Table of Contents
Disclaimer
Anything here on my blog, this article, and all the other one, are for education purpose. Any misuse of the information is at your own risk.
声明
此博客任何文章,包括本篇,仅供学习使用。任何滥用信息的行为,作者概不负责。
What Perter Kim (author of THP) suggests is to get your hands dirty. And the best way to get your hands dirty is to enroll in BugBounty programs.
Among the BugBounty sites he recommended, I took HackerOne. I registered and joined a program.
!!! IMPORTANT NOTE:
When doing BugBounty, be sure to read through thePolicyandScopesection pretty carefully to avoid any kind of trouble.
I've written two notes when reading TheHackerPlayBook-I, I think I have to take a beat and give the ideas from the book a try.
Passive Recon
Actually I bought TheHackerBook - III, because the book is too good, I don't want to miss out anything. So I bought the first and second too and start all over.
In the third book, Perter Kim set up a website that's for demonstration purpose, so anyone in the world is eligible to scan it. The domain is https://cyberspacekittens.com/.
So here I'm going to do some passive recon and see if I can find anything interesting.
BuiltWith
First, I want to look at the tech stack of the website. I go to builtwith.com.
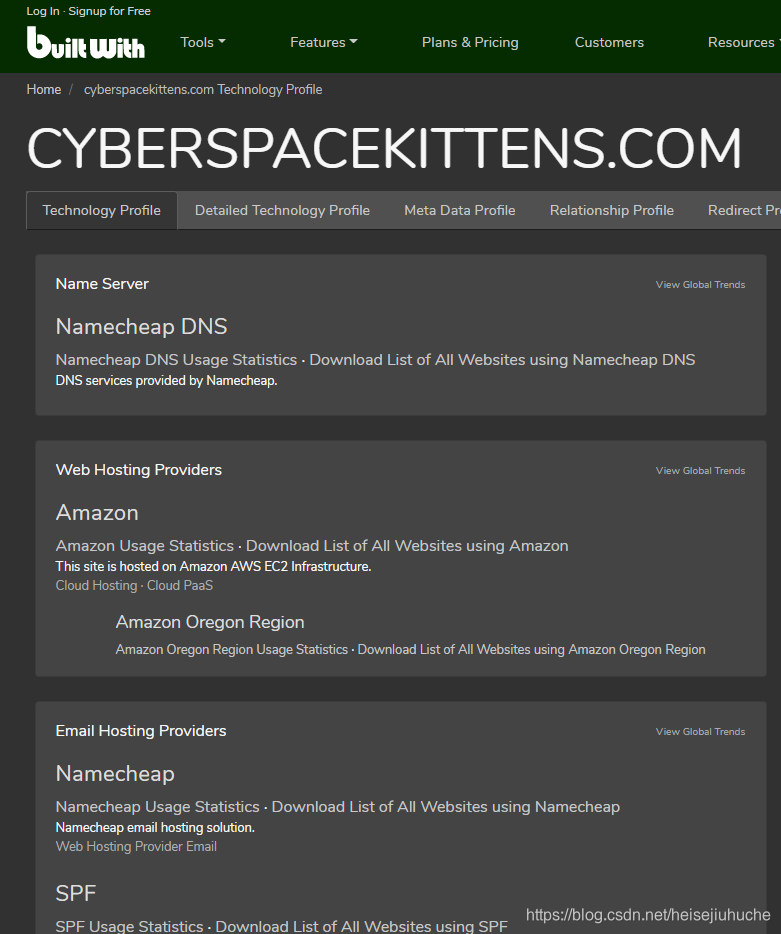
It lists a lot of infos, if the website is cloud based, web server tech, version and more.
