Obedient Cat
Overview
- Category: General Skills
- Points: 5
Solution
First download the file, it has no extension associated.

Let's see what kind of file it is using file command.
file flagIt's ascii.

cat to obtain flag.
cat flag
flag: picoCTF{s4n1ty_v3r1f13d_28e8376d}
Mod 26
Overview
- Category: Cryptography
- Points: 10
Solution
Basic rot 13 cipher. Go to https://rot13.com/ to obtain flag.
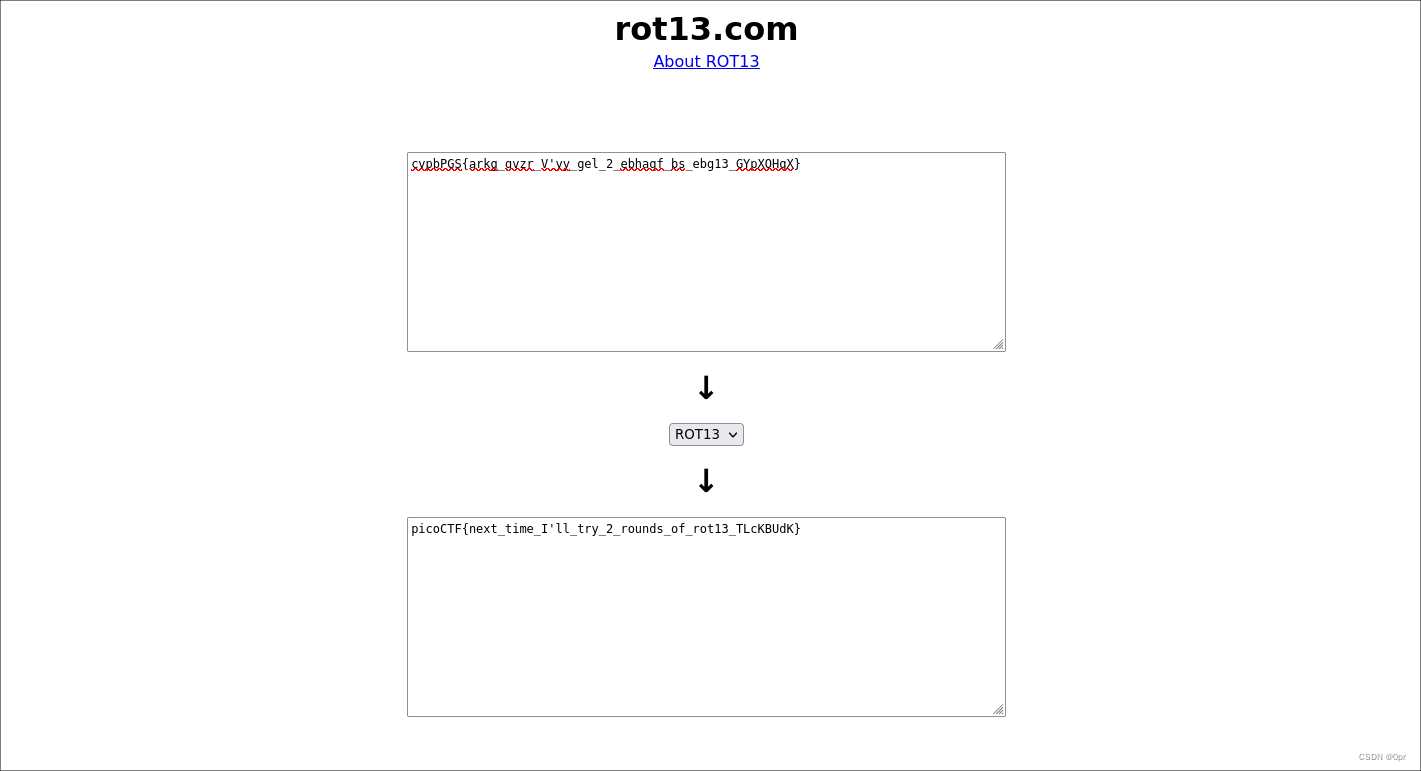
flag: picoCTF{next_time_I'll_try_2_rounds_of_rot13_TLcKBUdK}
Python Wrangling
Overview
- Category: General Skills
- Points: 10
Solution
First download all three files.

After checking the python code, it looks like the script can decode the encoded flag using the password file.
Run the python script as there's usage string.

Pretty straight forward now.
