Group Background
ALLANITE is suspected to be a Russian threat focused in espionage activities. Its main targets are electric utility sectors within United States and United Kingdom. The group hasn't exhibited disruptive or destructive abilities yet. They remain present in industry control systems and to gain persistence. It's techniques resembles that of other groups like Dragonfly. It's iconic campaign is dubbed as Palmetto Fusion. More details can be found here.
Recent Documented Time
2017.
Malware and Techniques Involved
Allanite conducts malware-less operations and rely on legitimate and available tools on windows operating system. Although, other techniques are also involved during the campaign against targets in the energy industry.
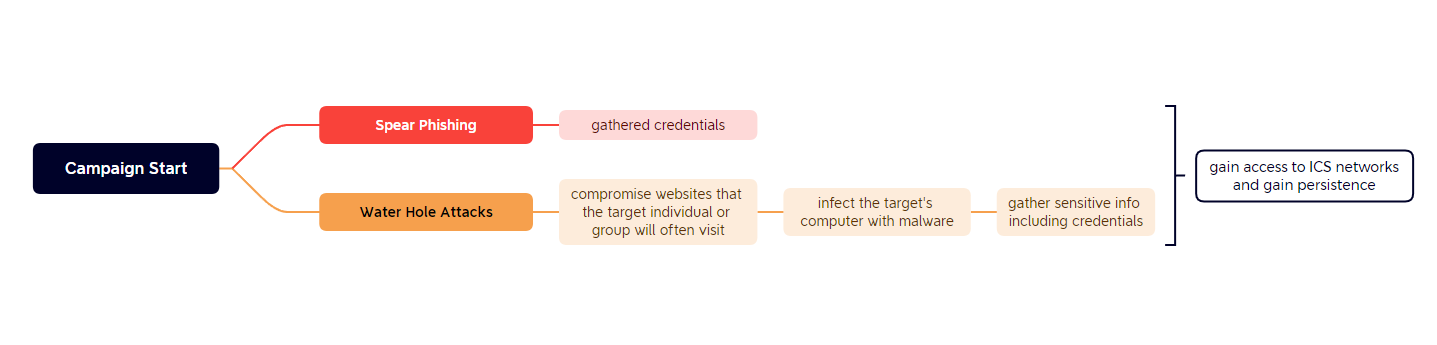
Spear Phishing
During the campaign, Allanite will constantly use spear phishing technique to gather user credentials for later use, which will grant them access to ICS systems in energy sector environments.
Watering Hole Attack
Besides spear phishing, Allanite also carried out watering hole attacks to infect target user's computer and gain access to sensitive information.
Watering hole attacks are hard to detect since it will compromise a site which the target user or group will often visit. It is nearly impossible to trace down such kind of compromised site to stop the attack from taking place.
The individual or group visits the compromised website, then the malicious code will run on the target's computer and connect back to attackers machine.
More about watering hole attack here.
Campaign Mind Map
References
- https://attack.mitre.org/groups/G1000/
- https://www.dragos.com/threat/allanite/
- https://certstation.com/blog/allanite-group-chooses-ics-networks-at-electric-services-in-usa-uk/
- https://www.techtarget.com/searchsecurity/definition/watering-hole-attack
- https://www.washingtonpost.com/world/national-security/us-officials-say-russian-government-hackers-have-penetrated-energy-and-nuclear-company-business-networks/2017/07/08/bbfde9a2-638b-11e7-8adc-fea80e32bf47_story.html?noredirect=on&utm_term=.cd1d17d6a118