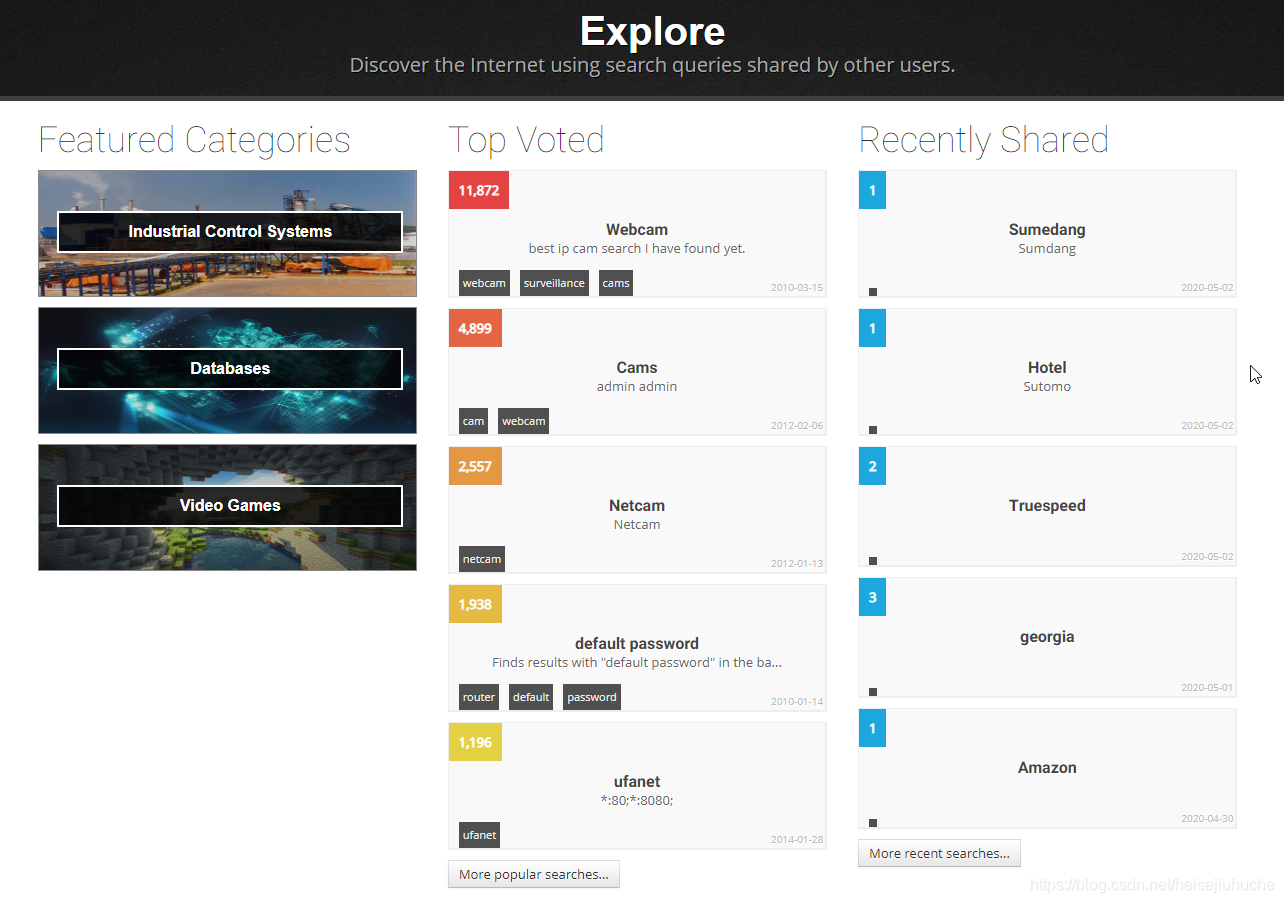
Shodan.io
Go to the website and go to Explore page, here is the top things that you can find that's most veted. The major thing to play on shodan is the surveillance web cameras that's misconfigured.
And like google, shodan supports filters.
Hers is a link to all the filters on shodan.
Let's play around with some of them.
OK, another warning here.
DO NOT scan any domain or ip that you are not authorized.