# copy the password string
cat pw.txt
# run the script and paste in the password
python ende.py -d flag.txt.en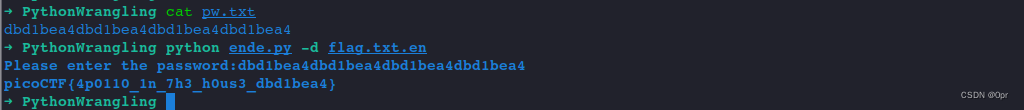
flag: picoCTF{4p0110_1n_7h3_h0us3_dbd1bea4}
Wave a flag
Overview
- Category: General Skills
- Points: 10
Solution
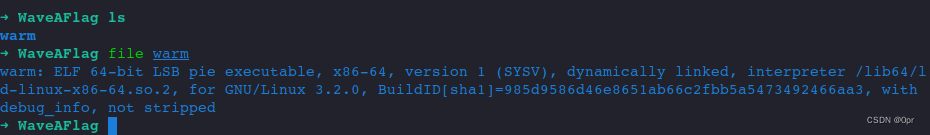
First download the file.
It's elf executable.
Run it.
chmod +x warm
./warm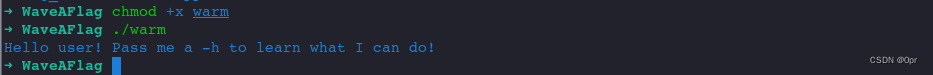
Looks like the flag should be in the help info.
./warm -h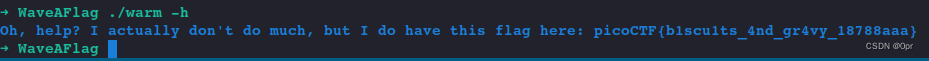
flag: picoCTF{b1scu1ts_4nd_gr4vy_18788aaa}
information
Overview
- Category: Forensics
- Points: 10
Solution
First download the file. It's a jpg file. Must use one of the image meta data manipulation tools to check the file.
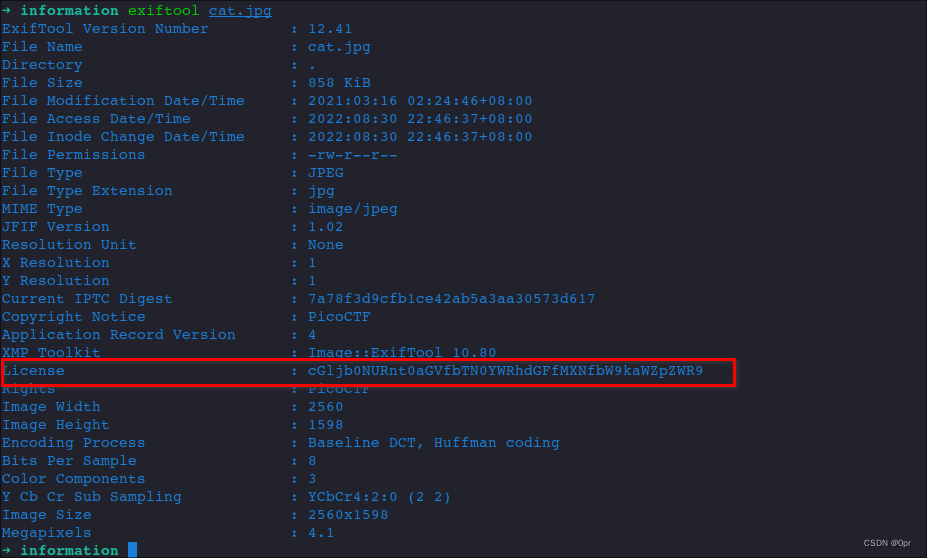
exiftool cat.jpgThis License file looks suspicious. Might be base64 encoded string.
Decode it.
echo -n 'cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9' | base64 -d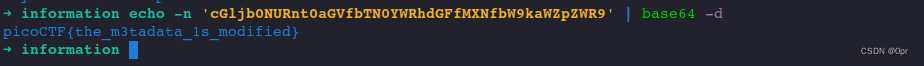
flag: picoCTF{the_m3tadata_1s_modified}
Nice netcat...
