Lab Intro
A local police department has hired you to pentest their website. They had a new website created by a web development company and they want to make sure that everything is secure and in order.
In this lab you will practice with Burp Suite, configuring the scope of the engagement, intercepting the communications with a webserver and spidering a target web application. You can access the target web application at the following address 10.100.13.5.
Goal
The goal of this lab is to test the given web application in order to find a hidden path that contains a restricted area. Once the hidden path is discovered, your goal will be to bypass the authentication exploiting a "feature" left over by the developers while "debugging" the area.
Solution
Burp
Examine the webapp. The home page is like this.
 Click around, try to build the site map. And add the host to scope per request of the task.
Click around, try to build the site map. And add the host to scope per request of the task.
Right click on the domain and select add to scope.
 Click on the filter and choose
Click on the filter and choose show only in scope.
 Let's check if there's a
Let's check if there's a robots.txt file.
Yes, there is.
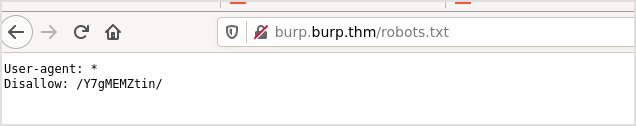 Let's visit the path in the file. It's a login page. And the backend is php.
Let's visit the path in the file. It's a login page. And the backend is php.
 Try to login as admin:admin shows error.
Try to login as admin:admin shows error.
 There's nothing in the home page's source.
There's nothing in the home page's source.
Let's use repeater to check the login page again. Try to login, and intercept the request.
 Press
Press Ctrl + R to send the request to repeater.
 After sending a request to the server, I got a message on the bottom of the response.
After sending a request to the server, I got a message on the bottom of the response.
 Requesting with the parameter shows the restricted area on the server.
Requesting with the parameter shows the restricted area on the server.

ZAP
Set ZAP to intercept requests by clicking the dot.
 Make a request.
Make a request.
 Now, the target is in sites panel.
Now, the target is in sites panel.
 Let's right click the site and select
Let's right click the site and select Attack -> Spider. Click Start Scan.
 After a while, the path has been discovered.
After a while, the path has been discovered.

In Messages tab, find the URL and open it in browser.
 The login page shows up.
The login page shows up.
 ZAP hub provides live view of the requests and response. But it's not too user friendly cause there's no syntax highlighting.
ZAP hub provides live view of the requests and response. But it's not too user friendly cause there's no syntax highlighting.

Back to ZAP, I got the same message.
 Task completed.
Task completed.
Time elapsed, one and half hours.