注意:
不要扫描任何你没有被授权的域名或者IP。
我还没有查看过相关法律,不知道你这样做会带来什么危害。
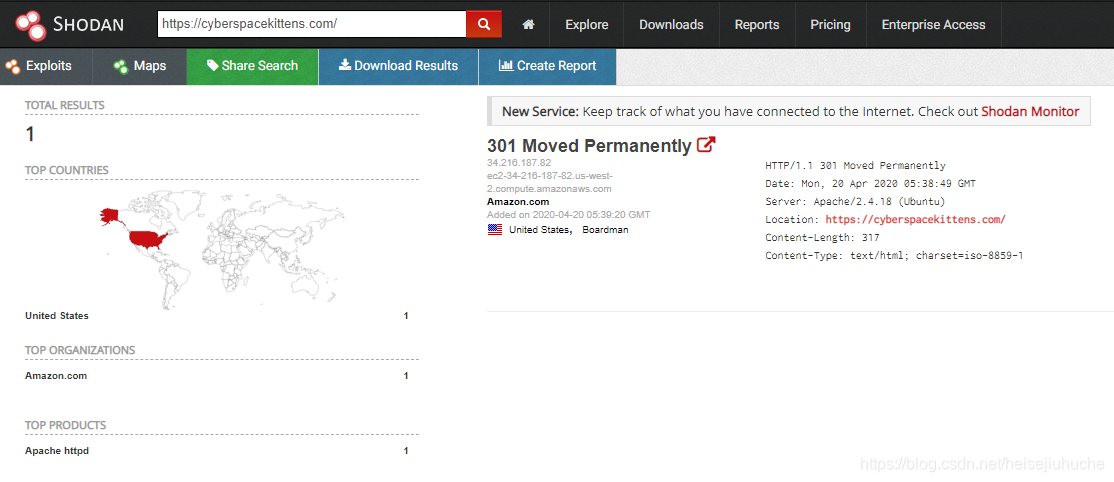
Open the 301 Moved Permanently, we can see more detailed info about the site. What ports are open, what services are running, the IP address of the server, and most importantly, the vulnerabilities if they are so obvious.
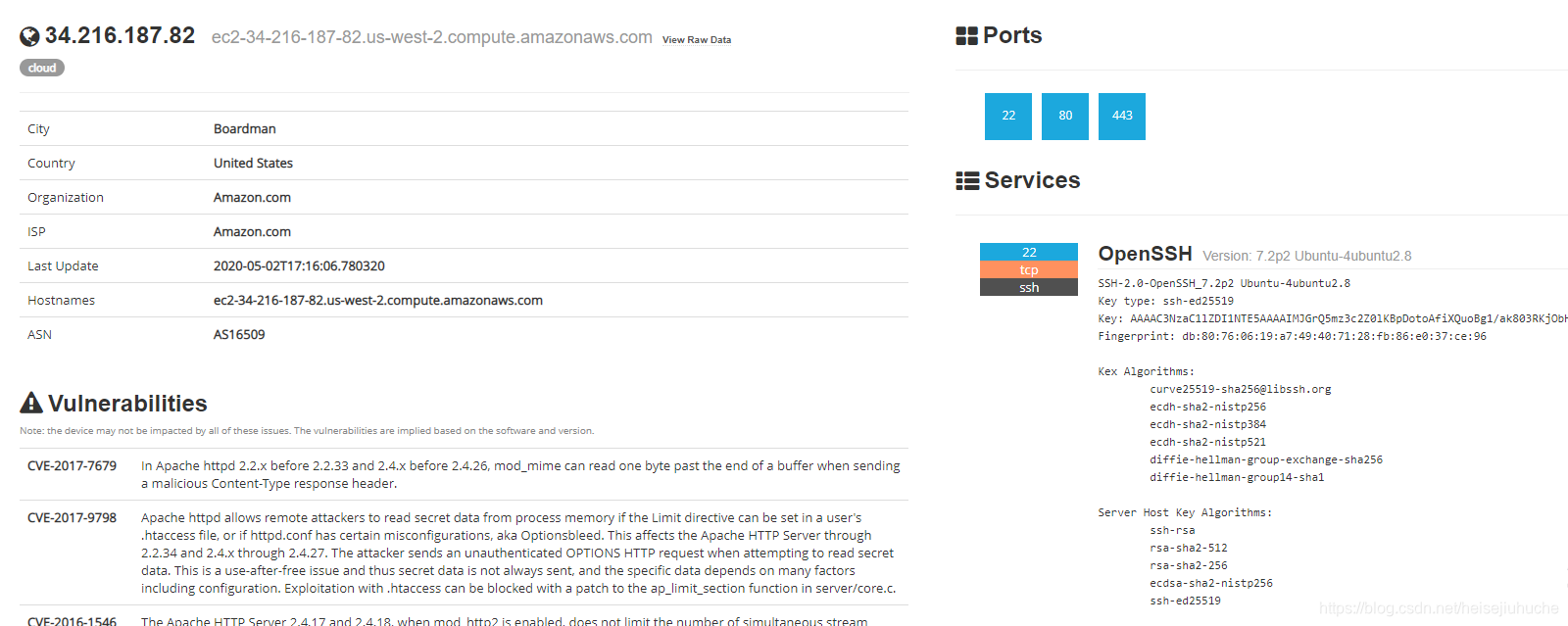
The banner of each service is very detailed. Feel free to scan https://cyberspacekittens.com/ yourself.