Overview
- Category: General Skills
- Points: 15
Solution
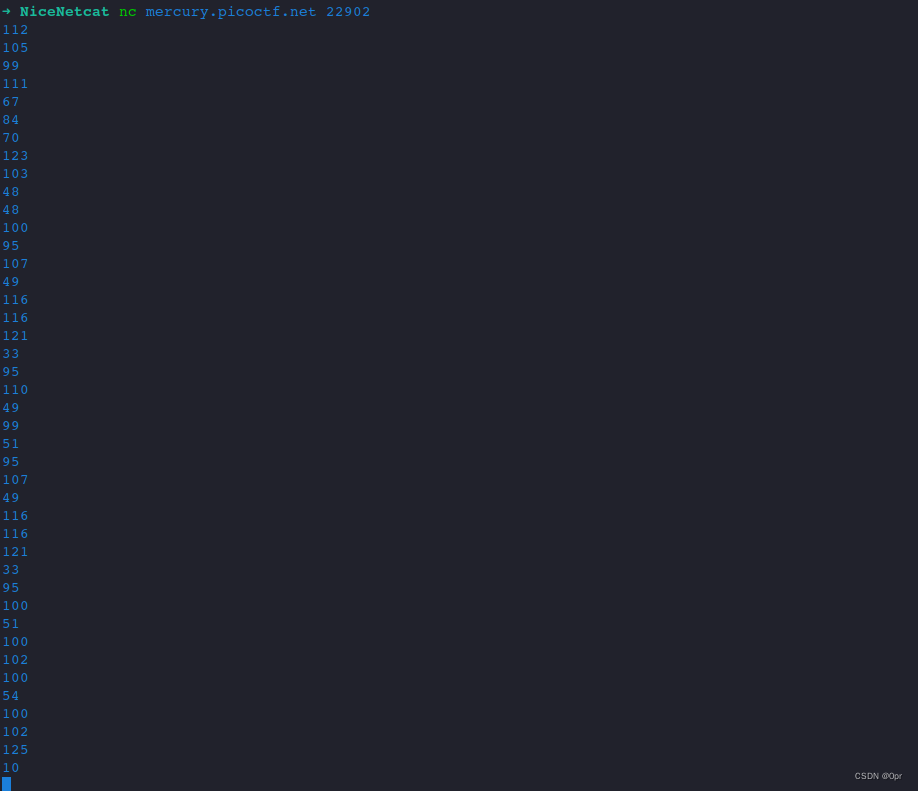
Connect to the server using the command and see.
nc mercury.picoctf.net 22902Looks like ascii numbers. Do a string manipulation and convert them to letters.
Concatenate into one line. Good that they have extra space for us.
nc mercury.picoctf.net 22902 | tr -d '\n' | tee flag.ascii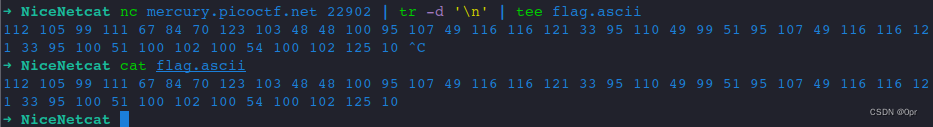
Go to https://codebeautify.org/ascii-to-text to get the flag.
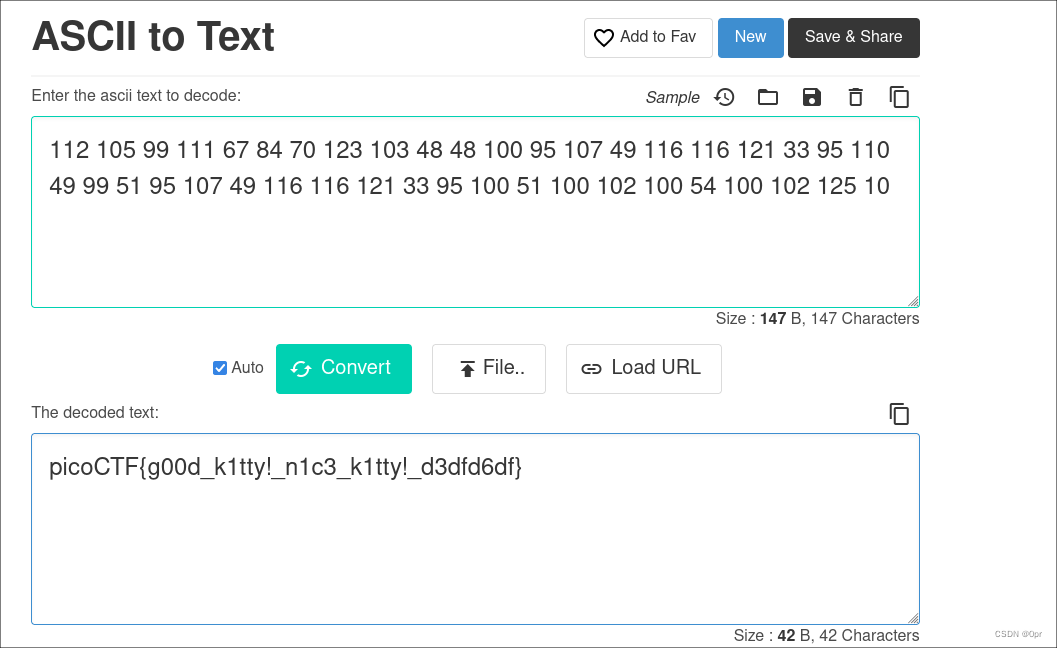
flag: picoCTF{g00d_k1tty!_n1c3_k1tty!_d3dfd6df}
Summary
Day 1 out. Pretty straight forward and easy, hence warm up. Tomorrow we're going to be facing harder ones involving reverse engineering problems. Game's on.