Censys.io
Basic overview of the websites ports and services at shodan.io. What if now I want to gethering some detailed info about the services through passive scan. We can go to censys.io.
I grabbed the IP of cyberspacekittens in shodan.io, and in the Search IPv4, I got the following result.
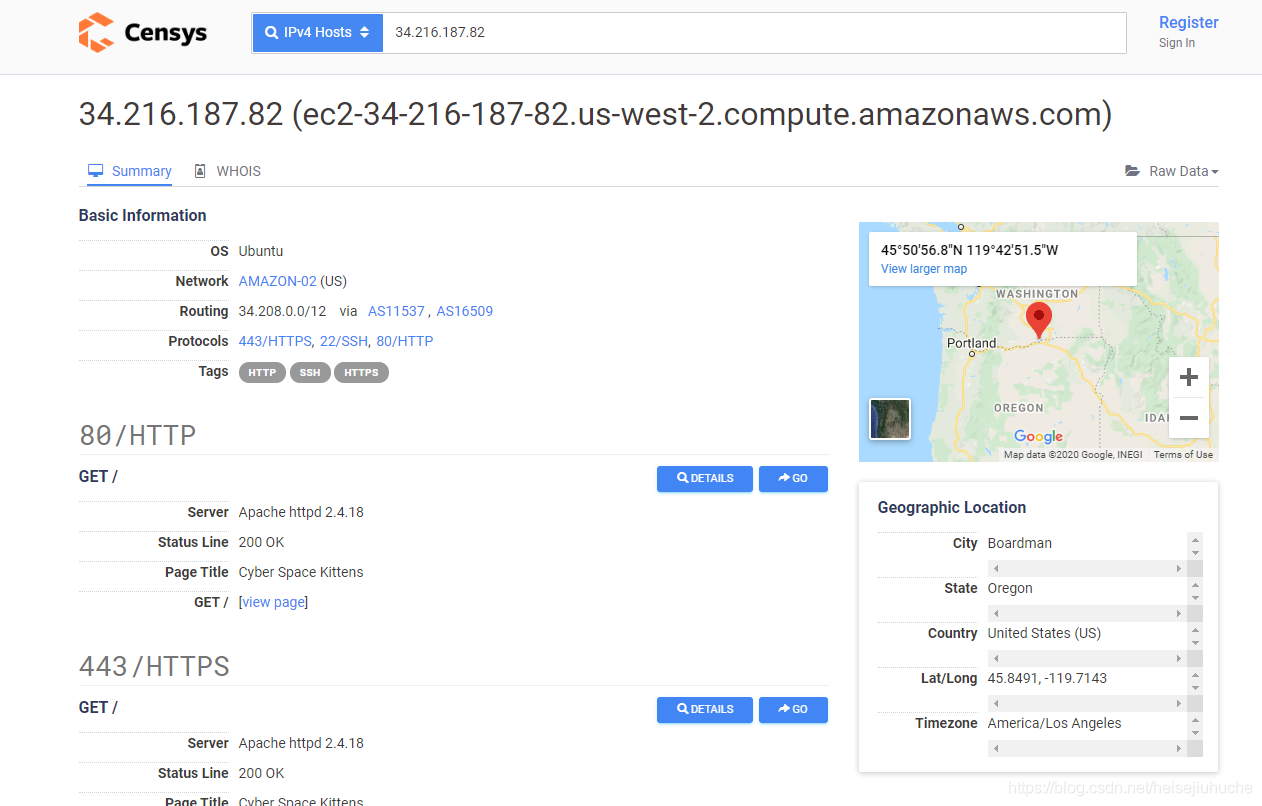
And see the detail button, I can click it and see a whole lot more info than shodan.
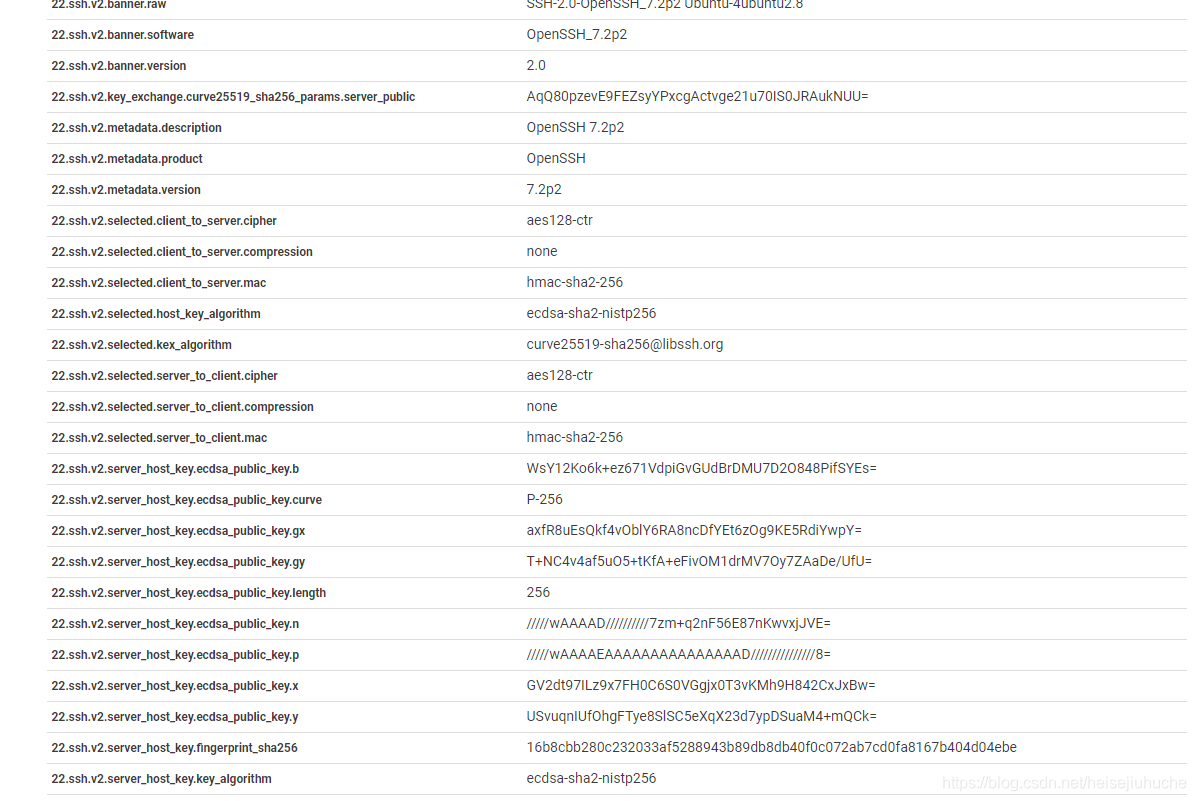
Feel free to poke around by yourself.
Hunter.io
Now, I want to see if I can get any emails from that domain.
I go to hunter.io, and this is what I found.
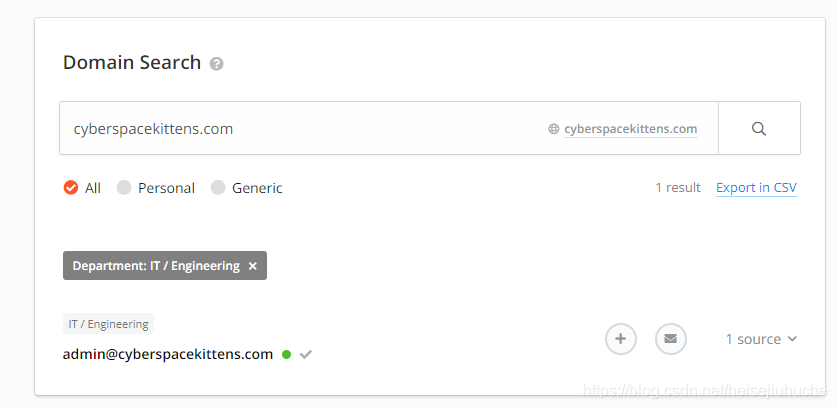
The website is for demonstration purpose so there's not much going on here. But I do find an email address here.
Anything like email addresses or usernames are considered sensitive informations, which may lead to system compromise.
Let's do a tesla.com, cause it's in BugBounty program, it shouldn't be an issue.
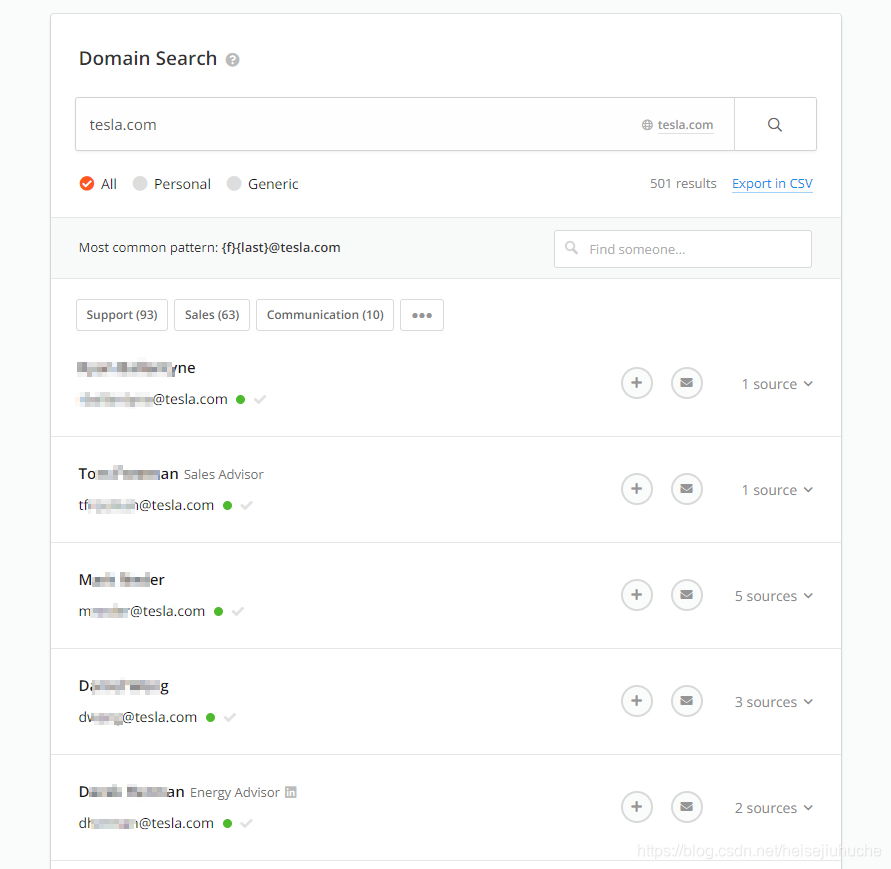
The picture contains only a few email addresses. You can see the people's full name, his email, and his department. Lots of info for social engineering.
Summary
I can find infos about os info, technology, open ports, open services, location, ip, emails, employee names and even vulnerabilities without a bit an active scan of the system. These websites offers so much for me to begin my first step in reconnaissance.
More to come.